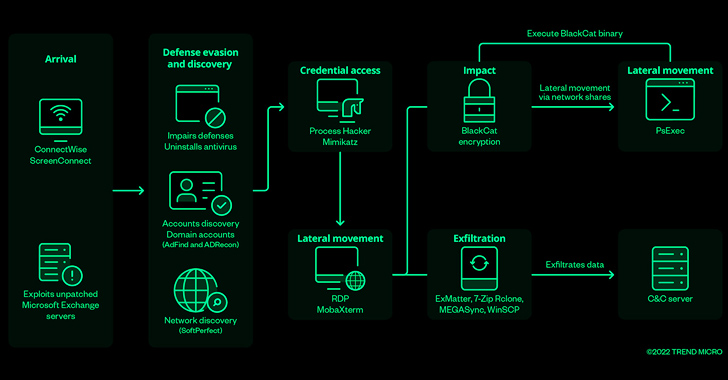
The threat actors behind BlackCat ransomware have come up with an improved variant that prioritizes speed and stealth in an attempt to bypass security guardrails and achieve their goals.
The new version, dubbed Sphynx and announced in February 2023, packs a “number of updated capabilities that strengthen the group’s efforts to evade detection,” IBM Security X-Force said in a new analysis.
The “product” update was first highlighted by vx-underground in April 2023. Trend Micro, last month, detailed a Linux version of Sphynx that’s “focused primarily on its encryption routine.”
BlackCat, also called ALPHV and Noberus, is the first Rust-language-based ransomware strain spotted in the wild. Active since November 2021, it has emerged as a formidable ransomware actor, victimizing more than 350 targets as of May 2023.
The group, like other ransomware-as-a-service (RaaS) offerings, is known to operate a double extortion scheme, deploying custom data exfiltration tools like ExMatter to siphon sensitive data prior to encryption.
Initial access to targeted networks is typically obtained through a network of actors called initial access brokers (IABs), who employ off-the-shelf information stealer malware to harvest legitimate credentials.
BlackCat has also been observed to share overlaps with the now-defunct BlackMatter ransomware family, according to Cisco Talos and Kaspersky.
The findings provide a window into the ever-evolving cybercrime ecosystem wherein threat actors enhance their tooling and tradecraft to increase the likelihood of a successful compromise, not to mention thwart detection and evade analysis.
Specifically, the Sphynx version of BlackCat incorporates junk code and encrypted strings, while also reworking the command line arguments passed to the binary.
Sphynx also incorporates a loader to decrypt the ransomware payload that, upon execution, performs network discovery activities to hunt for additional systems, deletes volume shadow copies, encrypts files, and finally drops the ransom note.
? Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
Despite law enforcement campaigns against cybercrime and ransomware groups, the continuous shift in tactics is proof that BlackCat remains an active threat to organizations and has “no signs of winding down.”
| Source: WithSecure |
Finnish cybersecurity firm WithSecure, in a recent research, described how the illicit financial proceeds associated with ransomware attacks have led to a “professionalization of cyber crime” and the advent of new supporting underground services.
“Many major ransomware groups are operating a service provider or RaaS model, where they supply tooling and expertise to affiliates, and in return take a cut of the profits,” the company said.
“These profits have driven the rapid development of a service industry, providing all the tools and services that an up and coming threat group could need, and thanks to cryptocurrency and dark web routing services the many different groups involved are able to anonymously buy and sell services, and access their profits.”










