admin
January 29, 2024
The U.S. National Security Agency (NSA) has admitted to buying internet browsing records from data brokers to...
admin
January 27, 2024
Mexican financial institutions are under the radar of a new spear-phishing campaign that delivers a modified version...
admin
January 26, 2024
Medieval castles stood as impregnable fortresses for centuries, thanks to their meticulous design. Fast forward to the...
admin
January 26, 2024
Chinese-speaking users have been targeted by malicious Google ads for restricted messaging apps like Telegram as part...
admin
January 26, 2024
Microsoft on Thursday said the Russian state-sponsored threat actors responsible for a cyber attack on its systems in late...
admin
January 26, 2024
40-year-old Russian national Vladimir Dunaev has been sentenced to five years and four months in prison for...
admin
January 26, 2024
Cisco has released patches to address a critical security flaw impacting Unified Communications and Contact Center Solutions...
admin
January 25, 2024
The maintainers of the open-source continuous integration/continuous delivery and deployment (CI/CD) automation software Jenkins have resolved nine...
admin
January 25, 2024
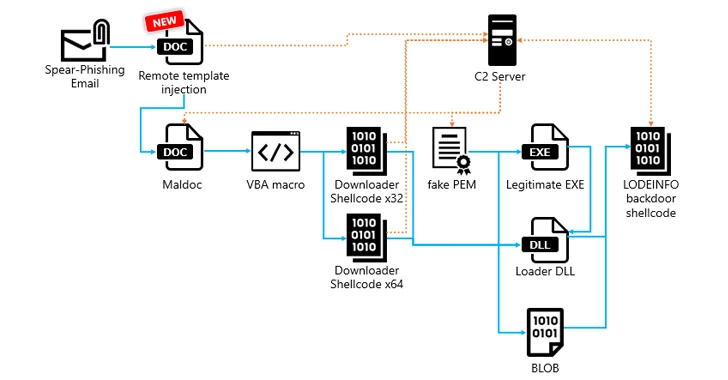
Cybersecurity researchers have uncovered an updated version of a backdoor called LODEINFO that's distributed via spear-phishing attacks.
The findings come...
admin
January 25, 2024
Cybersecurity researchers have shed light on the command-and-control (C2) server of a known malware family called SystemBC.
"SystemBC can...
admin
January 25, 2024
Hackers with links to the Kremlin are suspected to have infiltrated information technology company Hewlett Packard Enterprise's...
admin
January 25, 2024
The 2023/2024 Axur Threat Landscape Report provides a comprehensive analysis of the latest cyber threats. The information...
admin
January 25, 2024
A previously undocumented China-aligned threat actor has been linked to a set of adversary-in-the-middle (AitM) attacks that...
admin
January 25, 2024
A new Go-based malware loader called CherryLoader has been discovered by threat hunters in the wild to deliver additional...
admin
January 24, 2024
In today’s highly distributed workplace, every employee has the ability to act as their own CIO, adopting...
admin
January 24, 2024
The ransomware group known as Kasseika has become the latest to leverage the Bring Your Own Vulnerable...
admin
January 24, 2024
Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Engine (GKE) that could be potentially exploited by...
admin
January 24, 2024
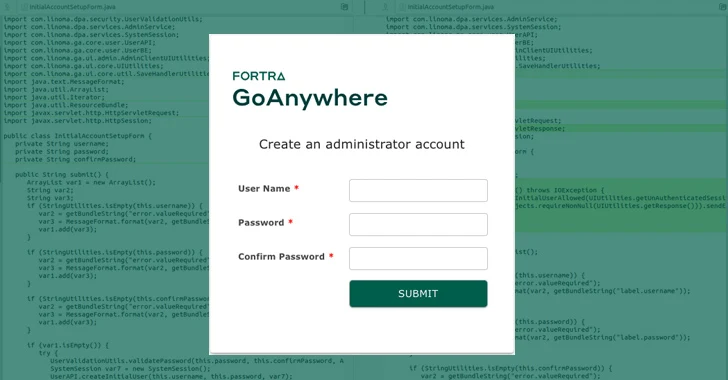
A critical security flaw has been disclosed in Fortra's GoAnywhere Managed File Transfer (MFT) software that could...
admin
January 24, 2024
In a world where more & more organizations are adopting open-source components as foundational blocks in their...
admin
January 24, 2024
Governments from Australia, the U.K., and the U.S. have imposed financial sanctions on a Russian national for...