admin
December 7, 2023
Unspecified governments have demanded mobile push notification records from Apple and Google users to pursue people of...
admin
December 7, 2023
A previously unknown Linux remote access trojan called Krasue has been observed targeting telecom companies in Thailand...
admin
December 6, 2023
Threat actors can take advantage of Amazon Web Services Security Token Service (AWS STS) as a way...
admin
December 6, 2023
Compromising the browser is a high-return target for adversaries. Browser extensions, which are small software modules that...
admin
December 6, 2023
A collection of 21 security flaws have been discovered in Sierra Wireless AirLink cellular routers and open-source...
admin
December 6, 2023
In an increasingly complex and fast-paced digital landscape, organizations strive to protect themselves from various security threats....
admin
December 6, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned of active exploitation of a high-severity Adobe ColdFusion vulnerability by...
admin
December 6, 2023
Atlassian has released software fixes to address four critical flaws in its software that, if successfully exploited, could result...
admin
December 6, 2023
Chipmaker Qualcomm has released more information about three high-severity security flaws that it said came under "limited,...
admin
December 5, 2023
The Russia-linked influence operation called Doppelganger has targeted Ukrainian, U.S., and German audiences through a combination of...
admin
December 5, 2023
A new "post-exploitation tampering technique" can be abused by malicious actors to visually deceive a target into...
admin
December 5, 2023
Microsoft Copilot has been called one of the most powerful productivity tools on the planet.
Copilot is an...
admin
December 5, 2023
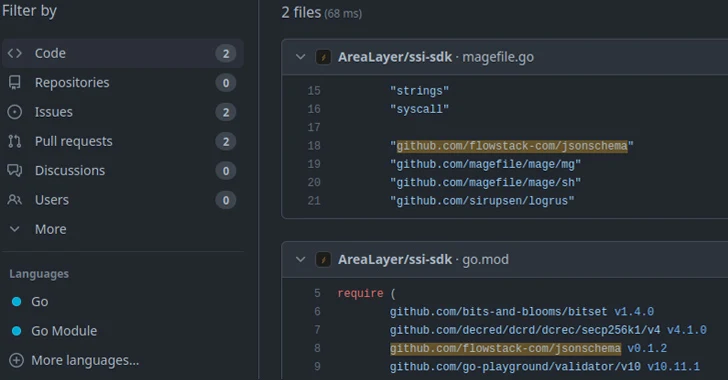
New research has found that over 15,000 Go module repositories on GitHub are vulnerable to an attack...
admin
December 5, 2023
A previously undocumented threat actor has been linked to a cyber attack targeting an aerospace organization in...
admin
December 5, 2023
Microsoft on Monday said it detected Kremlin-backed nation-state activity exploiting a now-patched critical security flaw in its...
admin
December 4, 2023
New research has unearthed multiple novel attacks that break Bluetooth Classic's forward secrecy and future secrecy guarantees,...
admin
December 4, 2023
As work ebbs with the typical end-of-year slowdown, now is a good time to review user roles...
admin
December 4, 2023
Cybersecurity researchers have discovered a new variant of an emerging botnet called P2PInfect that's capable of targeting routers and...
admin
December 4, 2023
The Unified Extensible Firmware Interface (UEFI) code from various independent firmware/BIOS vendors (IBVs) has been found vulnerable...
admin
December 4, 2023
Microsoft has warned of a new wave of CACTUS ransomware attacks that leverage malvertising lures to deploy...