A version of an open source ransomware toolkit called Cryptonite has been observed in the wild with wiper capabilities due to its “weak architecture and programming.”
Cryptonite, unlike other ransomware strains, is not available for sale on the cybercriminal underground, and was instead offered for free by an actor named CYBERDEVILZ until recently through a GitHub repository. The source code and its forks have since been taken down.
Written in Python, the malware employs the Fernet module of the cryptography package to encrypt files with a “.cryptn8” extension.
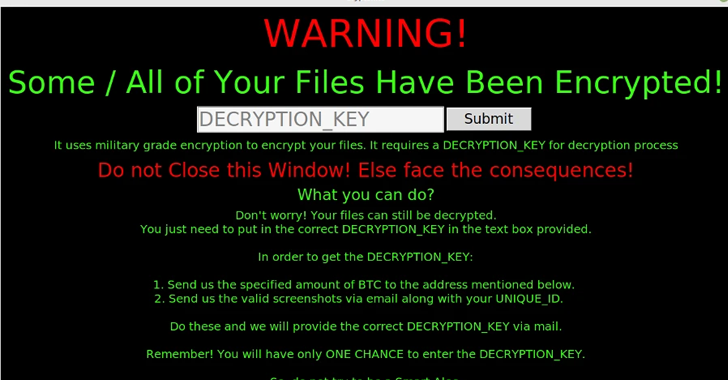
But a new sample analyzed by Fortinet FortiGuard Labs has been found to lock files with no option to decrypt them back, essentially acting as a destructive data wiper.
But this change isn’t a deliberate act on part of the threat actor, but rather stems from a lack of quality assurance that causes the program to crash when attempting to display the ransom note after completing the encryption process.
“The problem with this flaw is that due to the design simplicity of the ransomware if the program crashes — or is even closed — there is no way to recover the encrypted files,” Fortinet researcher Gergely Revay said in a Monday write-up.
The exception thrown during the execution of the ransomware program also means that the “key” used to encrypt the files is never transmitted to the operators, thereby locking users out of their data.
The findings come against the backdrop of an evolving ransomware landscape where wipers under the guise of file-encrypting malware are being increasingly deployed to overwrite data without allowing for decryption.









