A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control (GC2) amid broader abuse of Google’s infrastructure for malicious ends.
The tech giant’s Threat Analysis Group (TAG) attributed the campaign to a threat actor it tracks under the geological and geographical-themed moniker HOODOO, which is also known by the names APT41, Barium, Bronze Atlas, Wicked Panda, and Winnti.
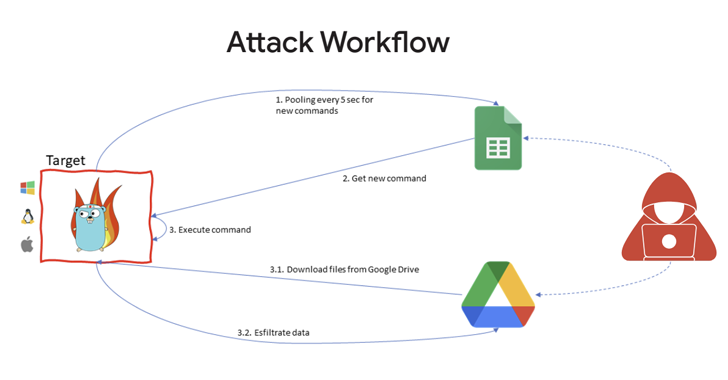
The starting point of the attack is a phishing email that contains links to a password-protected file hosted on Google Drive, which, in turn, incorporates the GC2 tool to read commands from Google Sheets and exfiltrate data using the cloud storage service.
“After installation on the victim machine, the malware queries Google Sheets to obtain attacker commands,” Google’s cloud division said in its sixth Threat Horizons Report. “In addition to exfiltration via Drive, GC2 enables the attacker to download additional files from Drive onto the victim system.”
Google said the threat actor previously utilized the same malware in July 2022 to target an Italian job search website.
The development is notable for two reasons: First, it suggests that Chinese threat groups are increasingly relying on publicly available tooling like Cobalt Strike and GC2 to confuse attribution efforts.
Secondly, it also points to the growing adoption of malware and tools written in the Go programming language, owing to its cross-platform compatibility and its modular nature.
Google further cautioned that the “undeniable value of cloud services” have made them a lucrative target for cybercriminals and government-backed actors alike, “either as hosts for malware or providing the infrastructure for command-and-control (C2).”
Master the Art of Dark Web Intelligence Gathering
Learn the art of extracting threat intelligence from the dark web – Join this expert-led webinar!
A case in point is the use of Google Drive for storing malware such as Ursnif (aka Gozi) and DICELOADER (aka Lizar or Tirion) in the form of ZIP archive files as part of disparate phishing campaigns.
“The most common vector used to compromise any network, including cloud instances is to take over an account’s credentials directly: either because there is no password, as with some default configurations, or because a credential has been leaked or recycled or is generally so weak as to be guessable,” Google Cloud’s Christopher Porter said.
The findings come three months after Google Cloud detailed APT10’s (aka Bronze Riverside, Cicada, Potassium, or Stone Panda) targeting of cloud infrastructure and VPN technologies to breach enterprise environments and exfiltrate data of interest.










