admin
July 3, 2025
Cisco has released security updates to address a maximum-severity security flaw in Unified Communications Manager (Unified CM)...
admin
July 3, 2025
Threat actors with ties to North Korea have been observed targeting Web3 and cryptocurrency-related businesses with malware...
Vercel’s v0 AI Tool Weaponized by Cybercriminals to Rapidly Create Fake Login Pages at Scale


2 min read
admin
July 2, 2025
Unknown threat actors have been observed weaponizing v0, a generative artificial intelligence (AI) tool from Vercel, to...
admin
July 2, 2025
With nearly 80% of cyber threats now mimicking legitimate user behavior, how are top SOCs determining what’s...
Hackers Using PDFs to Impersonate Microsoft, DocuSign, and More in Callback Phishing Campaigns


5 min read
admin
July 2, 2025
Cybersecurity researchers are calling attention to phishing campaigns that impersonate popular brands and trick targets into calling...
U.S. Sanctions Russian Bulletproof Hosting Provider for Supporting Cybercriminals Behind Ransomware


3 min read
admin
July 2, 2025
The U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) has levied sanctions against Russia-based...
admin
July 2, 2025
Cybersecurity researchers have discovered a critical security vulnerability in artificial intelligence (AI) company Anthropic's Model Context Protocol...
admin
July 1, 2025
Cybersecurity researchers have flagged the tactical similarities between the threat actors behind the RomCom RAT and a...
New Flaw in IDEs Like Visual Studio Code Lets Malicious Extensions Bypass Verified Status


3 min read
admin
July 1, 2025
A new study of integrated development environments (IDEs) like Microsoft Visual Studio Code, Visual Studio, IntelliJ IDEA,...
admin
July 1, 2025
Despite years of investment in Zero Trust, SSE, and endpoint protection, many enterprises are still leaving one...
admin
July 1, 2025
Google has released security updates to address a vulnerability in its Chrome browser for which an exploit...
admin
July 1, 2025
The U.S. Department of Justice (DoJ) on Monday announced sweeping actions targeting the North Korean information technology...
admin
July 1, 2025
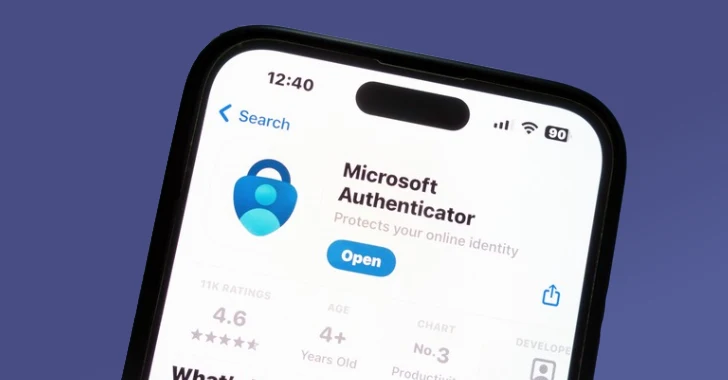
Microsoft has said that it's ending support for passwords in its Authenticator app starting August 1, 2025.
The...
admin
June 30, 2025
U.S. cybersecurity and intelligence agencies have issued a joint advisory warning of potential cyber-attacks from Iranian state-sponsored...
admin
June 30, 2025
Europol on Monday announced the takedown of a cryptocurrency investment fraud ring that laundered €460 million ($540...
admin
June 30, 2025
The threat actor known as Blind Eagle has been attributed with high confidence to the use of...
admin
June 30, 2025
Identity-based attacks are on the rise. Attacks in which malicious actors assume the identity of an entity...
admin
June 30, 2025
Ever wonder what happens when attackers don’t break the rules—they just follow them better than we do?...
admin
June 28, 2025
The U.S. Federal Bureau of Investigation (FBI) has revealed that it has observed the notorious cybercrime group...
admin
June 28, 2025
The threat actor behind the GIFTEDCROOK malware has made significant updates to turn the malicious program from...