admin
June 1, 2024
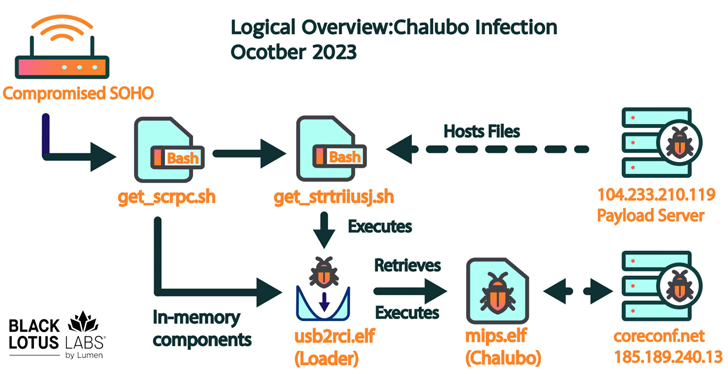
More than 600,000 small office/home office (SOHO) routers are estimated to have been bricked and taken offline...
admin
May 31, 2024
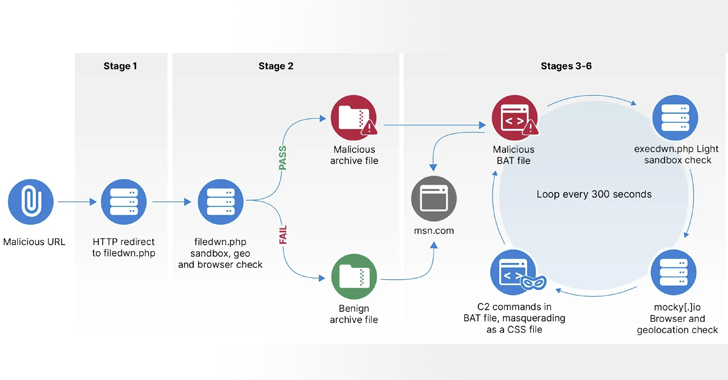
Digital content is a double-edged sword, providing vast benefits while simultaneously posing significant threats to organizations across...
admin
May 31, 2024
Microsoft has emphasized the need for securing internet-exposed operational technology (OT) devices following a spate of cyber...
admin
May 31, 2024
The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks...
admin
May 31, 2024
OpenAI on Thursday disclosed that it took steps to cut off five covert influence operations (IO) originating...
admin
May 31, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Linux...
admin
May 30, 2024
Security leaders are in a tricky position trying to discern how much new AI-driven cybersecurity tools could...
admin
May 30, 2024
Cloudflare on Thursday said it took steps to disrupt a month-long phishing campaign orchestrated by a Russia-aligned...
admin
May 30, 2024
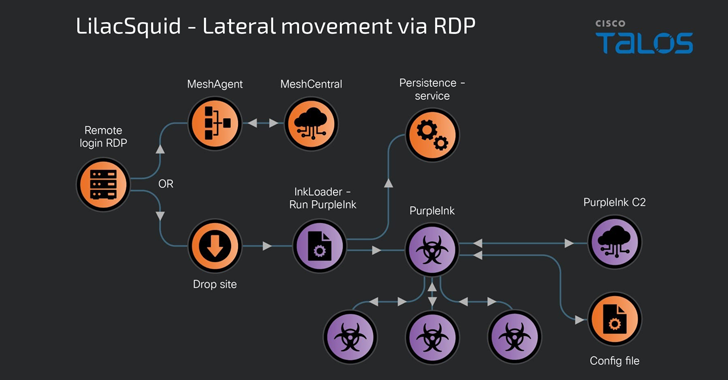
A previously undocumented cyber espionage-focused threat actor named LilacSquid has been linked to targeted attacks spanning various...
admin
May 30, 2024
The threat actors behind the RedTail cryptocurrency mining malware have added a recently disclosed security flaw impacting...
admin
May 30, 2024
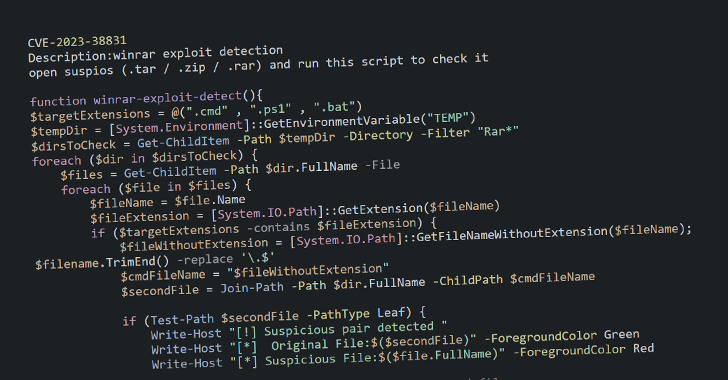
Cybersecurity researchers have warned that multiple high-severity security vulnerabilities in WordPress plugins are being actively exploited by...
admin
May 30, 2024
Europol on Thursday said it shut down the infrastructure associated with several malware loader operations such as...
admin
May 30, 2024
The U.S. Department of Justice (DoJ) on Wednesday said it dismantled what it described as "likely the...
admin
May 30, 2024
Okta is warning that a cross-origin authentication feature in Customer Identity Cloud (CIC) is susceptible to credential...
admin
May 29, 2024
The U.S. Department of Justice (DoJ) has sentenced a 31-year-old man to 10 years in prison for...
admin
May 29, 2024
A recent study by Wing Security found that 63% of businesses may have former employees with access...
admin
May 29, 2024
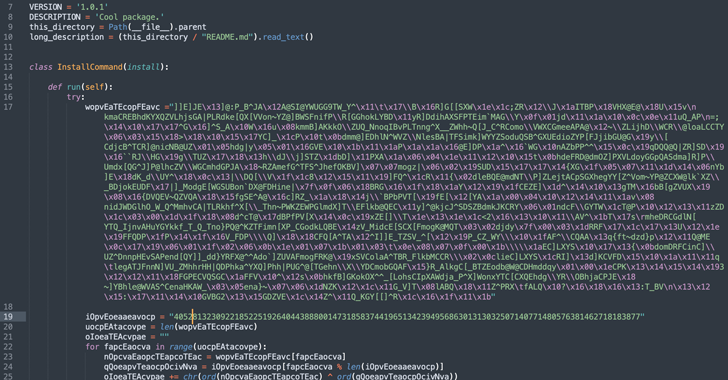
Cybersecurity researchers have warned of a new malicious Python package that has been discovered in the Python...
admin
May 29, 2024
Check Point is warning of a zero-day vulnerability in its Network Security gateway products that threat actors...
admin
May 29, 2024
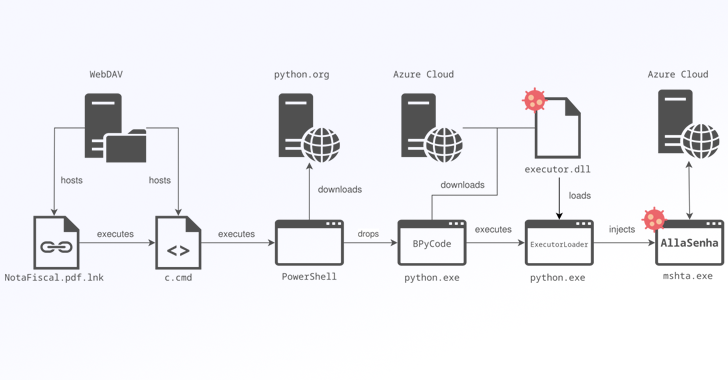
Brazilian banking institutions are the target of a new campaign that distributes a custom variant of the...
admin
May 29, 2024
A never-before-seen North Korean threat actor codenamed Moonstone Sleet has been attributed as behind cyber attacks targeting...