An Iranian nation-state threat actor has been linked to a new wave of phishing attacks targeting Israel that’s designed to deploy an updated version of a backdoor called PowerLess.
Cybersecurity firm Check Point is tracking the activity cluster under its mythical creature handle Educated Manticore, which exhibits “strong overlaps” with a hacking crew known as APT35, Charming Kitten, Cobalt Illusion, ITG18, Mint Sandstorm (formerly Phosphorus), TA453, and Yellow Garuda.
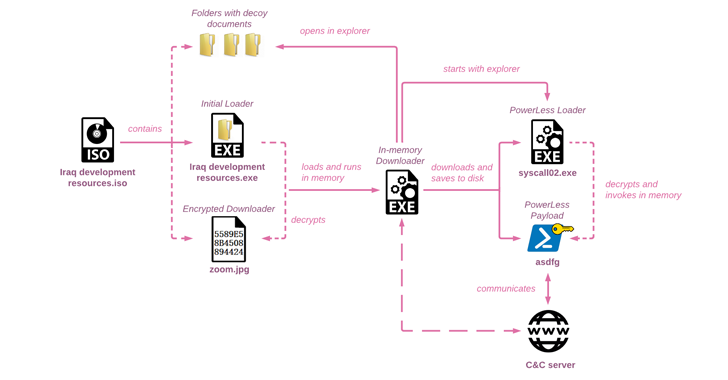
“Like many other actors, Educated Manticore has adopted recent trends and started using ISO images and possibly other archive files to initiate infection chains,” the Israeli company said in a technical report published today.
Active since at least 2011, APT35 has cast a wide net of targets by leveraging fake social media personas, spear-phishing techniques, and N-day vulnerabilities in internet-exposed applications to gain initial access and drop various payloads, including ransomware.
The development is an indication that the adversary is continuously refining and retooling its malware arsenal to expand their functionality and resist analysis efforts, while also adopting enhanced methods to evade detection.
The attack chain documented by Check Point begins with an ISO disk image file that makes use of Iraq-themed lures to drop a custom in-memory downloader that ultimately launches the PowerLess implant.
The ISO file acts as a conduit to display a decoy document written in Arabic, English, and Hebrew, and purports to feature academic content about Iraq from a legitimate non-profit entity called the Arab Science and Technology Foundation (ASTF), indicating that the research community may have been the target of the campaign.
The PowerLess backdoor, previously spotlighted by Cybereason in February 2022, comes with capabilities to steal data from web browsers and apps like Telegram, take screenshots, record audio, and log keystrokes.
“While the new PowerLess payload remains similar, its loading mechanisms have significantly improved, adopting techniques rarely seen in the wild, such as using .NET binary files created in mixed mode with assembly code,” Check Point said.
“PowerLess [command-and-control] communication to the server is Base64-encoded and encrypted after obtaining a key from the server. To mislead researchers, the threat actor actively adds three random letters at the beginning of the encoded blob.”
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
The cybersecurity firm said it also discovered two other archive files used as part of a different intrusion set that shares overlaps with the aforementioned attack sequence owing to the use of the same Iraq-themed PDF file.
Further analysis has revealed that the infection chains arising from these two archive files culminate in the execution of a PowerShell script that’s engineered to download two files from a remote server and run them.
“Educated Manticore continues to evolve, refining previously observed toolsets and delivering mechanisms,” Check Point said, adding “the actor adopts popular trends to avoid detection” and keeps “developing custom toolsets using advanced techniques.”
“Because it is an updated version of previously reported malware, […] it is important to note that it might only represent the early stages of infection, with significant fractions of post-infection activity yet to be seen in the wild.”








