admin
August 28, 2023
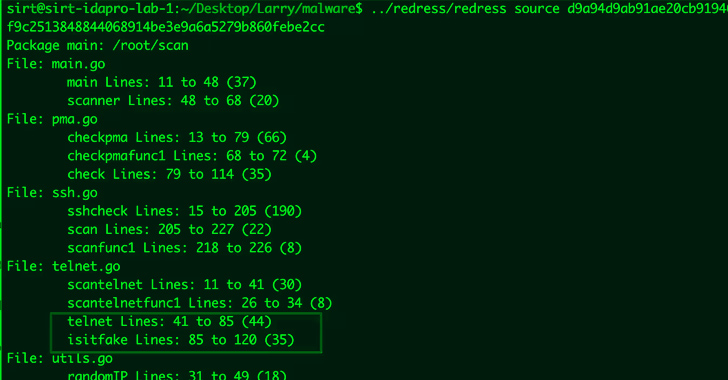
An updated version of a botnet malware called KmsdBot is now targeting Internet of Things (IoT) devices, simultaneously branching...
admin
August 26, 2023
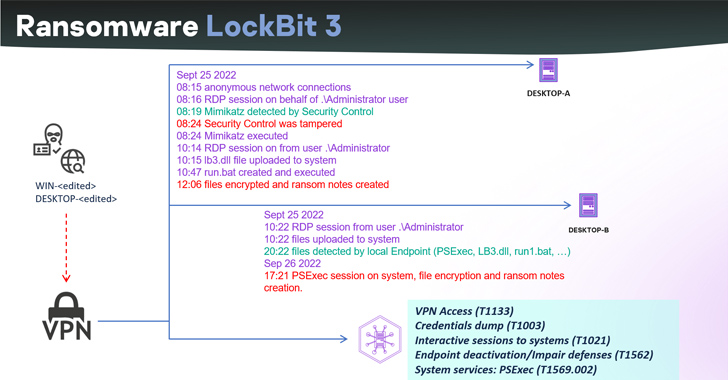
The leak of the LockBit 3.0 ransomware builder last year has led to threat actors abusing the tool to...
admin
August 26, 2023
Risk and financial advisory solutions provider Kroll on Friday disclosed that one of its employees fell victim...
admin
August 25, 2023
In today's digital landscape, your business data is more than just numbers—it's a powerhouse. Imagine leveraging this...
admin
August 25, 2023
Two U.K. teenagers have been convicted by a jury in London for being part of the notorious...
admin
August 25, 2023
Every company has some level of tech debt. Unless you’re a brand new start-up, you most likely...
admin
August 25, 2023
A nation-state activity group originating from China has been linked to cyber attacks on dozens of organizations...
admin
August 25, 2023
The U.S. Federal Bureau of Investigation (FBI) is warning that Barracuda Networks Email Security Gateway (ESG) appliances...
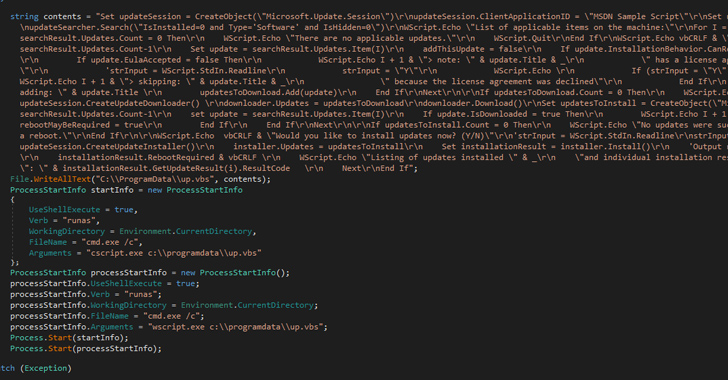
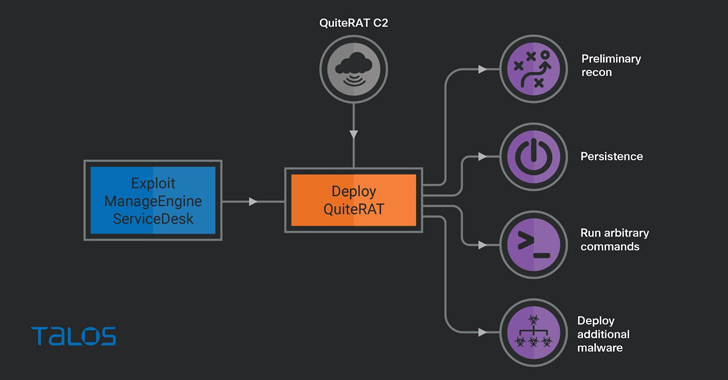
Lazarus Group Exploits Critical Zoho ManageEngine Flaw to Deploy Stealthy QuiteRAT Malware

3 min read
admin
August 24, 2023
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security...
admin
August 24, 2023
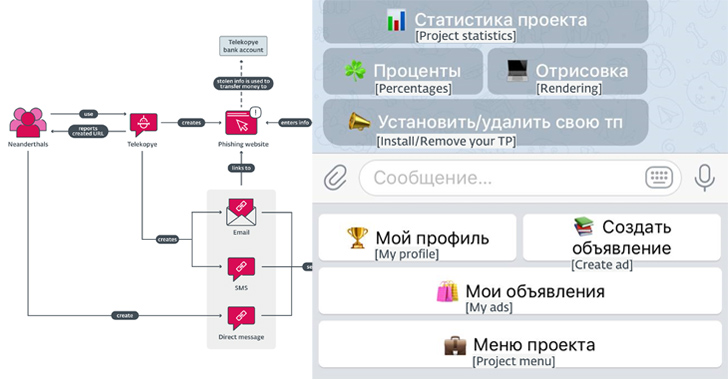
A new financially motivated operation is leveraging a malicious Telegram bot to help threat actors scam their...
admin
August 24, 2023
Public Wi-Fi, which has long since become the norm, poses threats to not only individual users but...
admin
August 24, 2023
The SmokeLoader malware is being used to deliver a new Wi-Fi scanning malware strain called Whiffy Recon on compromised...
admin
August 24, 2023
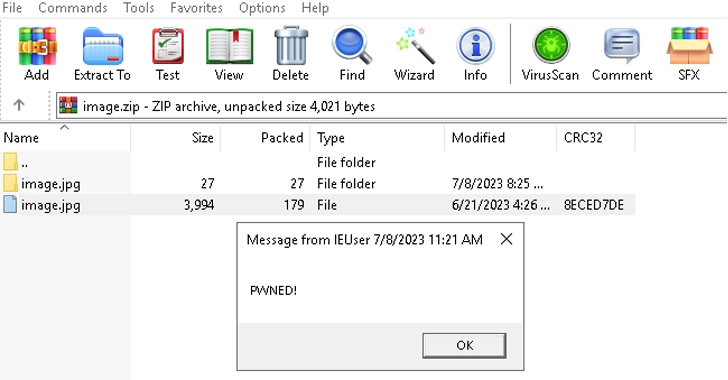
A recently patched security flaw in the popular WinRAR archiving software has been exploited as a zero-day...
admin
August 24, 2023
Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new...
admin
August 24, 2023
The U.S. Justice Department (DoJ) on Wednesday unsealed an indictment against two founders of the now-sanctioned Tornado Cash cryptocurrency...
admin
August 23, 2023
The U.S. Federal Bureau of Investigation (FBI) on Tuesday warned that threat actors affiliated with North Korea...
admin
August 23, 2023
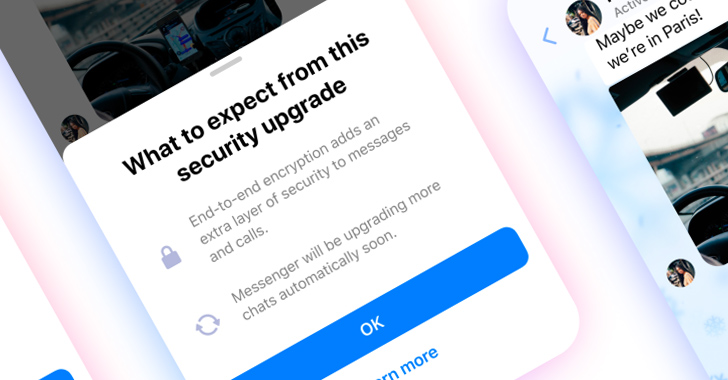
Meta has once again reaffirmed its plans to roll out support for end-to-end encryption (E2EE) by default...
admin
August 23, 2023
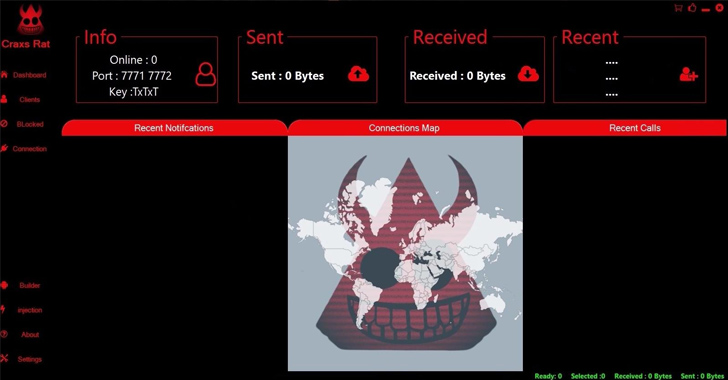
A Syrian threat actor named EVLF has been outed as the creator of malware families CypherRAT and CraxsRAT.
"These RATs...
admin
August 23, 2023
Developers are not the only people who have adopted the agile methodology for their development processes. From...
admin
August 23, 2023
A malicious toolset dubbed Spacecolon is being deployed as part of an ongoing campaign to spread variants of the...