admin
April 19, 2023
Elite hackers associated with Russia's military intelligence service have been linked to large-volume phishing campaigns aimed at hundreds of...
admin
April 19, 2023
The cyber espionage actor tracked as Blind Eagle has been linked to a new multi-stage attack chain that leads...
admin
April 19, 2023
Google on Tuesday rolled out emergency fixes to address another actively exploited high-severity zero-day flaw in its...
admin
April 19, 2023
The Pakistan-based advanced persistent threat (APT) actor known as Transparent Tribe used a two-factor authentication (2FA) tool used by...
admin
April 19, 2023
Recent data breaches across CircleCI, LastPass, and Okta underscore a common theme: The enterprise SaaS stacks connected...
admin
April 19, 2023
U.K. and U.S. cybersecurity and intelligence agencies have warned of Russian nation-state actors exploiting now-patched flaws in networking equipment...
admin
April 19, 2023
An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the...
admin
April 19, 2023
A fresh round of patches has been made available for the vm2 JavaScript library to address two...
admin
April 18, 2023
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named "in2al5d p3in4er" (read: invalid...
admin
April 18, 2023
A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than...
admin
April 18, 2023
Rapid technological evolution requires security that is resilient, up to date and adaptable.
In this article, we will...
admin
April 18, 2023
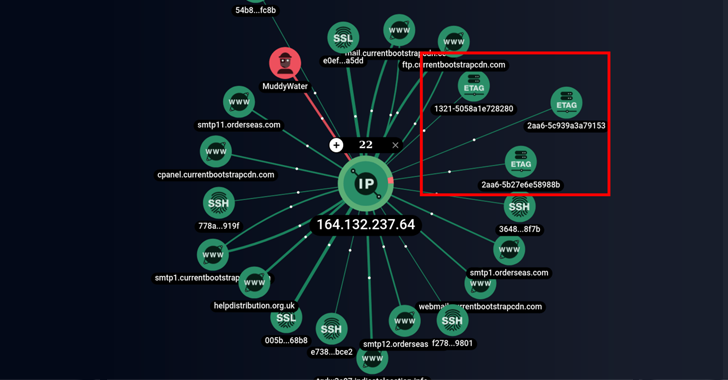
The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote...
admin
April 18, 2023
Threat actors behind the LockBit ransomware operation have developed new artifacts that can encrypt files on devices...
admin
April 17, 2023
A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming...
admin
April 17, 2023
The Deep, Dark Web – The Underground – is a haven for cybercriminals, teeming with tools and...
admin
April 17, 2023
Israeli spyware vendor QuaDream is allegedly shutting down its operations in the coming days, less than a...
admin
April 17, 2023
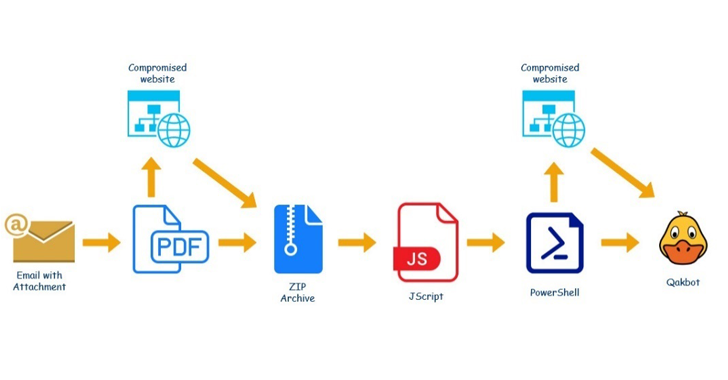
A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the...
admin
April 17, 2023
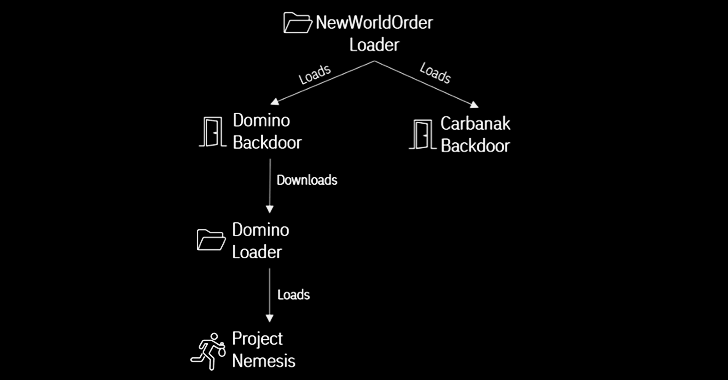
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has...
admin
April 17, 2023
Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM) are frequently confused. The similarity of the acronyms...
admin
April 17, 2023
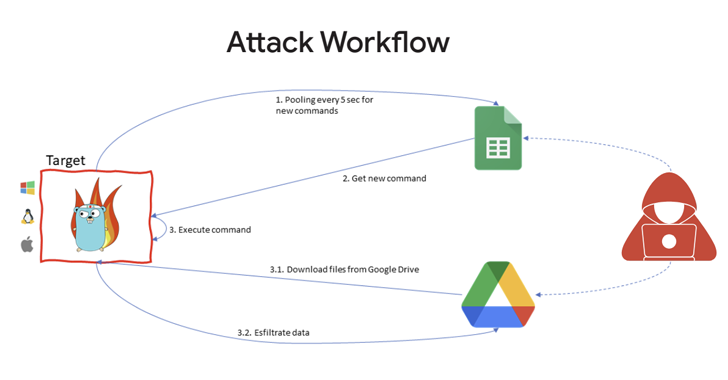
Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool...

.jpg)