A number of phishing campaigns are leveraging the decentralized Interplanetary Filesystem (IPFS) network to host malware, phishing kit infrastructure, and facilitate other attacks.
“Multiple malware families are currently being hosted within IPFS and retrieved during the initial stages of malware attacks,” Cisco Talos researcher Edmund Brumaghin said in an analysis shared with The Hacker News.
The research mirrors similar findings from Trustwave SpiderLabs in July 2022, which found more than 3,000 emails containing IPFS phishing URLs as an attack vector, calling IPFS the new “hotbed” for hosting phishing sites.
IPFS as a technology is both resilient to censorship and takedowns, making it a double-edged sword. Underlying it is a peer-to-peer (P2P) network which replicates content across all participating nodes so that even if content is removed from one machine, requests for the resources can still be served via other systems.
This also makes it ripe for abuse by bad actors looking to host malware that can resist law enforcement attempts at disrupting their attack infrastructure, like seen in the case of Emotet last year.
“IPFS is currently being abused by a variety of threat actors who are using it to host malicious contents as part of phishing and malware distribution campaigns,” Brumaghin previously told The Hacker News in August 2022.
This includes Dark Utilities, a command-and-control (C2) framework that’s advertised as a way for adversaries to avail remote system access, DDoS capabilities, and cryptocurrency mining, with the payload binaries provided by the platform hosted in IPFS.
Furthermore, IPFS has been put to use to serve rogue landing pages as part of phishing campaigns orchestrated to steal credentials and distribute a wide range of malware comprising Agent Tesla, reverse shells, data wiper, and an information stealer called Hannabi Grabber.
In one malspam delivery chain detailed by Talos, an email purporting to be from a Turkish financial institution urged the recipient to open a ZIP file attachment that, when launched, worked as a downloader to retrieve an obfuscated version of Agent Tesla hosted within the IPFS network.
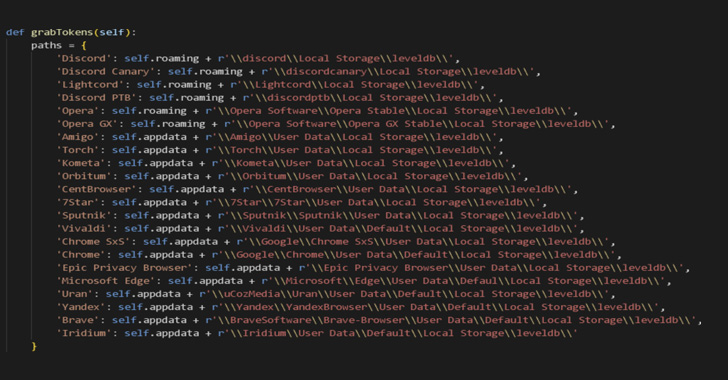
The destructive malware, for its part, takes the form of a batch file that deletes backups and recursively purges all directory contents. Hannabi Grabber is a Python-based malware that gathers sensitive information from the infected host, such as browser data and screenshots, and transmits it via a Discord Webhook.
The latest development points to the growing use by attackers of legitimate offerings such as Discord, Slack, Telegram, Dropbox, Google Drive, AWS, and several others to host malicious content or to direct users to it, making phishing one of the lucrative primary initial access vectors.
“We expect this activity to continue to increase as more threat actors recognize that IPFS can be used to facilitate bulletproof hosting, is resilient against content moderation and law enforcement activities, and introduces problems for organizations attempting to detect and defend against attacks that may leverage the IPFS network,” Brumaghin said.





