admin
January 15, 2024
Cybersecurity researchers have disclosed a security flaw in the Opera web browser for Microsoft Windows and Apple...
admin
January 15, 2024
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half...
admin
January 15, 2024
Multiple security vulnerabilities have been disclosed in Bosch BCC100 thermostats and Rexroth NXA015S-36V-B smart nutrunners that, if...
admin
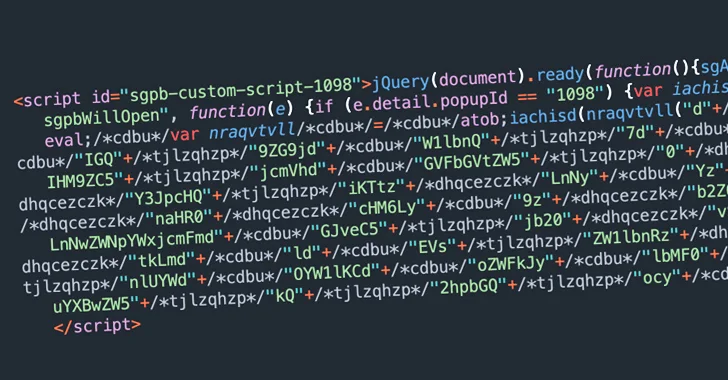
January 15, 2024
Thousands of WordPress sites using a vulnerable version of the Popup Builder plugin have been compromised with...
admin
January 14, 2024
The cyber attacks targeting the energy sector in Denmark last year may not have had the involvement...
admin
January 13, 2024
Juniper Networks has released updates to fix a critical remote code execution (RCE) vulnerability in its SRX...
admin
January 13, 2024
A 29-year-old Ukrainian national has been arrested in connection with running a “sophisticated cryptojacking scheme,” netting them...
admin
January 12, 2024
As many as five different malware families were deployed by suspected nation-state actors as part of post-exploitation...
admin
January 12, 2024
The threat actors associated with the Medusa ransomware have ramped up their activities following the debut of a dedicated...
Applying the Tyson Principle to Cybersecurity: Why Attack Simulation is Key to Avoiding a KO


5 min read
admin
January 12, 2024
Picture a cybersecurity landscape where defenses are impenetrable, and threats are nothing more than mere disturbances deflected...
admin
January 12, 2024
GitLab has released security updates to address two critical vulnerabilities, including one that could be exploited to...
admin
January 12, 2024
Cybersecurity researchers have identified a new attack that exploits misconfigurations in Apache Hadoop and Flink to deploy...
admin
January 12, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security vulnerability impacting Microsoft SharePoint Server to...
admin
January 11, 2024
Generative AI will enable anyone to launch sophisticated phishing attacks that only Next-generation MFA devices can stop
The...
admin
January 11, 2024
Cybersecurity researchers have identified an updated version of a macOS information stealer called Atomic (or AMOS), indicating that the...
admin
January 11, 2024
The ubiquity of GitHub in information technology (IT) environments has made it a lucrative choice for threat...
admin
January 11, 2024
Cybersecurity researchers have developed a proof-of-concept (PoC) code that exploits a recently disclosed critical flaw in the Apache OfBiz open-source Enterprise...
admin
January 11, 2024
A new Python-based hacking tool called FBot has been uncovered targeting web servers, cloud services, content management systems (CMS),...
admin
January 11, 2024
The compromise of Mandiant's X (formerly Twitter) account last week was likely the result of a "brute-force...
admin
January 11, 2024
A pair of zero-day flaws identified in Ivanti Connect Secure (ICS) and Policy Secure have been chained...