admin
April 24, 2024
Cybersecurity researchers have discovered an ongoing attack campaign that's leveraging phishing emails to deliver malware called SSLoad.
The campaign, codenamed FROZEN#SHADOW by...
admin
April 24, 2024
Security vulnerabilities uncovered in cloud-based pinyin keyboard apps could be exploited to reveal users' keystrokes to nefarious actors.
The...
admin
April 24, 2024
A new ongoing malware campaign has been observed distributing three different stealers, such as CryptBot, LummaC2, and Rhadamanthys hosted on Content Delivery Network (CDN)...
admin
April 23, 2024
In the high-stakes world of cybersecurity, the battleground has shifted. Supply chain attacks have emerged as a...
admin
April 23, 2024
Researchers have identified a dependency confusion vulnerability impacting an archived Apache project called Cordova App Harness.
Dependency confusion...
admin
April 23, 2024
European Police Chiefs said that the complementary partnership between law enforcement agencies and the technology industry is...
admin
April 23, 2024
Cybersecurity breaches can be devastating for both individuals and businesses alike. While many people tend to focus on understanding...
admin
April 23, 2024
German authorities said they have issued arrest warrants against three citizens on suspicion of spying for China.
The...
admin
April 23, 2024
The U.S. Department of State on Monday said it's taking steps to impose visa restrictions on 13 individuals who are allegedly...
admin
April 23, 2024
The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw in the Microsoft Windows Print Spooler component...
admin
April 22, 2024
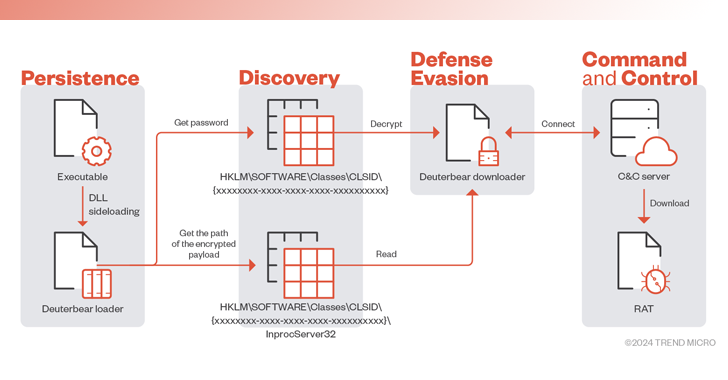
The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and...
admin
April 22, 2024
Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been...
admin
April 22, 2024
The MITRE Corporation revealed that it was the target of a nation-state cyber attack that exploited two...
admin
April 22, 2024
Between crossovers - Do threat actors play dirty or desperate?
In our dataset of over 11,000 victim...
admin
April 22, 2024
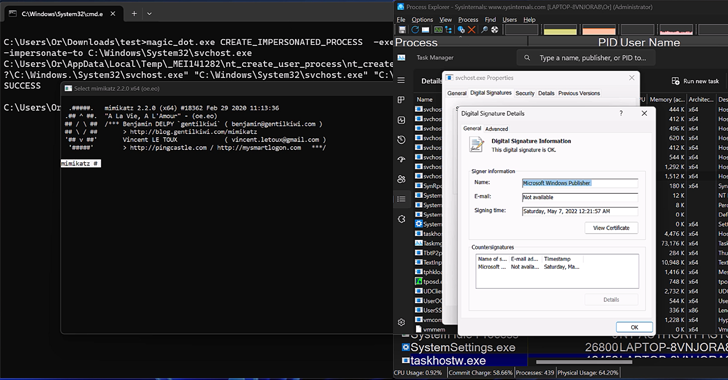
New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to...
admin
April 22, 2024
Microsoft has revealed that North Korea-linked state-sponsored cyber actors has begun to use artificial intelligence (AI) to...
admin
April 21, 2024
A new information stealer has been found leveraging Lua bytecode for added stealth and sophistication, findings from...
admin
April 20, 2024
Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS that has come under...
admin
April 20, 2024
Users of the CrushFTP enterprise file transfer software are being urged to update to the latest version following the discovery of a...
admin
April 19, 2024
Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part...