admin
September 12, 2023
Google on Monday rolled out out-of-band security patches to address a critical security flaw in its Chrome...
admin
September 11, 2023
With the growing reliance on web applications and digital platforms, the use of application programming interfaces (APIs)...
admin
September 11, 2023
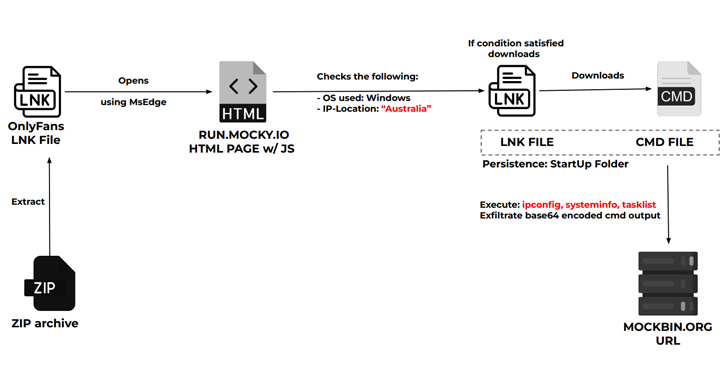
A new phishing attack is leveraging Facebook Messenger to propagate messages with malicious attachments from a "swarm...
admin
September 11, 2023
The Iranian threat actor known as Charming Kitten has been linked to a new wave of attacks targeting different...
Google Chrome Rolls Out Support for ‘Privacy Sandbox’ to Bid Farewell to Tracking Cookies

3 min read
admin
September 11, 2023
Google has officially begun its rollout of Privacy Sandbox in the Chrome web browser to a majority...
admin
September 11, 2023
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool...
admin
September 11, 2023
A new malware loader called HijackLoader is gaining traction among the cybercriminal community to deliver various payloads...
admin
September 9, 2023
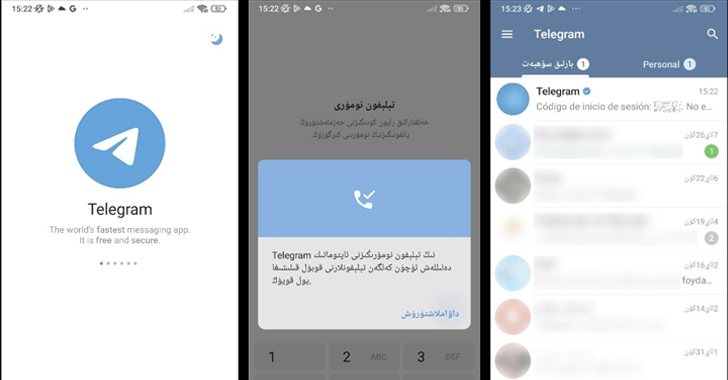
Spyware masquerading as modified versions of Telegram have been spotted in the Google Play Store that’s designed...
admin
September 9, 2023
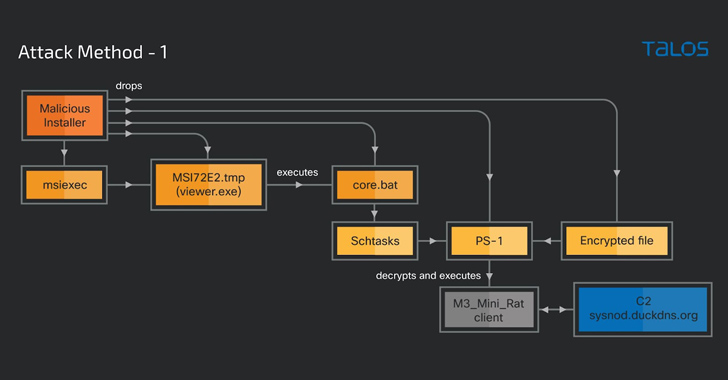
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat...
admin
September 8, 2023
The U.K. and U.S. governments on Thursday sanctioned 11 individuals who are alleged to be part of...
admin
September 8, 2023
Apple on Thursday released emergency security updates for iOS, iPadOS, macOS, and watchOS to address two zero-day...
admin
September 7, 2023
By the end of 2024, the number of MSPs and MSSPs offering vCISO services is expected to...
admin
September 7, 2023
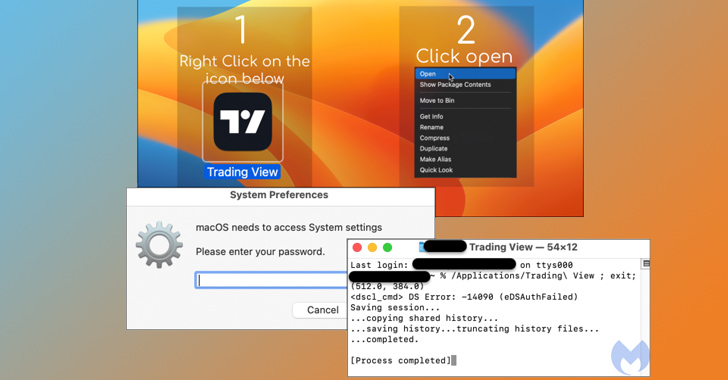
A new malvertising campaign has been observed distributing an updated version of a macOS stealer malware called Atomic...
admin
September 7, 2023
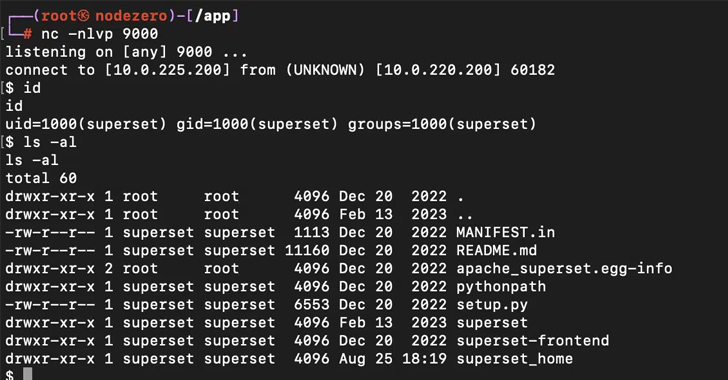
Patches have been released to address two new security vulnerabilities in Apache SuperSet that could be exploited...
admin
September 7, 2023
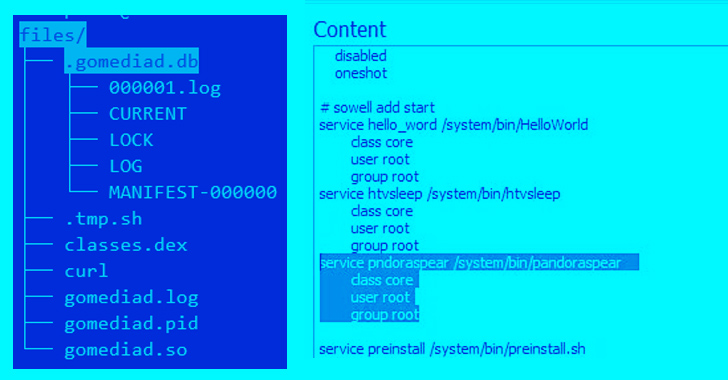
A Mirai botnet variant called Pandora has been observed infiltrating inexpensive Android-based TV sets and TV boxes and using them as...
admin
September 7, 2023
Microsoft on Wednesday revealed that a China-based threat actor known as Storm-0558 acquired the inactive consumer signing key to...
Zero-Day Alert: Latest Android Patch Update Includes Fix for Newly Actively Exploited Flaw


2 min read
admin
September 6, 2023
Google has rolled out monthly security patches for Android to address a number of flaws, including a...
admin
September 6, 2023
The Iranian threat actor tracked as APT34 has been linked to a new phishing attack that leads...
admin
September 6, 2023
The role of the CISO keeps taking center stage as a business enabler: CISOs need to navigate...
admin
September 6, 2023
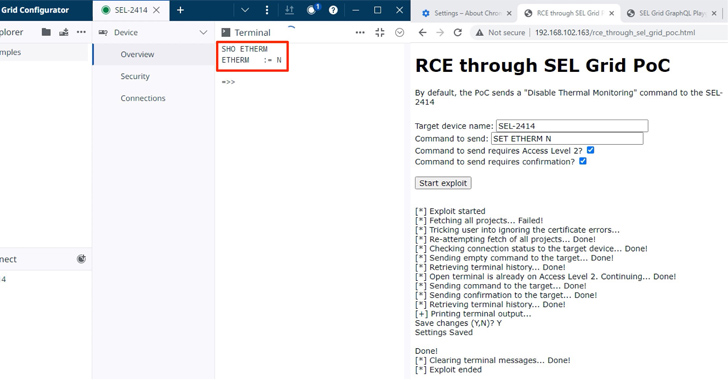
Nine security flaws have been disclosed in electric power management products made by Schweitzer Engineering Laboratories (SEL).
“The...