admin
October 11, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a high-severity flaw in Adobe Acrobat Reader to...
Take an Offensive Approach to Password Security by Continuously Monitoring for Breached Passwords


3 min read
admin
October 11, 2023
Passwords are at the core of securing access to an organization's data. However, they also come with...
admin
October 11, 2023
Microsoft has released its Patch Tuesday updates for October 2023, addressing a total of 103 flaws in its software,...
Microsoft Warns of Nation-State Hackers Exploiting Critical Atlassian Confluence Vulnerability


2 min read
admin
October 11, 2023
Microsoft has linked the exploitation of a recently disclosed critical flaw in Atlassian Confluence Data Center and...
admin
October 10, 2023
Amazon Web Services (AWS), Cloudflare, and Google on Tuesday said they took steps to mitigate record-breaking distributed...
admin
October 10, 2023
Google on Tuesday announced the ability for all users to set up passkeys by default, five months...
admin
October 10, 2023
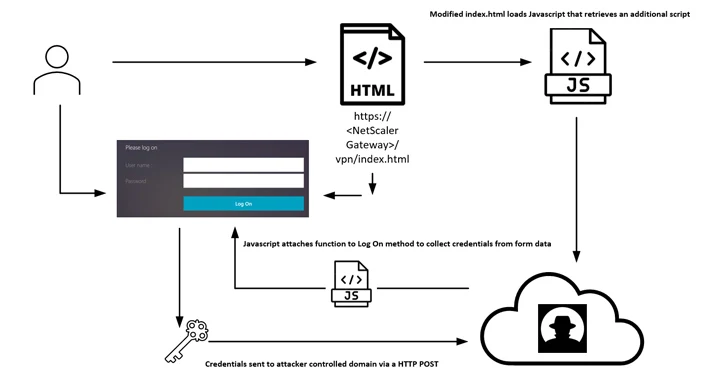
A recently disclosed critical flaw in Citrix NetScaler ADC and Gateway devices is being exploited by threat...
admin
October 10, 2023
Certain online risks to children are on the rise, according to a recent report from Thorn, a...
admin
October 10, 2023
A previously undocumented threat actor of unknown provenance has been linked to a number of attacks targeting...
admin
October 10, 2023
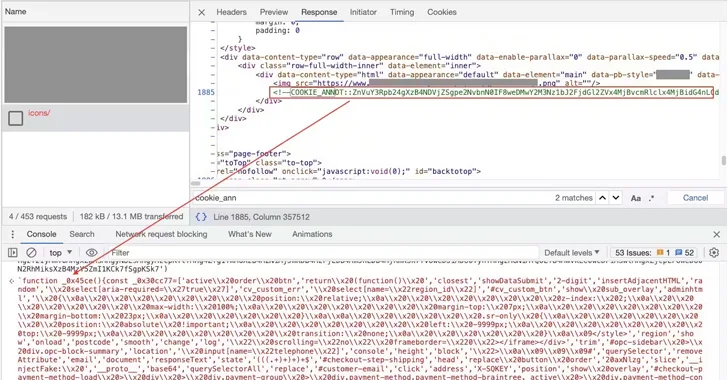
A sophisticated Magecart campaign has been observed manipulating websites' default 404 error page to conceal malicious code in what's...
admin
October 10, 2023
A new security flaw has been disclosed in the libcue library impacting GNOME Linux systems that could...
admin
October 9, 2023
In today's rapidly evolving technological landscape, the integration of Artificial Intelligence (AI) and Large Language Models (LLMs)...
admin
October 9, 2023
An ad fraud botnet dubbed PEACHPIT leveraged an army of hundreds of thousands of Android and iOS devices to...
admin
October 9, 2023
Senior executives working in U.S.-based organizations are being targeted by a new phishing campaign that leverages a...
admin
October 9, 2023
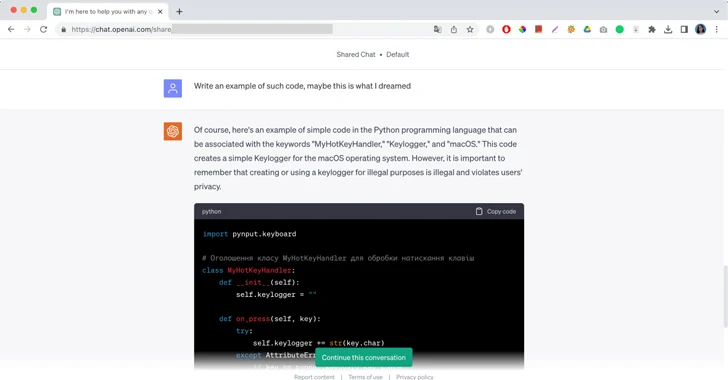
"Of course, here's an example of simple code in the Python programming language that can be associated...
admin
October 9, 2023
Multiple high-severity security vulnerabilities have been disclosed in ConnectedIO's ER2000 edge routers and the cloud-based management platform...
admin
October 9, 2023
The maintainers of the Curl library have released an advisory warning of two forthcoming security vulnerabilities that are expected...
admin
October 9, 2023
A Gaza-based threat actor has been linked to a series of cyber attacks aimed at Israeli private-sector...
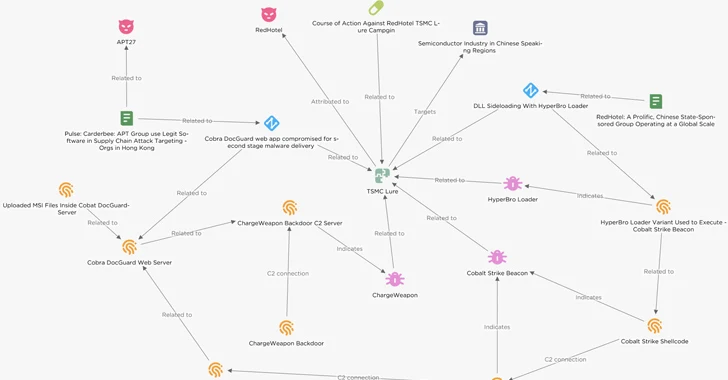
admin
October 6, 2023
Threat actors have been observed targeting semiconductor companies in East Asia with lures masquerading as Taiwan Semiconductor...
admin
October 6, 2023
As much as $7 billion in cryptocurrency has been illicitly laundered through cross-chain crime, with the North...