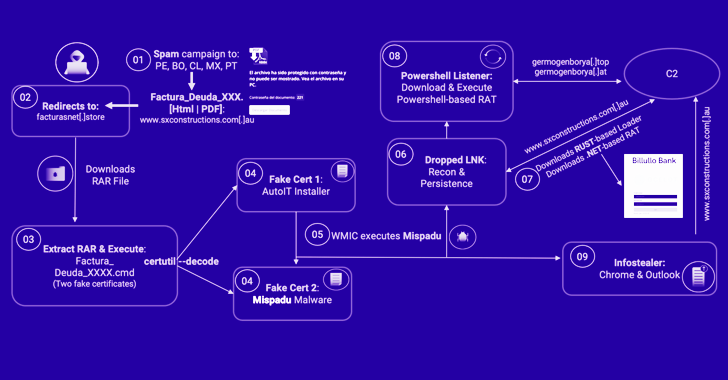
A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru, and Portugal with the goal of stealing credentials and delivering other payloads.
The activity, which commenced in August 2022, is currently ongoing, Ocelot Team from Latin American cybersecurity firm Metabase Q said in a report shared with The Hacker News.
Mispadu (aka URSA) was first documented by ESET in November 2019, describing its ability to perpetrate monetary and credential theft and act as a backdoor by taking screenshots and capturing keystrokes.
“One of their main strategies is to compromise legitimate websites, searching for vulnerable versions of WordPress, to turn them into their command-and-control server to spread malware from there, filtering out countries they do not wish to infect, dropping different type of malware based on the country being infected,” researchers Fernando García and Dan Regalado said.
It’s also said to share similarities with other banking trojans targeting the region, like Grandoreiro, Javali, and Lampion. Attack chains involving the Delphi malware leverage email messages urging recipients to open fake overdue invoices, thereby triggering a multi-stage infection process.
Should a victim open the HTML attachment sent via the spam email, it verifies that the file was opened from a desktop device and then redirects to a remote server to fetch the first-stage malware.
The RAR or ZIP archive, when launched, is designed to make use of rogue digital certificates – one which is the Mispadu malware and the other, an AutoIT installer – to decode and execute the trojan by abusing the legitimate certutil command-line utility.
Mispadu is equipped to gather the list of antivirus solutions installed on the compromised host, siphon credentials from Google Chrome and Microsoft Outlook, and facilitate the retrieval of additional malware.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
This includes an obfuscated Visual Basic Script dropper that serves to download another payload from a hard-coded domain, a .NET-based remote access tool that can run commands issued by an actor-controlled server, and a loader written in Rust that, in turn, executes a PowerShell loader to run files directly from memory.
What’s more, the malware utilizes malicious overlay screens to obtain credentials associated with online banking portals and other sensitive information.
Metabase Q noted that the certutil approach has allowed Mispadu to bypass detection by a wide range of security software and harvest over 90,000 bank account credentials from over 17,500 unique websites.







