admin
November 23, 2023
An active malware campaign is leveraging two zero-day vulnerabilities with remote code execution (RCE) functionality to rope...
admin
November 22, 2023
A new research has uncovered multiple vulnerabilities that could be exploited to bypass Windows Hello authentication on Dell Inspiron...
admin
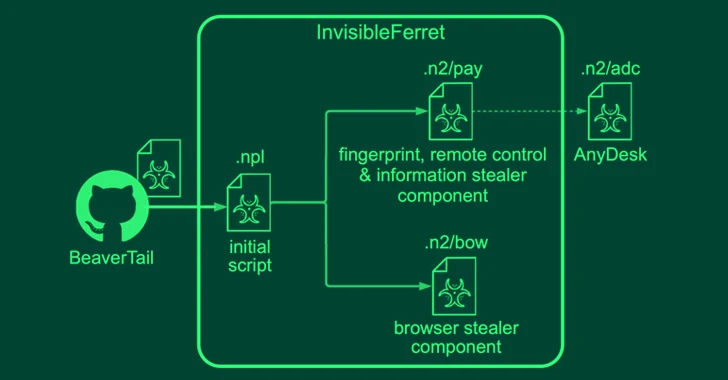
November 22, 2023
North Korean threat actors have been linked to two campaigns in which they masquerade as both job...
admin
November 22, 2023
Ambitious Employees Tout New AI Tools, Ignore Serious SaaS Security RisksLike the SaaS shadow IT of the past, AI...
admin
November 22, 2023
The macOS information stealer known as Atomic is now being delivered to target via a bogus web...
admin
November 22, 2023
Multiple threat actors, including LockBit ransomware affiliates, are actively exploiting a recently disclosed critical security flaw in Citrix NetScaler...
admin
November 21, 2023
A new variant of the Agent Tesla malware has been observed delivered via a lure file with the ZPAQ compression...
admin
November 21, 2023
The ransomware strain known as Play is now being offered to other threat actors "as a service," new evidence...
admin
November 21, 2023
Phishing attacks are steadily becoming more sophisticated, with cybercriminals investing in new ways of deceiving victims into...
admin
November 21, 2023
The Kinsing threat actors are actively exploiting a critical security flaw in vulnerable Apache ActiveMQ servers to infect Linux...
admin
November 21, 2023
Android smartphone users in India are the target of a new malware campaign that employs social engineering...
admin
November 21, 2023
The China-linked Mustang Panda actor has been linked to a cyber attack targeting a Philippines government entity...
admin
November 20, 2023
Threat actors are targeting the education, government and business services sectors with a remote access trojan called NetSupport...
admin
November 20, 2023
In this article, we will provide a brief overview of Silverfort's platform, the first (and currently only)...
admin
November 20, 2023
Phishing campaigns delivering malware families such as DarkGate and PikaBot are following the same tactics previously used...
admin
November 20, 2023
Today’s security leaders must manage a constantly evolving attack surface and a dynamic threat environment due to...
admin
November 20, 2023
The stealer malware known as LummaC2 (aka Lumma Stealer) now features a new anti-sandbox technique that leverages the mathematical...
admin
November 20, 2023
Bitcoin wallets created between 2011 and 2015 are susceptible to a new kind of exploit called Randstorm that makes...
admin
November 20, 2023
An Indian hack-for-hire group targeted the U.S., China, Myanmar, Pakistan, Kuwait, and other countries as part of...
admin
November 18, 2023
The threat actors behind the 8Base ransomware are leveraging a variant of the Phobos ransomware to conduct their financially...