admin
April 5, 2023
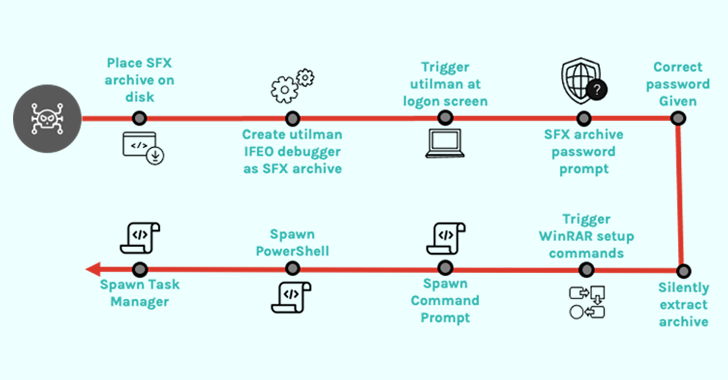
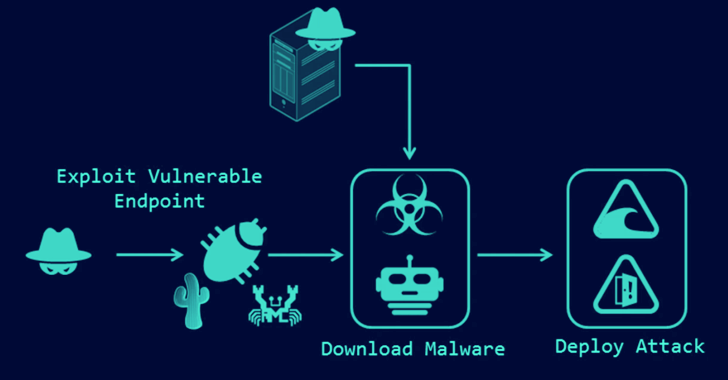
An unknown threat actor used a malicious self-extracting archive (SFX) file in an attempt to establish persistent...
admin
April 5, 2023
A North Korean government-backed threat actor has been linked to attacks targeting government and military personnel, think...
admin
April 5, 2023
Every year hundreds of millions of malware attacks occur worldwide, and every year businesses deal with the...
admin
April 5, 2023
The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that...
admin
April 4, 2023
Clouded vision
CTI systems are confronted with some major issues ranging from the size of the collection networks...
admin
April 4, 2023
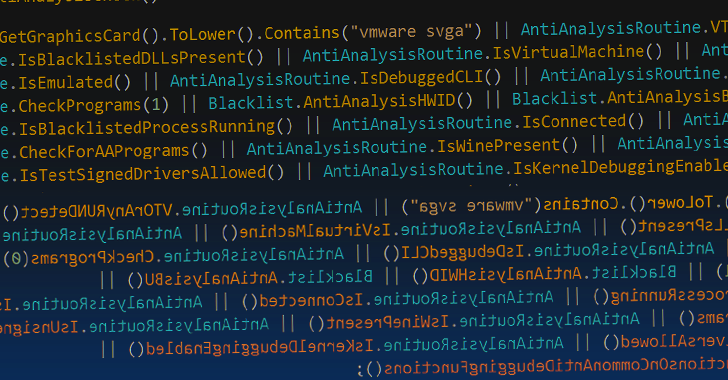
Cybersecurity researchers have taken the wraps off a previously undocumented ransomware strain called Rorschach that's both sophisticated and fast.
"What...
admin
April 4, 2023
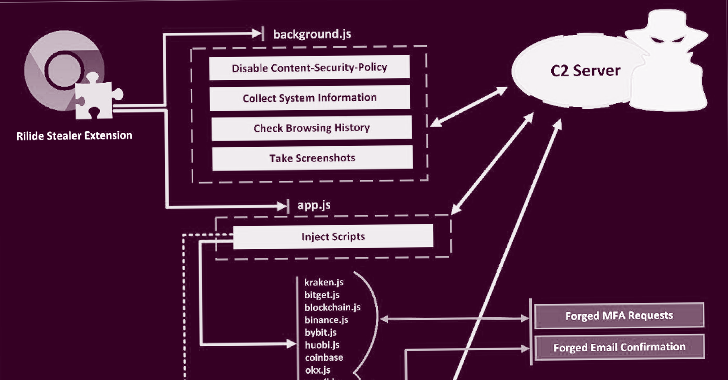
Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a...
admin
April 4, 2023
The threat actor known as Arid Viper has been observed using refreshed variants of its malware toolkit in its...
admin
April 4, 2023
Collaboration sits at the essence of SaaS applications. The word, or some form of it, appears in...
admin
April 4, 2023
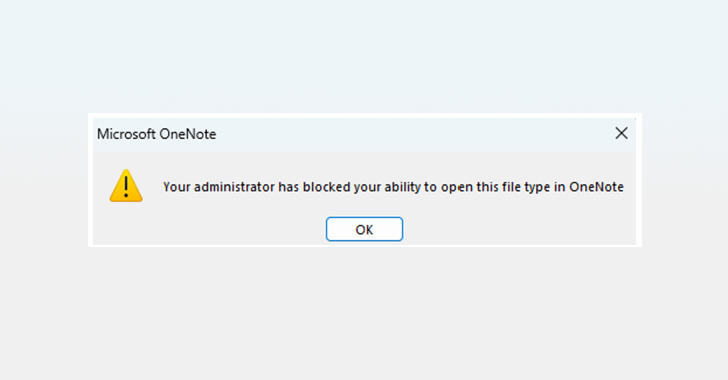
Microsoft has announced plans to automatically block embedded files with "dangerous extensions" in OneNote following reports that...
admin
April 4, 2023
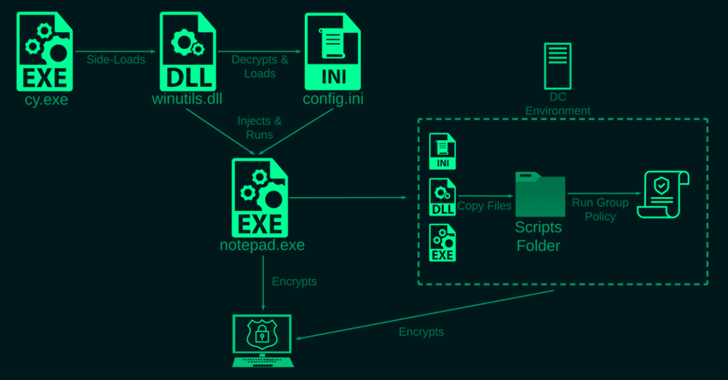
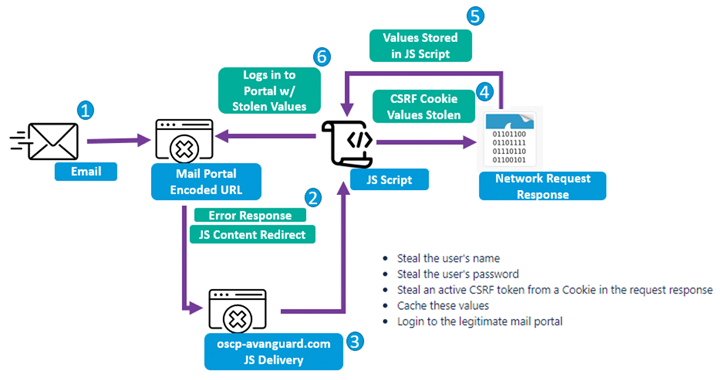
The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number...
admin
April 3, 2023
The Italian data protection watchdog, Garante per la Protezione dei Dati Personali (aka Garante), has imposed a...
admin
April 3, 2023
Data storage devices maker Western Digital on Monday disclosed a "network security incident" that involved unauthorized access...
“It’s The Service Accounts, Stupid”: Why Do PAM Deployments Take (almost) Forever To Complete


7 min read
admin
April 3, 2023
Privileged Access Management (PAM) solutions are regarded as the common practice to prevent identity threats to administrative...
admin
April 3, 2023
A piece of new information-stealing malware called OpcJacker has been spotted in the wild since the second half of...
admin
April 1, 2023
Microsoft has patched a misconfiguration issue impacting the Azure Active Directory (AAD) identity and access management service...
admin
April 1, 2023
Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors...
admin
April 1, 2023
Unknown threat actors are actively exploiting a recently patched security vulnerability in the Elementor Pro website builder...
admin
March 31, 2023
Organizations rely on Incident response to ensure they are immediately aware of security incidents, allowing for quick action to...
admin
March 31, 2023
The advanced persistent threat (APT) actor known as Winter Vivern is now targeting officials in Europe and...