admin
September 22, 2023
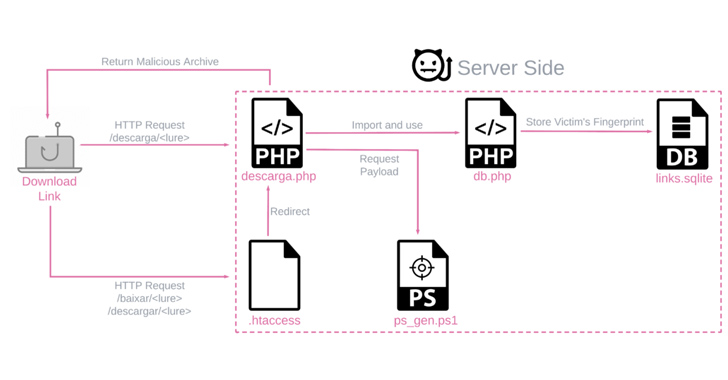
An active malware campaign targeting Latin America is dispensing a new variant of a banking trojan called BBTok,...
admin
September 22, 2023
Thorough, independent tests are a vital resource for analyzing provider’s capabilities to guard against increasingly sophisticated threats...
admin
September 22, 2023
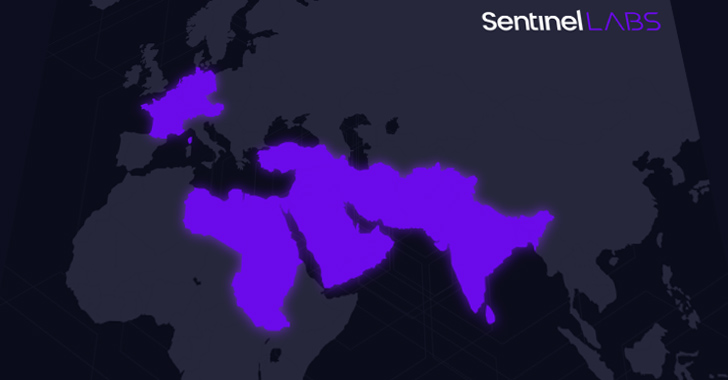
Israeli organizations were targeted as part of two different campaigns orchestrated by the Iranian nation-state actor known...
admin
September 22, 2023
Atlassian and the Internet Systems Consortium (ISC) have disclosed several security flaws impacting their products that could...
admin
September 22, 2023
Apple has released yet another round of security patches to address three actively exploited zero-day flaws impacting...
admin
September 21, 2023
A previously undocumented threat actor dubbed Sandman has been attributed to a set of cyber attacks targeting telecommunic koation...
admin
September 21, 2023
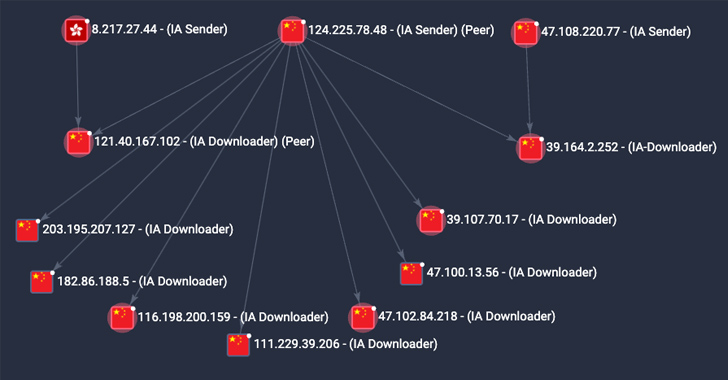
The peer-to-peer (P2) worm known as P2PInfect has witnessed a surge in activity since late August 2023, witnessing a...
admin
September 21, 2023
A malicious actor released a fake proof-of-concept (PoC) exploit for a recently disclosed WinRAR vulnerability on GitHub...
admin
September 21, 2023
Security teams are familiar with threats emanating from third-party applications that employees add to improve their productivity....
admin
September 21, 2023
China's Ministry of State Security (MSS) has accused the U.S. of breaking into Huawei's servers, stealing critical...
admin
September 21, 2023
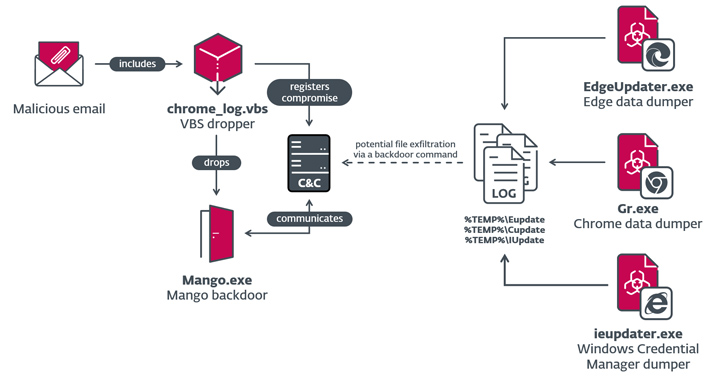
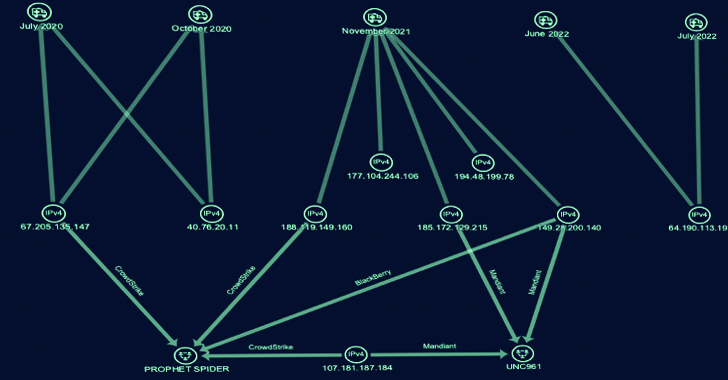
A financially motivated threat actor has been outed as an initial access broker (IAB) that sells access...
admin
September 21, 2023
The maintainers of Free Download Manager (FDM) have acknowledged a security incident dating back to 2020 that...
admin
September 20, 2023
Finnish law enforcement authorities have announced the takedown of PIILOPUOTI, a dark web marketplace that specialized in...
admin
September 20, 2023
Multiple security flaws have been disclosed in the Nagios XI network monitoring software that could result in...
admin
September 20, 2023
Well, you shouldn’t. It may already be hiding vulnerabilities.
It's the modular nature of modern web applications that...
admin
September 20, 2023
Cybersecurity researchers have discovered a fresh batch of malicious packages in the npm package registry that are...
admin
September 20, 2023
Chinese-language speakers have been increasingly targeted as part of multiple email phishing campaigns that aim to distribute...
admin
September 20, 2023
Encrypted messaging app Signal has announced an update to the Signal Protocol to add support for quantum...
admin
September 20, 2023
GitLab has shipped security patches to resolve a critical flaw that allows an attacker to run pipelines...
admin
September 20, 2023
Cybersecurity company Trend Micro has released patches and hotfixes to address a critical security flaw in Apex One and...