admin
March 28, 2023
Apple on Monday backported fixes for an actively exploited security flaw to older iPhone and iPad models.
The...
admin
March 27, 2023
Conor Brian Fitzpatrick, the 20-year-old founder and the administrator of the now-defunct BreachForums has been formally charged in the...
admin
March 27, 2023
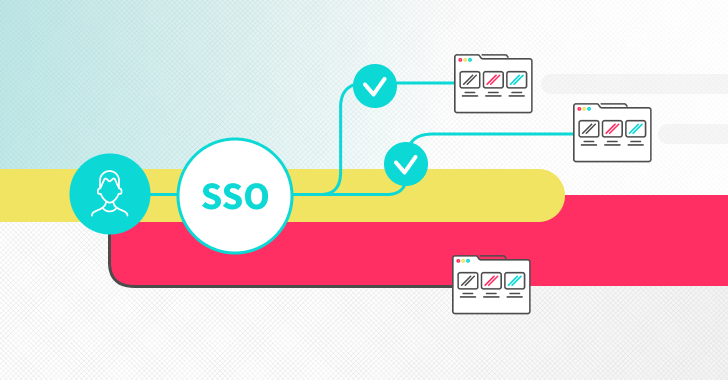
Single sign-on (SSO) is an authentication method that allows users to authenticate their identity for multiple applications...
admin
March 27, 2023
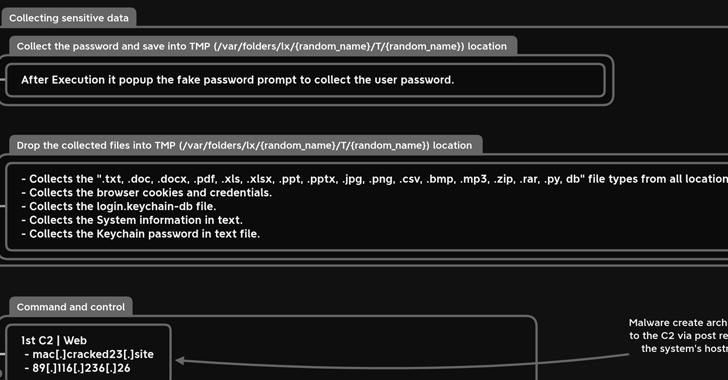
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive information...
admin
March 27, 2023
Microsoft has released an out-of-band update to address a privacy-defeating flaw in its screenshot editing tool for...
admin
March 25, 2023
OpenAI on Friday disclosed that a bug in the Redis open source library was responsible for the...
admin
March 25, 2023
In what's a case of setting a thief to catch a thief, the U.K. National Crime Agency...
admin
March 25, 2023
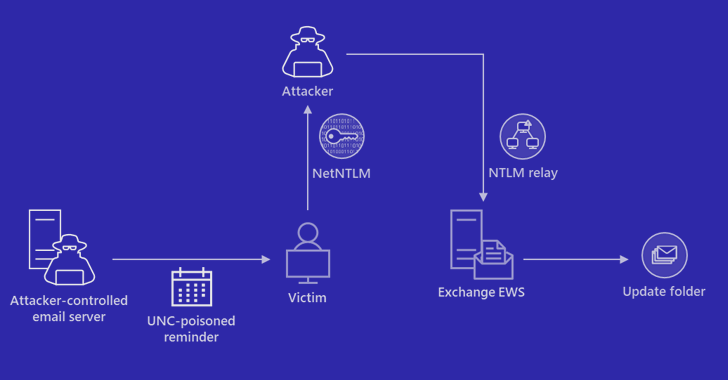
Microsoft on Friday shared guidance to help customers discover indicators of compromise (IoCs) associated with a recently...
admin
March 24, 2023
Any app that can improve business operations is quickly added to the SaaS stack. However, employees don't...
admin
March 24, 2023
A malicious Python package on the Python Package Index (PyPI) repository has been found to use Unicode...
admin
March 24, 2023
Cloud-based repository hosting service GitHub said it took the step of replacing its RSA SSH host key...
admin
March 24, 2023
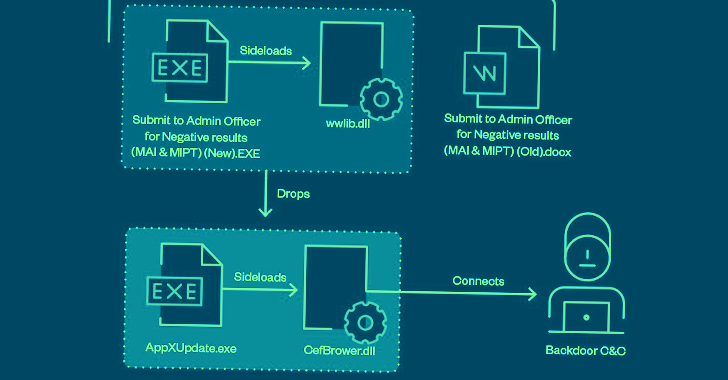
A recent campaign undertaken by Earth Preta indicates that nation-state groups aligned with China are getting increasingly proficient at...
admin
March 24, 2023
Patches have been released for a critical security flaw impacting the WooCommerce Payments plugin for WordPress, which...
admin
March 23, 2023
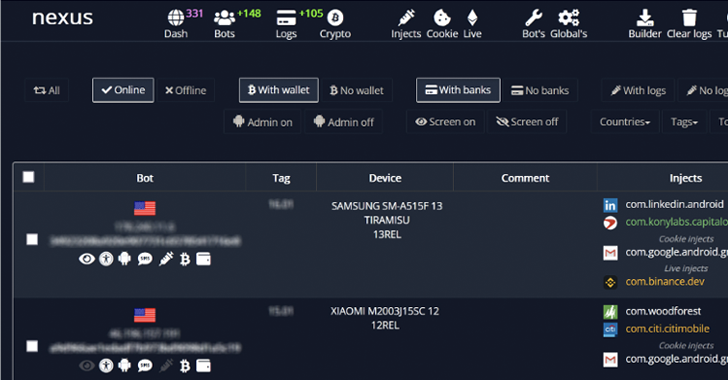
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial...
admin
March 23, 2023
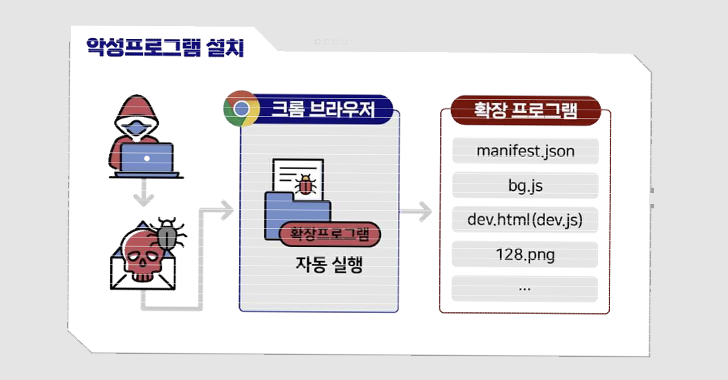
Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that...
2023 Cybersecurity Maturity Report Reveals Organizational Unpreparedness for Cyberattacks


3 min read
admin
March 23, 2023
In 2022 alone, global cyberattacks increased by 38%, resulting in substantial business loss, including financial and reputational...
admin
March 23, 2023
Telecommunication providers in the Middle East are the subject of new cyber attacks that commenced in the...
admin
March 23, 2023
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked...
admin
March 22, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released eight Industrial Control Systems (ICS) advisories on Tuesday, warning...
admin
March 22, 2023
The North Korean advanced persistent threat (APT) actor dubbed ScarCruft is using weaponized Microsoft Compiled HTML Help...