New research has found that close to 12,000 internet-exposed Juniper firewall devices are vulnerable to a recently disclosed remote code execution flaw.
VulnCheck, which discovered a new exploit for CVE-2023-36845, said it could be exploited by an “unauthenticated and remote attacker to execute arbitrary code on Juniper firewalls without creating a file on the system.”
CVE-2023-36845 refers to a medium-severity flaw in the J-Web component of Junos OS that could be weaponized by a threat actor to control certain, important environment variables. It was patched by Juniper Networks last month alongside CVE-2023-36844, CVE-2023-36846, and CVE-2023-36847 in an out-of-cycle update.
A subsequent proof-of-concept (PoC) exploit devised by watchTowr combined CVE-2023-36846 and CVE-2023-36845 to upload a PHP file containing malicious shellcode and achieve code execution.
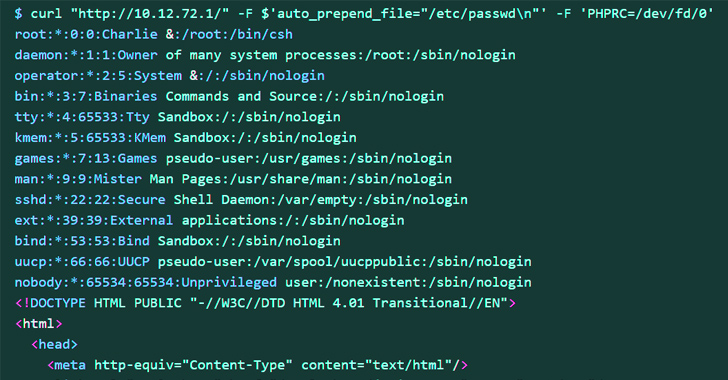
The latest exploit, on the other hand, impacts older systems and can be written using a single cURL command. Specifically, it relies on just CVE-2023-36845 to realize the same objective.
This, in turn, is accomplished by using the standard input stream (aka stdin) to set the PHPRC environment variable to “/dev/fd/0” via a specially crafted HTTP request, effectively turning “/dev/fd/0” into a makeshift file, and leak sensitive information.
Arbitrary code execution is then achieved by leveraging PHP’s auto_prepend_file and allow_url_include options in conjunction with the data:// protocol wrapper.
Identity is the New Endpoint: Mastering SaaS Security in the Modern Age
Dive deep into the future of SaaS security with Maor Bin, CEO of Adaptive Shield. Discover why identity is the new endpoint. Secure your spot now.
“Firewalls are interesting targets to APT as they help bridge into the protected network and can serve as useful hosts for C2 infrastructure,” Jacob Baines said. “Anyone who has an unpatched Juniper firewall should examine it for signs of compromise.”
Juniper has since disclosed that it’s not aware of a successful exploit against its customers, but warned that it has detected exploitation attempts in the wild, making it imperative that users apply the necessary fixes to mitigate potential threats.




