The most precious asset in today’s information age is the secret safeguarded under lock and key. Regrettably, maintaining secrets has become increasingly challenging, as highlighted by the 2023 State of Secrets Sprawl report, the largest analysis of public GitHub activity.
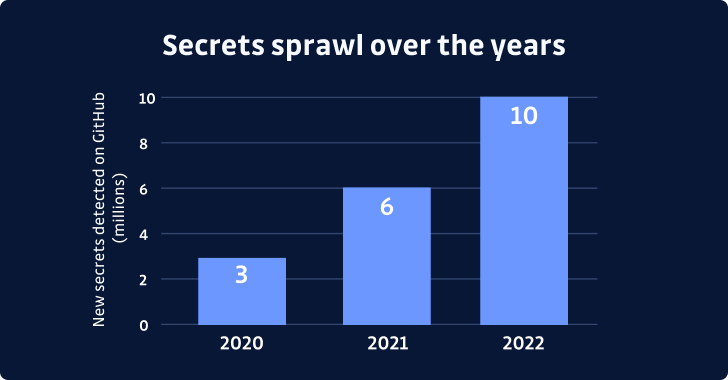
The report shows a 67% year-over-year increase in the number of secrets found, with 10 million hard-coded secrets detected in 2022 alone. This alarming surge in secrets sprawl highlights the need for action and underscores the importance of secure software development.
Secrets sprawl refers to secrets appearing in plaintext in various sources, such as source code, build scripts, infrastructure as code, logs, etc. While secrets like API tokens and private keys securely connect the components of the modern software supply chain, their widespread distribution among developers, machines, applications, and infrastructure systems heightens the likelihood of leaks.
Cybersecurity Incidents Highlight the Dangers of Hard-Coded Secrets
Two high-profile cybersecurity incidents involving Uber and Toyota have underlined the urgent need to address the issue of secrets sprawl and prioritize code security. As awareness around this issue grows, it is imperative for companies to prioritize the protection of secrets and invest in innovative solutions that detect and remediate potential threats.
Uber suffered an attack in which an attacker gained access to critical systems using hard-coded admin credentials found in a PowerShell script. In contrast, Toyota inadvertently exposed credentials granting access to customer data in a public GitHub repository for almost five years. Both incidents serve as glaring reminders of the risks associated with secrets sprawl. Moreover, as the report points out, most security incidents involve, at some point, secrets: it may be keys leveraged by attackers or exposed through leaked source code, for instance.
A Major Blind Spot in Application Security
With 1 out of every 10 code authors exposing a secret in 2022, it’s evident that this issue transcends experience levels and afflicts developers across the board.
Secrets management is gaining increased attention as more organizations scrutinize their software supply chain processes following a string of high-profile security breaches. Cybersecurity teams have traditionally focused on identifying vulnerabilities rather than uncovering poorly secured credentials. As a result, countless applications running in production environments may have undiscovered secrets management issues.
In a perfect scenario, adopting DevSecOps best practices would address this growing issue. Yet, with the constant expansion of code repositories, more basic errors appear. Recognizing software supply chain vulnerabilities, cybercriminals proactively scan repositories to find secrets that could facilitate application breaches.
The issue will likely worsen as attacks on software supply chains are expected to escalate. As technology advances and code becomes more entwined with our daily lives, the risks associated with secrets sprawl become more pressing.
The intensified focus on securing software supply chains, especially in light of the Biden administration’s National Cybersecurity Strategy, is expected to drive more IT organizations to implement end-to-end security measures within their software development life cycles. As a result, DevOps teams should anticipate anincreased focus on secrets management from cybersecurity experts.
Embracing Proactive Measures to Mitigate Secrets Sprawl Risks
To combat this growing threat, organizations must prioritize the protection of their secrets and invest in solutions for detecting and addressing potential vulnerabilities.
The continued growth of the everything-as-code paradigm and the commoditization of digital infrastructure and services means that software, code, and secrets will only become more critical in their daily business operations.
The risk of secrets exposure cannot entirely be eliminated, even with centralized secret management systems. But it can be mitigated by addressing poor secrets hygiene practices and implementing remediation playbooks.
To measure how much a secrets detection and remediation program could bring to your organization, you can use our free Value Calculator to estimate the probable cost of not dealing with a security debt consisting of thousands of hard-coded secrets today.
By learning to live with this issue and putting the right tools and resources in place, companies can significantly reduce the risks associated with leaked and exploited secrets.
In conclusion, secrets sprawl is a growing threat requiring organizations’ immediate attention. With the right tools and strategies in place, companies can mitigate the risks associated with leaked and exploited secrets. It’s time to prioritize secrets management and invest in innovative solutions to ensure our secrets remain safe and secure.
In a world where information is power, it’s time to take action and ensure our secrets remain safely under lock and key.






