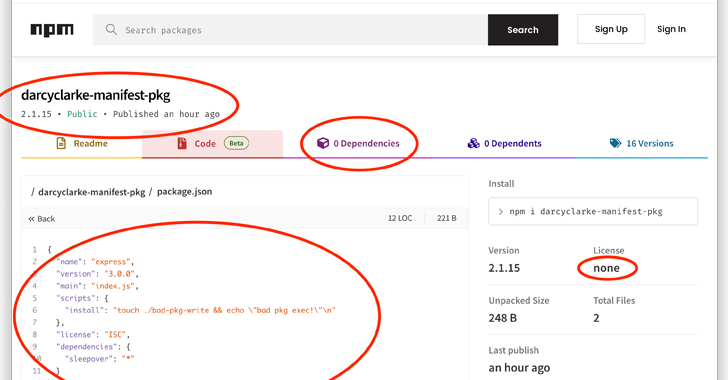
The npm registry for the Node.js JavaScript runtime environment is susceptible to what’s called a manifest confusion attack that could potentially allow threat actors to conceal malware in project dependencies or perform arbitrary script execution during installation.
“A npm package’s manifest is published independently from its tarball,” Darcy Clarke, a former GitHub and npm engineering manager, said in a technical write-up published last week. “Manifests are never fully validated against the tarball’s contents.”
“The ecosystem has broadly assumed the contents of the manifest and tarball are consistent,” Clarke added.
The problem, at its core, stems from the fact that the manifest and package metadata are decoupled and that they are never cross-referenced against one another, thereby leading to unexpected behavior and misuse when there is a mismatch.
As a result, a threat actor could exploit this loophole to publish a module with a manifest file (package.json) that contains hidden dependencies as well as run install scripts, which could then pave the way for a supply chain attack and the poisoning of a developer’s environment.
“Manifest confusion becomes problematic in development environments without effective DevSecOps workflows and tooling in place, especially when applications blindly trust application manifests rather than the actual (vulnerable or malicious) files contained within open source packages,” Sonatype researcher and journalist Ax Sharma said.
The finding underscores the fact that metadata contained within package manifest files alone cannot be relied upon when downloading a package from the open-source repository, necessitating that users take steps to scan packages for any anomalous features and exploits.
GitHub, per Clarke, is said to be aware of the problem since at least early November 2022, with the Microsoft subsidiary stating it plans to address it internally as of March 2023. The issue, however, remains unresolved to date.
In the absence of an official fix, security researcher Felix Pankratz has made available a Python script that can be used to test for mismatches between the manifests in npm modules.
The development also comes as developer security company Snyk, in partnership with Redhunt Labs, examined 11,900 repositories from the top 1,000 GitHub organizations for insecure dependencies, uncovering 1,229,601 flaws in 15,584 vulnerable dependency files.
“Deserialization of untrusted data was the most prevalent vulnerability type with a whopping 130,831 occurrences in Java repositories, making it 40 percent of the total vulnerabilities identified,” the study said.
In JavaScript-based projects, prototype pollution emerged as the leading shortcoming with 343,332 occurrences. Denial-of-service (DoS) flaws contributed to the most in Python and Ruby projects with 19,652 and 56,331 occurrences, respectively.
“The threat of vulnerable dependencies disrupting the state of security of software supply chains is here to stay,” security researchers Umair Nehri and Vandana Verma Sehgal said. “So, developers must be careful with the dependencies they use in their projects and keep them up-to-date to keep them patched from any known vulnerabilities.”






