admin
May 27, 2023
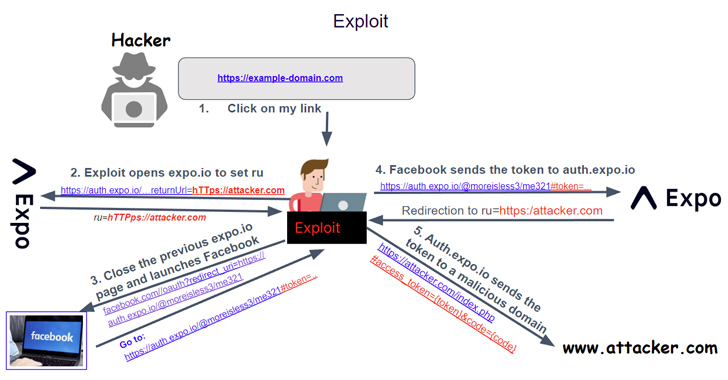
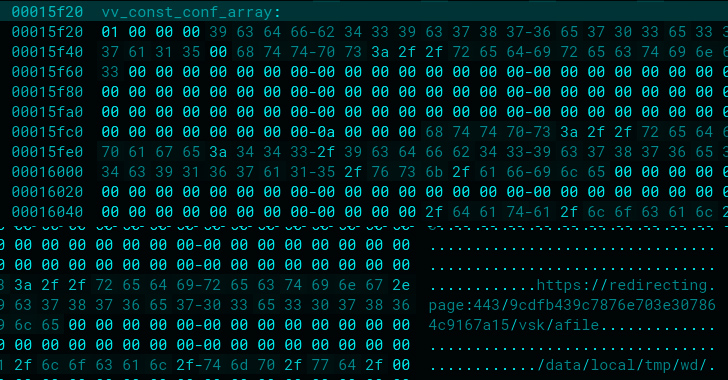
A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development...
admin
May 26, 2023
5G is a game changer for mobile connectivity, including mobile connectivity to the cloud. The technology provides...
admin
May 26, 2023
A new security flaw has been disclosed in the Google Cloud Platform's (GCP) Cloud SQL service that...
admin
May 26, 2023
Security researchers have shared a deep dive into the commercial Android spyware called Predator, which is marketed...
admin
May 26, 2023
A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments...
admin
May 26, 2023
Email protection and network security services provider Barracuda is warning users about a zero-day flaw that it...
admin
May 25, 2023
A new botnet called Dark Frost has been observed launching distributed denial-of-service (DDoS) attacks against the gaming industry.
"The Dark...
admin
May 25, 2023
Zyxel has released software updates to address two critical security flaws affecting select firewall and VPN products...
admin
May 25, 2023
A hospital with 2,000 employees in the E.U. deployed Cynet protections across its environment. The hospital was...
admin
May 25, 2023
An unnamed government entity associated with the United Arab Emirates (U.A.E.) was targeted by a likely Iranian...
admin
May 25, 2023
Google on Wednesday announced the 0.1 Beta version of GUAC (short for Graph for Understanding Artifact Composition) for organizations to secure...
admin
May 25, 2023
A Brazilian threat actor is targeting Portuguese financial institutions with information-stealing malware as part of a long-running...
admin
May 25, 2023
In today's digital landscape, browser security has become an increasingly pressing issue, making it essential for organizations...
admin
May 25, 2023
The threat actors behind the nascent Buhti ransomware have eschewed their custom payload in favor of leaked LockBit and...
admin
May 25, 2023
A stealthy China-based group managed to establish a persistent foothold into critical infrastructure organizations in the U.S....
admin
May 25, 2023
The Iranian threat actor known as Agrius is leveraging a new ransomware strain called Moneybird in its attacks targeting...
admin
May 24, 2023
At least eight websites associated with shipping, logistics, and financial services companies in Israel were targeted as...
admin
May 24, 2023
If you're involved in securing the applications your organization develops, there is no question that Static Application...
admin
May 24, 2023
Google has removed a screen recording app named "iRecorder - Screen Recorder" from the Play Store after...
admin
May 24, 2023
An updated version of the commodity malware called Legion comes with expanded features to compromise SSH servers...