A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems.
That’s according to findings from SentinelOne, which observed an increase in the number of Geacon payloads appearing on VirusTotal in recent months.
“While some of these are likely red-team operations, others bear the characteristics of genuine malicious attacks,” security researchers Phil Stokes and Dinesh Devadoss said in a report.
Cobalt Strike is a well-known red teaming and adversary simulation tool developed by Fortra. Owing to its myriad capabilities, illegally cracked versions of the software have been abused by threat actors over the years.
While post-exploitation activity associated with Cobalt Strike has primarily singled out Windows, such attacks against macOS are something of a rarity.
In May 2022, software supply chain firm Sonatype disclosed details of a rogue Python package called “pymafka” that was designed to drop a Cobalt Strike Beacon onto compromised Windows, macOS, and Linux hosts.
That may, however, change with the emergence of Geacon artifacts in the wild. Geacon is a Go variant of Cobalt Strike that has been available on GitHub since February 2020.
Further analysis of two new VirusTotal samples that were uploaded in April 2023 has traced their origins to two Geacon variants (geacon_plus and geacon_pro) that were developed in late October by two anonymous Chinese developers z3ratu1 and H4de5.
The geacon_pro project is no longer accessible on GitHub, but an Internet Archive snapshot captured on March 6, 2023, reveals its ability to bypass antivirus engines such as Microsoft Defender, Kaspersky, and Qihoo 360 360 Core Crystal.
H4de5, the developer behind geacon_pro, claims the tool is mainly designed to support CobaltStrike versions 4.1 and later, while geacon_plus supports CobaltStrike version 4.0. The current version of the software is 4.8.
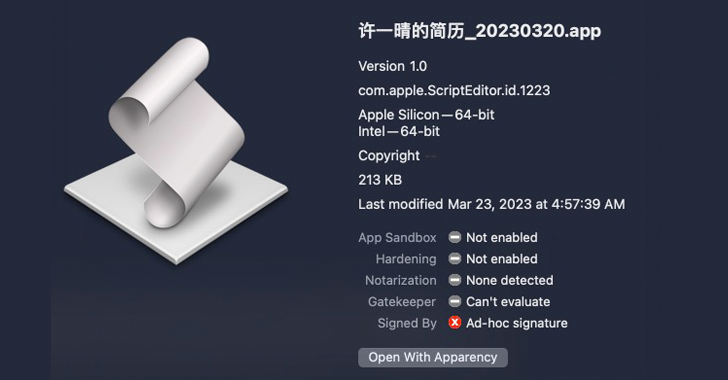
Xu Yiqing’s Resume_20230320.app, one of the artifacts discovered by SentinelOne, employs a run-only AppleScript to reach out to a remote server and download a Geacon payload. It’s compatible with both Apple silicon and Intel architectures.
“The unsigned Geacon payload is retrieved from an IP address in China,” the researchers said. “Before it begins its beaconing activity, the user is presented with a two-page decoy document embedded in the Geacon binary. A PDF is opened displaying a resume for an individual named ‘Xu Yiqing.'”
The Geacon binary, compiled from the geacon_plus source code, packs a multitude of functions that allows it to download next-stage payloads and exfiltrate data, and facilitate network communications.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
The second sample, per the cybersecurity firm, is embedded within a trojanized app that masquerades as the SecureLink remote support app (SecureLink.app) and mainly targets Intel devices.
The barebones, unsigned application requests for users’ permission to access contacts, photos, reminders, as well as the device’s camera and microphone. Its main component is a Geacon payload built from the geacon_pro project that connects to a known command-and-control (C2) server in Japan.
The development comes as the macOS ecosystem is being targeted by a wide variety of threat actors, including state-sponsored groups, to deploy backdoors and information stealers.
“The uptick in Geacon samples over the last few months suggests that security teams should be paying attention to this tool and ensuring that they have protections in place,” the researchers said.







