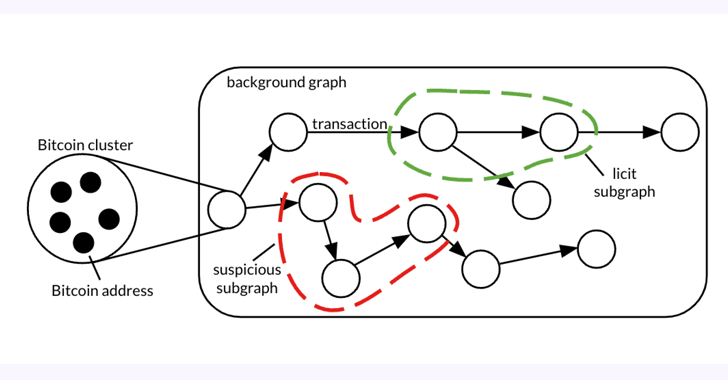
A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market.
The findings come from Elliptic in collaboration with researchers from the MIT-IBM Watson AI Lab.
The 26 GB dataset, dubbed Elliptic2, is a “large graph dataset containing 122K labeled subgraphs of Bitcoin clusters within a background graph consisting of 49M node clusters and 196M edge transactions,” the co-authors said in a paper shared with The Hacker News.
Elliptic2 builds on the Elliptic Data Set (aka Elliptic1), a transaction graph that was made public in July 2019 with the goal of combating financial crime using graph convolutional neural networks (GCNs).
The idea, in a nutshell, is to uncover illicit activity and money laundering patterns by taking advantage of blockchain’s pseudonymity and combining it with knowledge about the presence of licit (e.g., exchange, wallet provider, miner, etc.) and illicit services (e.g., darknet market, malware, terrorist organizations, Ponzi scheme, etc.) on the network.
“Using machine learning at the subgraph level – i.e., the groups of transactions that make up instances of money laundering – can be effective at predicting whether crypto transactions constitute proceeds of crime,” Tom Robinson, chief scientist and co-founder of Elliptic, told The Hacker News.
“This is different to conventional crypto AML solutions, which rely on tracing funds from known illicit wallets, or pattern-matching with known money laundering practices.”
The study, which experimented with three different subgraph classification methods on Elliptic2, such as GNN-Seg, Sub2Vec, and GLASS, identified subgraphs that represented crypto exchange accounts potentially engaged in illegitimate activity.
Furthermore, it has made it possible to trace back the source of funds associated with suspicious subgraphs to various entities, including a cryptocurrency mixer, a Panama-based Ponzi scheme, and an invite-only Russian dark web forum.
Robinson said just considering the “shape” – the local structures within a complex network – of the money laundering subgraphs proved to be an already effective way to flag criminal activity.
Further examination of the subgraphs predicted using the trained GLASS model has also identified known cryptocurrency laundering patterns, such as the presence of peeling chains and nested services.
“A peeling chain is where a small amount of cryptocurrency is ‘peeled’ to a destination address, while the remainder is sent to another address under the user’s control,” Robinson explained. “This happens repeatedly to form a peeling chain. The pattern can have legitimate financial privacy purposes, but it can also be indicative of money laundering, especially where the ‘peeled’ cryptocurrency is repeatedly sent to an exchange service.”
“This is a known crypto laundering technique and has an analogy in ‘smurfing’ within traditional finance – so the fact that our machine learning mode independently identified it is encouraging.”
As for the next steps, the research is expected to focus on increasing the accuracy and precision of these techniques, as well as extending the work to further blockchains, Robinson added.



![5 Threats That Reshaped Web Security This Year [2025]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjQ51hMVtHfFQ2O7pCZYfK5WkypXg1Qury_AA_VudY5f_n7u8S8M4UJAy76w7DM1aBq1faDyuaOO4VJP7bIj1L1-AgNzZjQf0-kZlhU6kH-G4qDMkZFF_7YsL3v5R6d9PkpJcTegD7H01BySWNNs-m5toA_DTqVSVs-sCeLm5n1zJuLzs1_erWdl8asq4k/s790-rw-e365/reflectiz.jpg)


