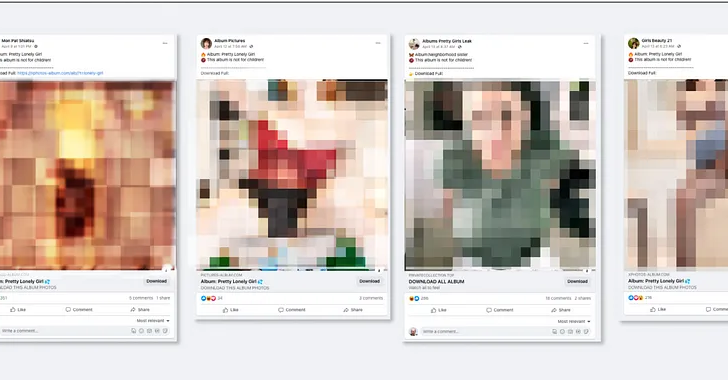
A Vietnamese threat actor has been attributed as behind a “malverposting” campaign on social media platforms to infect over 500,000 devices worldwide over the past three months to deliver variants of information stealers such as S1deload Stealer and SYS01stealer.
Malverposting refers to the use of promoted social media posts on services like Facebook and Twitter to mass propagate malicious software and other security threats. The idea is to reach a broader audience by paying for ads to “amplify” their posts.
According to Guardio Labs, such attacks commence with the adversary creating new business profiles and hijacking already popular accounts to serve ads that claim to offer free adult-rated photo album downloads.
Within these ZIP archive files are purported images that are actually executable files, which, when clicked, activate the infection chain and ultimately deploy the stealer malware to siphon session cookies, account data, and other information.
The attack chain is highly effective as it creates a “vicious circle” wherein the information plundered using the stealer is used to create an ever-expanding army of hijacked Facebook bot accounts that are then used to push more sponsored posts, effectively scaling the scheme further.
To slip under the radar of Facebook, the threat actor has been found to pass off the newly generated business profile pages as photographer accounts. A majority of the infections have been reported in Australia, Canada, India, the U.K., and the U.S.
The method through which the PHP-based stealer is deployed is said to be constantly evolving to incorporate more detection evasion features, suggesting that the threat actor behind the campaign is actively refining and retooling their tactics in response to public disclosures.
“The malicious payload is quite sophisticated and varies all the time, introducing new evasive techniques,” Guardio Labs security researcher Nati Tal said.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
The findings come as Group-IB revealed details of an ongoing phishing operation that’s aimed at Facebook users by tricking them to enter their credentials on fake copycat sites designed to steal their account credentials and take over the profiles.
In a related development, Malwarebytes unearthed a malvertising campaign that has been found to trick users searching for games and food recipes on Google to serve malicious ads that redirect them to fake websites created on Weebly with the goal of conducting a tech support scam.




