admin
February 26, 2024
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud...
admin
February 26, 2024
The threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure,...
admin
February 25, 2024
LockBitSupp, the individual(s) behind the persona representing the LockBit ransomware service on cybercrime forums such as Exploit...
admin
February 24, 2024
Microsoft has expanded free logging capabilities to all U.S. federal agencies using Microsoft Purview Audit irrespective of...
admin
February 23, 2024
Microsoft has released an open access automation framework called PyRIT (short for Python Risk Identification Tool) to proactively identify...
admin
February 23, 2024
Created by John Tuckner and the team at workflow and automation platform Tines, the SOC Automation Capability Matrix (SOC...
admin
February 23, 2024
A dormant package available on the Python Package Index (PyPI) repository was updated nearly after two years...
admin
February 23, 2024
Details have emerged about a now-patched high-severity security flaw in Apple's Shortcuts app that could permit a...
admin
February 23, 2024
The U.S. Federal Trade Commission (FTC) has hit antivirus vendor Avast with a $16.5 million fine over...
admin
February 22, 2024
Apple has announced a new post-quantum cryptographic protocol called PQ3 that it said will be integrated into iMessage to...
admin
February 22, 2024
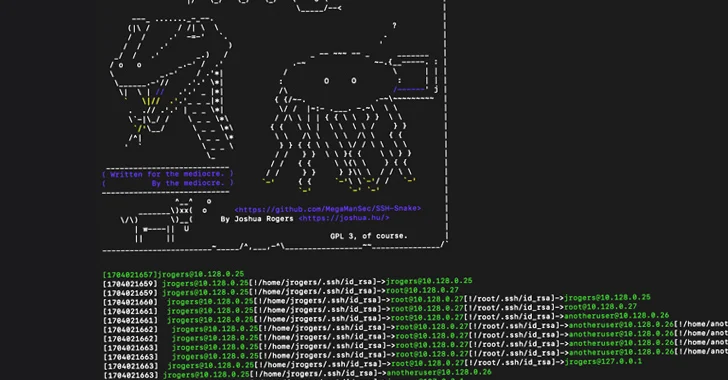
A recently open-sourced network mapping tool called SSH-Snake has been repurposed by threat actors to conduct malicious activities.
"SSH-Snake is...
admin
February 22, 2024
In the past 2 years, we have observed a significant surge in hacktivism activity due to ongoing...
admin
February 22, 2024
An installer for a tool likely used by the Russian Consular Department of the Ministry of Foreign...
admin
February 22, 2024
The U.S. State Department has announced monetary rewards of up to $15 million for information that could...
admin
February 21, 2024
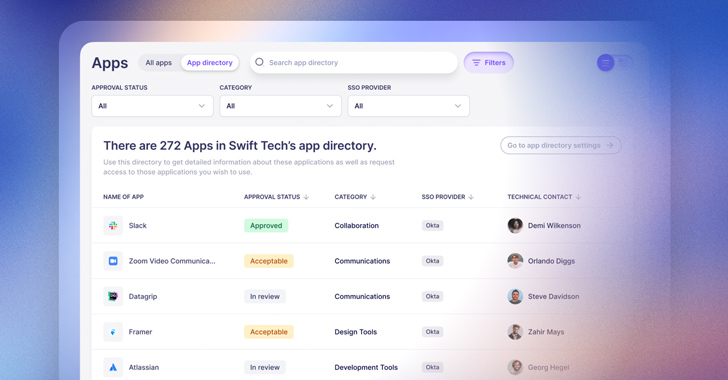
With SaaS applications now making up the vast majority of technology used by employees in most organizations,...
admin
February 21, 2024
Cybersecurity researchers have identified two authentication bypass flaws in open-source Wi-Fi software found in Android, Linux, and...
admin
February 21, 2024
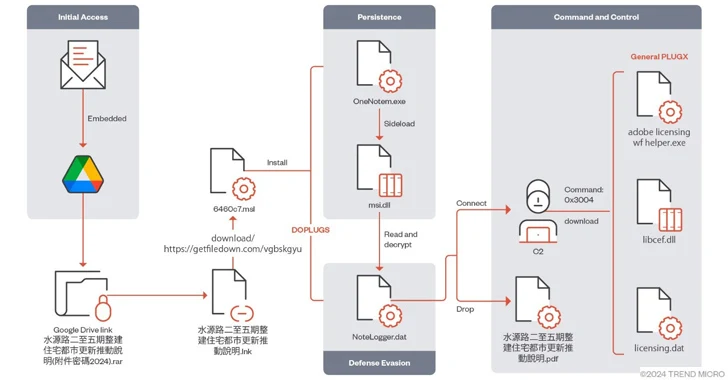
The China-linked threat actor known as Mustang Panda has targeted various Asian countries using a variant of...
admin
February 21, 2024
VMware is urging users to uninstall the deprecated Enhanced Authentication Plugin (EAP) following the discovery of a...
Cybersecurity for Healthcare—Diagnosing the Threat Landscape and Prescribing Solutions for Recovery


7 min read
admin
February 21, 2024
On Thanksgiving Day 2023, while many Americans were celebrating, hospitals across the U.S. were doing quite the...
admin
February 21, 2024
Facebook advertisers in Vietnam are the target of a previously unknown information stealer dubbed VietCredCare at least since August...