admin
March 1, 2024
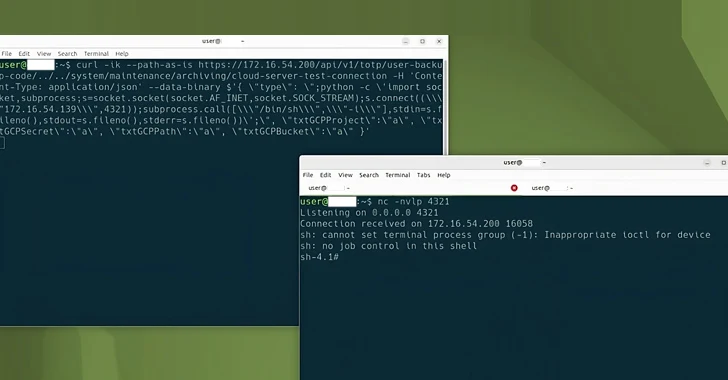
Cybersecurity researchers have discovered a new Linux variant of a remote access trojan (RAT) called BIFROSE (aka...
admin
March 1, 2024
The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber threat actors...
admin
February 29, 2024
Threat hunters have discovered a new Linux malware called GTPDOOR that’s designed to be deployed in telecom networks that...
admin
February 29, 2024
The notorious Lazarus Group actors exploited a recently patched privilege escalation flaw in the Windows Kernel as...
admin
February 29, 2024
As an IT leader, staying on top of the latest cybersecurity developments is essential to keeping your...
admin
February 29, 2024
Cybersecurity researchers have disclosed a new attack technique called Silver SAML that can be successful even in cases where...
admin
February 29, 2024
At least two different suspected China-linked cyber espionage clusters, tracked as UNC5325 and UNC3886, have been attributed to the exploitation...
admin
February 29, 2024
A previously undocumented threat actor dubbed SPIKEDWINE has been observed targeting officials in European countries with Indian diplomatic missions...
admin
February 29, 2024
The notorious North Korean state-backed hacking group Lazarus uploaded four packages to the Python Package Index (PyPI)...
admin
February 29, 2024
U.S. President Joe Biden has issued an Executive Order that prohibits the mass transfer of citizens' personal data to...
admin
February 28, 2024
An Iran-nexus threat actor known as UNC1549 has been attributed with medium confidence to a new set of attacks...
admin
February 28, 2024
The U.S. government is warning about the resurgence of BlackCat (aka ALPHV) ransomware attacks targeting the healthcare...
admin
February 28, 2024
In today's digital era, data privacy isn't just a concern; it's a consumer demand. Businesses are grappling...
admin
February 28, 2024
In a new joint advisory, cybersecurity and intelligence agencies from the U.S. and other countries are urging...
Superusers Need Super Protection: How to Bridge Privileged Access Management and Identity Management


3 min read
Superusers Need Super Protection: How to Bridge Privileged Access Management and Identity Management
admin
February 28, 2024
Traditional perimeter-based security has become costly and ineffective. As a result, communications security between people, systems, and...
admin
February 28, 2024
Mexican users have been targeted with tax-themed phishing lures at least since November 2023 to distribute a...
admin
February 27, 2024
A security vulnerability has been disclosed in the LiteSpeed Cache plugin for WordPress that could enable unauthenticated...
admin
February 27, 2024
An "intricately designed" remote access trojan (RAT) called Xeno RAT has been made available on GitHub, making it available...
admin
February 27, 2024
A critical security flaw has been disclosed in a popular WordPress plugin called Ultimate Member that has more than...
admin
February 27, 2024
Processing alerts quickly and efficiently is the cornerstone of a Security Operations Center (SOC) professional's role. Threat...