Employee offboarding is no one’s favorite task, yet it is a critical IT process that needs to be executed diligently and efficiently. That’s easier said than done, especially considering that IT organizations have less visibility and control over employees’ IT use than ever. Today, employees can easily adopt new cloud and SaaS applications whenever and wherever they want, and the old IT offboarding playbook of “disable AD account, forward email, recover and wipe device, and call it a day” is no longer enough.
Here, we’ll cover five of the most common pitfalls of IT offboarding in a SaaS-first world, along with advice on how to navigate around them.
Pitfall #1: Suspending or deleting the email account before completing other critical steps
It may seem logical to suspend or delete the employees’ Google Workspace or Microsoft 365 account as the first step in the offboarding process. However, this will make the account inaccessible to everyone, even admins, which could interfere with your ability to complete other offboarding tasks like transferring files and data.
Instead of suspending or deleting the account, you’ll want to revoke the former employee’s access to their email account by resetting their passwords and turning off any recovery methods the employee had set up, such as a secondary personal email address or mobile number.
Determining when to suspend or delete the employees’ email account will depend on internal protocol, and should be carefully completed only after confirming that access to all other critical resources, systems and data have been revoked or transferred to other employees. Typically, this will be the final step in the IT offboarding process.
Pitfall #2: Considering only what’s in IdP or SSO
One of the most common offboarding pitfalls is limiting the scope to only the sanctioned cloud and SaaS applications that are managed within your identity provider (IdP) or enterprise single sign-on system (SSO.) While it seems logical to design an offboarding process with a single identity kill-switch, the reality we all live with is that not everything is behind SSO, and by narrowing your scope, you risk overlooking all of the unsanctioned or “shadow” SaaS assets an employee introduced during their tenure. Such unsanctioned SaaS accounts are often created with a username and password, which can easily walk out the door on a Post-it note or be left abandoned and later compromised by a threat actor. To avoid this pitfall, start by opening the aperture of your IT offboarding to encompass all managed and unmanaged cloud and SaaS access.
So, how do you build a list of the unmanaged cloud and SaaS accounts for a departing employee? This can turn into the world’s worst scavenger hunt, with you having to cross-reference information from finance systems, your help desk ticketing platform, inquiries to application owners outside of IT, teammates of the departing employee, and more.
But don’t embark on that hunt yet, new solutions for SaaS management are emerging to make this process a whole lot easier.
Pitfall #3: Overlooking business-critical cloud and SaaS resources
It is easy to forget to transfer the ownership of critical resources like corporate social media accounts, root account ownership, and registered domains. This mistake can lead to business disruption or leave accounts orphaned and inaccessible. To ensure this doesn’t happen, IT organizations should be sure to identify and transfer ownership of any business-critical resources, automations, or integrations as an early step of the offboarding process.
Pitfall #4: Not involving the business owners of each SaaS application
The rapid rise of business-led IT means that more IT administration is happening outside of central IT. This means more people to engage in the offboarding process, including application business owners and business technologists who manage the budgets and licenses for their SaaS applications.
There are two key steps to simplifying this process: first, you have to know who the right people are to engage, which requires a robust SaaS management platform. Second, you need a way to streamline and even automate engagement with all stakeholders in order to effectively orchestrate the multitude of offboarding tasks that non-IT administrators must complete.
For example, before the departing employee’s account within a particular app is shut down, the application business owner may need to transfer ownership of data, integrations, or workflows to avoid disrupting the business. Additionally, the app owner may need to transfer any elevated permissions to a new user.
Pitfall #5: Overlooking app-to-app OAuth integrations
In most organizations today, a web of app-to-app OAuth integrations exists in order to automate data updates and tasks across apps. When employees leave the organization, revoking grants without careful review could lead to business disruption, and not revoking grants could lead to increased risk.
As a result, it’s important to review OAuth grants, work with application owners to identify any that need to be reinstated via a different account, and then revoke the grants issued by the departing employee’s accounts.
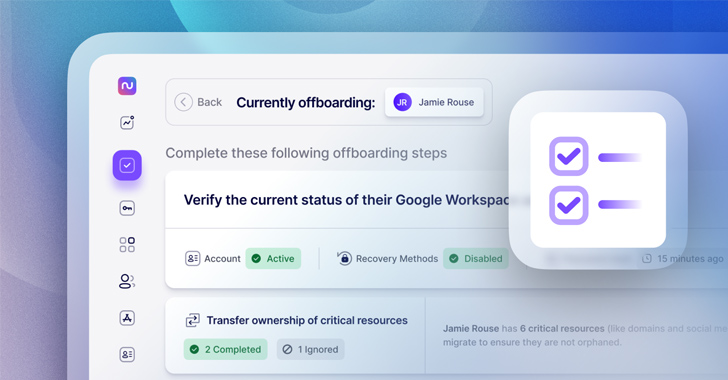
Automate SaaS offboarding with Nudge Security
IT offboarding is tedious, time-consuming and often incomplete. But, Nudge Security can make this process much easier.
Nudge Security continuously discovers and inventories all the SaaS and cloud applications your employees are using, including shadow IT, giving you a single source of truth for a departing users’ accounts, OAuth grants, and other critical resources. And, the built-in offboarding playbook automates up to 90% of manual tasks like resetting passwords, revoking OAuth grants, messaging application owners to transfer data and permissions, and more.
See how you can automate IT offboarding with Nudge Security.