admin
April 24, 2023
A recent review by Wing Security, a SaaS security company that analyzed the data of over 500...
admin
April 24, 2023
Threat actors have been observed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor websites as...
admin
April 24, 2023
The Russian-speaking threat actor behind a backdoor known as Tomiris is primarily focused on gathering intelligence in...
admin
April 24, 2023
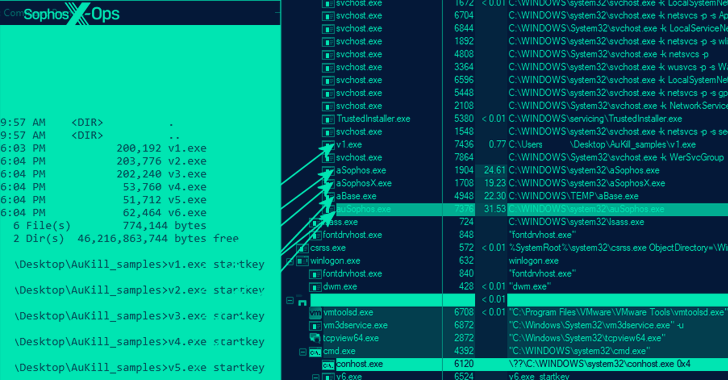
Threat actors are employing a previously undocumented "defense evasion tool" dubbed AuKill that's designed to disable endpoint...
admin
April 24, 2023
A new "all-in-one" stealer malware named EvilExtractor (also spelled Evil Extractor) is being marketed for sale for other threat...
admin
April 24, 2023
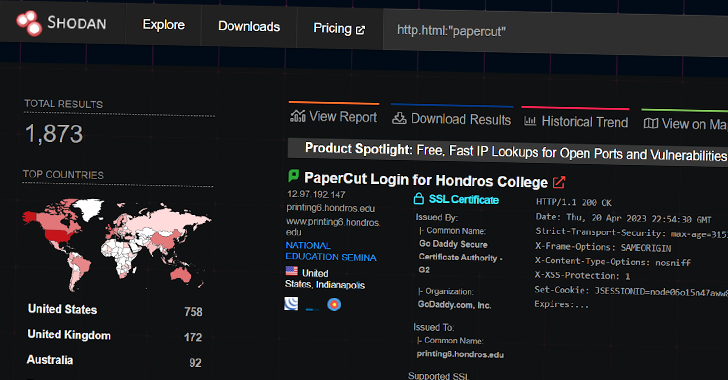
Print management software provider PaperCut said that it has "evidence to suggest that unpatched servers are being...
admin
April 22, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added three security flaws to its Known...
admin
April 22, 2023
Lazarus, the prolific North Korean hacking group behind the cascading supply chain attack targeting 3CX, also breached two...
admin
April 21, 2023
Recently, Andrew Martin, founder and CEO of ControlPlane, released a report entitled Cloud Native and Kubernetes Security...
admin
April 21, 2023
A large-scale attack campaign discovered in the wild has been exploiting Kubernetes (K8s) Role-Based Access Control (RBAC)...
admin
April 21, 2023
Cybersecurity researchers have disclosed details of a now-patched zero-day flaw in Google Cloud Platform (GCP) that could...
admin
April 21, 2023
Cisco and VMware have released security updates to address critical security flaws in their products that could...
admin
April 21, 2023
The supply chain attack targeting 3CX was the result of a prior supply chain compromise associated with...
admin
April 20, 2023
Why is Visibility into OT Environments Crucial?
The significance of Operational Technology (OT) for businesses is undeniable as...
admin
April 20, 2023
The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed...
admin
April 20, 2023
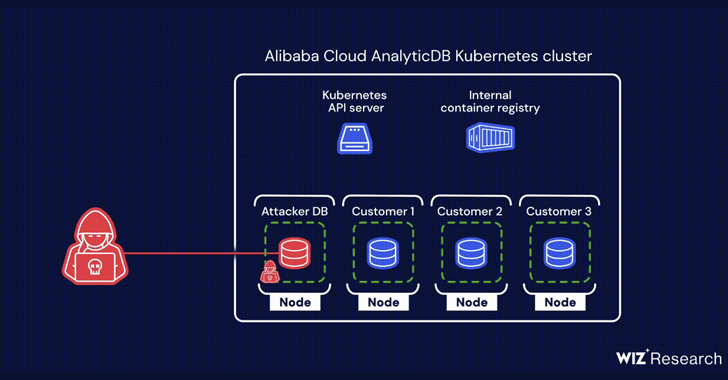
A chain of two critical flaws has been disclosed in Alibaba Cloud's ApsaraDB RDS for PostgreSQL and...
admin
April 20, 2023
Fortra, the company behind Cobalt Strike, shed light on a zero-day remote code execution (RCE) vulnerability in...
admin
April 20, 2023
In the short time since their inception, ChatGPT and other generative AI platforms have rightfully gained the...
admin
April 20, 2023
Telecommunication services providers in Africa are the target of a new campaign orchestrated by a China-linked threat...
admin
April 20, 2023
Israeli spyware maker NSO Group deployed at least three novel "zero-click" exploits against iPhones in 2022 to...