An analysis of the indicators of compromise (IoCs) associated with the JumpCloud hack has uncovered evidence pointing to the involvement of North Korean state-sponsored groups, in a style that’s reminiscent of the supply chain attack targeting 3CX.
The findings come from SentinelOne, which mapped out the infrastructure pertaining to the intrusion to uncover underlying patterns. It’s worth noting that JumpCloud, last week, attributed the attack to an unnamed “sophisticated nation-state sponsored threat actor.”
“The North Korean threat actors demonstrate a high level of creativity and strategic awareness in their targeting strategies,” SentinelOne security researcher Tom Hegel told The Hacker News. “The research findings reveal a successful and multifaceted approach employed by these actors to infiltrate developer environments.”
“They actively seek access to tools and networks that can serve as gateways to more extensive opportunities. Their tendency to execute multiple levels of supply chain intrusions before engaging in financially motivated theft is noteworthy.”
In a related development, CrowdStrike, which is working with JumpCloud to probe the incident, pinned the attack to a North Korean actor known as Labyrinth Chollima, a sub cluster within the infamous Lazarus Group, according to Reuters.
The infiltration was used as a “springboard” to target cryptocurrency companies, the news agency said, indicating an attempt on part of the adversary to generate illegal revenues for the sanctions-hit nation.
The revelations also coincide with a low-volume social engineering campaign identified by GitHub that targets the personal accounts of employees of technology firms, using a mix of repository invitations and malicious npm package dependencies. The targeted accounts are associated with blockchain, cryptocurrency, online gambling, or cybersecurity sectors.
The Microsoft subsidiary connected the campaign to a North Korean hacking group it tracks under the name Jade Sleet (aka TraderTraitor).
“Jade Sleet mostly targets users associated with cryptocurrency and other blockchain-related organizations, but also targets vendors used by those firms,” GitHub’s Alexis Wales said in a report published on July 18, 2023.
The attack chains involve setting up bogus personas on GitHub and other social media services such as LinkedIn, Slack, and Telegram, although in some cases the threat actor is believed to have taken control of legitimate accounts.
Under the assumed persona, Jade Sleet initiates contact with the targets and invites them to collaborate on a GitHub repository, convincing the victims into cloning and running the contents, which feature decoy software with malicious npm dependencies that act as first-stage malware to download and execute second-stage payloads on the infected machine.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
The malicious npm packages, per GitHub, are part of a campaign that first came to light last month, when Phylum detailed a supply chain threat involving a unique execution chain that uses a pair of fraudulent modules to fetch an unknown piece of malware from a remote server.
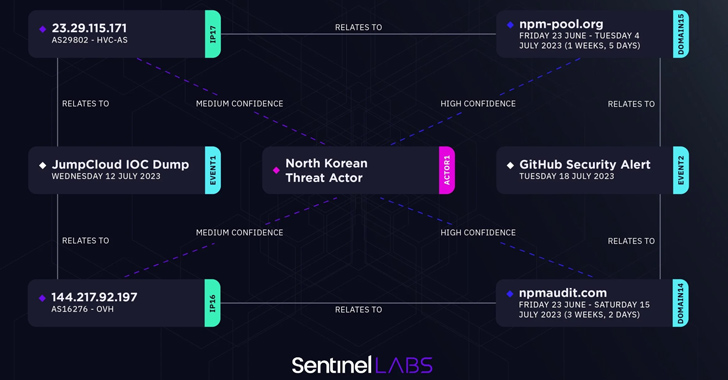
SentinelOne, in its latest analysis, said 144.217.92[.]197, an IP address linked to the JumpCloud attack, resolves to npmaudit[.]com, one of the eight domains listed by GitHub as used to fetch the second-stage malware. A second IP address 23.29.115[.]171 maps to npm-pool[.]org.
“It is evident that North Korean threat actors are continuously adapting and exploring novel methods to infiltrate targeted networks,” Hegel said. “The JumpCloud intrusion serves as a clear illustration of their inclination towards supply chain targeting, which yields a multitude of potential subsequent intrusions.”
“The DPRK demonstrates a profound understanding of the benefits derived from meticulously selecting high-value targets as a pivot point to conduct supply chain attacks into fruitful networks,” Hegel added.









