A sophisticated attack campaign dubbed SCARLETEEL is targeting containerized environments to perpetrate theft of proprietary data and software.
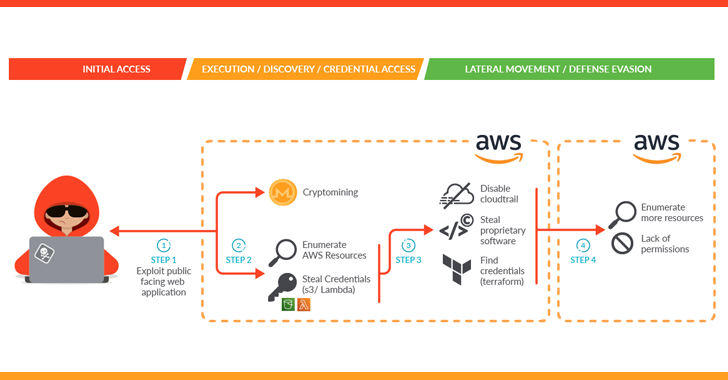
“The attacker exploited a containerized workload and then leveraged it to perform privilege escalation into an AWS account in order to steal proprietary software and credentials,” Sysdig said in a new report.
The advanced cloud attack also entailed the deployment of crypto miner software, which the cybersecurity company said is either an attempt to generate illicit profits or a ploy to distract defenders and throw them off the trail.
The initial infection vector banked on exploiting a vulnerable public-facing service in a self-managed Kubernetes cluster hosted on Amazon Web Services (AWS).
Upon gaining a successful foothold, an XMRig crypto miner was launched and a bash script was used to obtain credentials that could be used to further burrow into the AWS cloud infrastructure and exfiltrate sensitive data.
“Either crypto mining was the attacker’s initial goal and the goal changed once they accessed the victim’s environment, or crypto mining was used as a decoy to evade the detection of data exfiltration,” the company said.
The intrusion notably also disabled CloudTrail logs to minimize the digital footprint, preventing Sysdig from accessing additional evidence. In all, it allowed the threat actor to access more than 1TB of data, including customer scripts, troubleshooting tools, and logging files.
“They also attempted to pivot using a Terraform state file to other connected AWS accounts to spread their reach throughout the organization,” the company said. This, however, proved to be unsuccessful due to lack of permissions.
The findings come weeks after Sysdig also detailed another cryptojacking campaign mounted by the 8220 Gang between November 2022 and January 2023 targeting exploitable Apache web server and Oracle Weblogic applications.




