A recent campaign undertaken by Earth Preta indicates that nation-state groups aligned with China are getting increasingly proficient at bypassing security solutions.
The threat actor, active since at least 2012, is tracked by the broader cybersecurity community under Bronze President, HoneyMyte, Mustang Panda, RedDelta, and Red Lich.
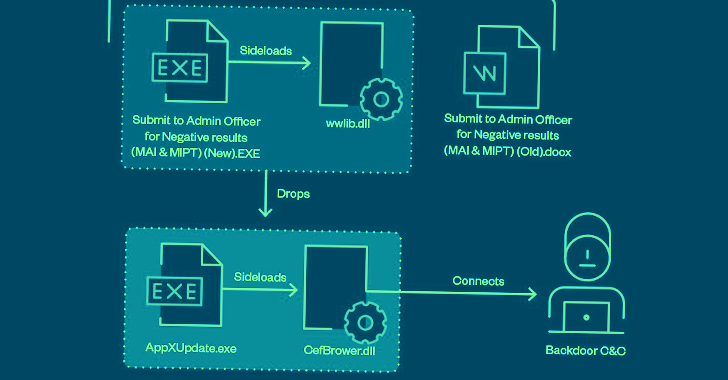
Attack chains mounted by the group commence with a spear-phishing email to deploy a wide range of tools for backdoor access, command-and-control (C2), and data exfiltration.
These messages come bearing with malicious lure archives distributed via Dropbox or Google Drive links that employ DLL side-loading, LNK shortcut files, and fake file extensions as arrival vectors to obtain a foothold and drop backdoors like TONEINS, TONESHELL, PUBLOAD, and MQsTTang (aka QMAGENT).
Similar infection chains utilizing Google Drive links have been observed delivering Cobalt Strike as early as April 2021.
“Earth Preta tends to hide malicious payloads in fake files, disguising them as legitimate ones — a technique that has been proven effective for avoiding detection,” Trend Micro said in a new analysis published Thursday.
This entry point method, which was first spotted late last year, has since received a slight tweak wherein the download link to the archive is embedded within another decoy document and the file is password-protected in an attempt to sidestep email gateway solutions.
“The files can then be extracted inside via the password provided in the document,” the researchers said. “By using this technique, the malicious actor behind the attack can successfully bypass scanning services.”
Initial access to the victim’s environment is followed by account discovery and privilege escalation phases, with Mustang Panda leveraging custom tools like ABPASS and CCPASS to circumvent User Account Control (UAC) in Windows 10.
Additionally, the threat actor has been observed deploying malware such as “USB Driver.exe” (HIUPAN or MISTCLOAK) and “rzlog4cpp.dll” (ACNSHELL or BLUEHAZE) to install themselves to removable disks and create a reverse shell with the goal of laterally moving across the network.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
Other utilities deployed include CLEXEC, a backdoor capable of executing commands and clearing event logs; COOLCLIENT and TROCLIENT, implants that are designed to record keystrokes as well as read and delete files; and PlugX.
“Apart from well-known legitimate tools, the threat actors also crafted highly customized tools used for exfiltration,” the researchers noted. This comprises NUPAKAGE and ZPAKAGE, both of which are equipped to collect Microsoft Office files.
The findings once again highlight the increased operational tempo of Chinese cyber espionage actors and their consistent investment in advancing their cyber weaponry to evade detection.
“Earth Preta is a capable and organized threat actor that is continuously honing its TTPs, strengthening its development capabilities, and building a versatile arsenal of tools and malware,” the researchers concluded.





