admin
March 20, 2024
The U.S. Environmental Protection Agency (EPA) said it's forming a new "Water Sector Cybersecurity Task Force" to...
admin
March 20, 2024
Did you know that 79% of organizations are already leveraging Generative AI technologies? Much like the internet...
admin
March 20, 2024
Multiple threat actors are exploiting the recently disclosed security flaws in JetBrains TeamCity software to deploy ransomware,...
admin
March 20, 2024
Cybersecurity researchers have discovered an updated variant of a stealer and malware loader called BunnyLoader that modularizes its various...
admin
March 20, 2024
The Cyber Police of Ukraine has arrested three individuals on suspicion of hijacking more than 100 million emails and...
admin
March 19, 2024
Application programming interfaces (APIs) are the connective tissue behind digital modernization, helping applications and databases exchange data...
admin
March 19, 2024
Large language models (LLMs) powering artificial intelligence (AI) tools today could be exploited to develop self-augmenting malware...
admin
March 19, 2024
A new phishing campaign is targeting U.S. organizations with the intent to deploy a remote access trojan...
admin
March 19, 2024
In an era where digital transformation drives business across sectors, cybersecurity has transcended its traditional operational role...
admin
March 19, 2024
Threat actors are leveraging digital document publishing (DDP) sites hosted on platforms like FlipSnack, Issuu, Marq, Publuu,...
admin
March 19, 2024
A new variant of a data wiping malware called AcidRain has been detected in the wild that's...
admin
March 19, 2024
A 31-year-old Moldovan national has been sentenced to 42 months in prison in the U.S. for operating...
admin
March 19, 2024
A new elaborate attack campaign has been observed employing PowerShell and VBScript malware to infect Windows systems...
admin
March 18, 2024
Fortra has released details of a now-patched critical security flaw impacting its FileCatalyst file transfer solution that could allow...
admin
March 18, 2024
Cybersecurity researchers have discovered a new malware campaign that leverages bogus Google Sites pages and HTML smuggling...
admin
March 18, 2024
The Russia-linked threat actor known as APT28 has been linked to multiple ongoing phishing campaigns that employ lure documents...
admin
March 18, 2024
WordPress users of miniOrange's Malware Scanner and Web Application Firewall plugins are being urged to delete them...
admin
March 16, 2024
Cybersecurity researchers have found a number of GitHub repositories offering cracked software that are used to deliver...
admin
March 16, 2024
A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative...
admin
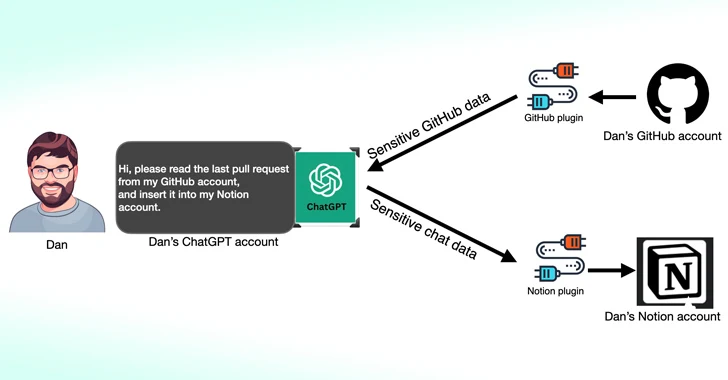
March 15, 2024
Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act as a new attack...