The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages.
APT28, also known by the names BlueDelta, Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422, is an advanced persistent threat (APT) group affiliated with Russia’s strategic military intelligence unit, the GRU.
The hacking crew operates with a high level of stealth and sophistication, often demonstrating their adaptability through deep preparedness and custom tooling, and relying on legitimate internet services (LIS) and living off-the-land binaries (LOLBins) to conceal their operations within regular network traffic.
“From April to December 2023, BlueDelta deployed Headlace malware in three distinct phases using geofencing techniques to target networks throughout Europe with a heavy focus on Ukraine,” Recorded Future’s Insikt Group said.
“BlueDelta’s espionage activities reflect a broader strategy aimed at gathering intelligence on entities with military significance to Russia in the context of its ongoing aggression against Ukraine.”
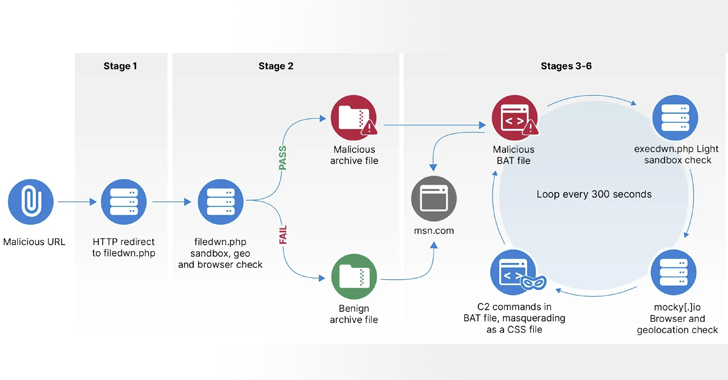
HeadLace, as previously documented by the Computer Emergency Response Team of Ukraine (CERT-UA), Zscaler, Proofpoint, and IBM X-Force, is distributed via spear-phishing emails containing malicious links that, when clicked, initiate a multi-stage infection sequence to drop the malware.
BlueDelta is said to have employed a seven-stage infrastructure chain during the first phase to deliver a malicious Windows BAT script (i.e., HeadLace) that’s capable of downloading and running follow-on shell commands, subject to sandbox and geofencing checks.
The second phase, which commenced on September 28, 2023, is notable for using GitHub as the starting point of the redirection infrastructure, while the third phase switched to using PHP scripts hosted on InfinityFree beginning October 17, 2023.
“The last detected activity in phase three was in December2023,” the company said. “Since then, BlueDelta likely ceased using InfinityFree hosting and favored hosting infrastructure on webhook[.]site and mocky[.]io directly.”
BlueDelta has also been found to undertake credential harvesting operations designed to target services like Yahoo! and UKR[.]net by serving lookalike pages and ultimately trick victims into entering their credentials.
Another technique involved creating dedicated web pages on Mocky that interact with a Python script running on compromised Ubiquiti routers to exfiltrate the entered credentials. Earlier this February, a U.S.-led law enforcement operation disrupted a botnet comprising Ubiquiti EdgeRouters that was put to use by APT28 for this purpose.
Targets of the credential harvesting activity included the Ukrainian Ministry of Defence, Ukrainian weapons import and export companies, European railway infrastructure, and a think tank based in Azerbaijan.
“Successfully infiltrating networks associated with Ukraine’s Ministry of Defence and European railway systems could allow BlueDelta to gather intelligence that potentially shapes battlefield tactics and broader military strategies,” Recorded Future said.
“Moreover, BlueDelta’s interest in the Azerbaijan Center for Economic and Social Development suggests an agenda to understand and possibly influence regional policies.”
The development comes as another state-sponsored Russian threat group called Turla has been observed leveraging human rights seminar invitations as phishing email decoys to execute a payload similar to the TinyTurla backdoor using the Microsoft Build Engine (MSBuild).




