Have you heard about Dependabot? If not, just ask any developer around you, and they’ll likely rave about how it has revolutionized the tedious task of checking and updating outdated dependencies in software projects.
Dependabot not only takes care of the checks for you, but also provides suggestions for modifications that can be approved with just a single click. Although Dependabot is limited to GitHub-hosted projects, it has set a new standard for continuous providers to offer similar capabilities. This automation of “administrative” tasks has become a norm, enabling developers to integrate and deploy their work faster than ever before. Continuous integration and deployment workflows have become the cornerstone of software engineering, propelling the DevOps movement to the forefront of the industry.
But a recent advisory by security firm Checkmarx sheds light on a concerning incident. Malicious actors have recently attempted to exploit the trust associated with Dependabot by impersonating the tool. By mimicking the suggestions made by Dependabot (in the form of pull requests), these actors tried to deceive developers into accepting changes without giving them a second thought.
While Dependabot exemplifies the advancements in automating software maintenance tasks, this incident also underscores the broader complexities and vulnerabilities inherent in CI/CD pipelines. These pipelines serve as vital conduits, linking the external world of software development tools and platforms with the internal processes of software creation and deployment. Understanding this connection is key to addressing the security challenges we face.
CI/CD Pipelines: Connecting the Outside World with the Internal One
Continuous integration (CI) and deployment (CD) workflows have revolutionized the software development process, providing developers with the ability to seamlessly merge their work and deploy it to the production environment. These workflows ensure that the code undergoes automated security scans, rigorous testing, and adherence to coding standards, resulting in a more efficient and reliable development process. They have become a catalyst for innovation, enabling teams to focus on building and enhancing their products with the assurance of quality and security.
To illustrate the concept, imagine building a puzzle. CI acts as a vigilant checker, verifying that each new puzzle piece fits correctly before moving forward. On the other hand, CD takes this a step further by automatically placing each verified piece into the final puzzle, eliminating the need to wait for the entire puzzle to be completed. This accelerated process allows for faster feature delivery and ultimately expedites the overall product development timeline.
However, these CI/CD workflows also connect the outside world with the internal development environment, creating potential risks. For instance, consider a scenario where a developer integrates a third-party library into their project through a CI/CD pipeline. If the developer fails to thoroughly vet the library or if the pipeline lacks proper security checks, malicious code could be unknowingly incorporated into the project, compromising its integrity. In recent years, there has been a rise in attacks such as typosquatting and dependency confusion, which aim to exploit the reliance on open source software for financial gain.
The rise of automated integrations workflows have changed the economics for attackers by lowering the cost and increasing the potential gains of an attack. Attackers can target popular central package repositories like PyPi, which hosts thousands of packages and serves millions of downloads daily. The sheer scale of operations makes it economically viable for attackers to try their luck, even with a small chance of success.
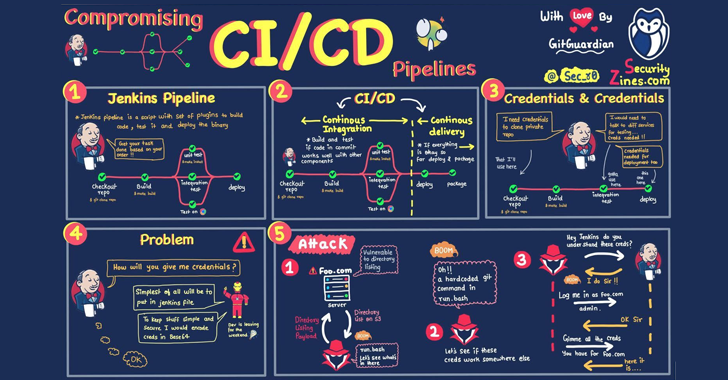
Another example is the use of external APIs within CI/CD pipelines. Developers often need to provide valid credentials for these APIs to enable automated deployment or integration with external services. However, if these credentials are not securely managed or if they are inadvertently exposed in logs or artifacts, they can be exploited by attackers to gain unauthorized access to sensitive resources or manipulate the pipeline’s behavior.
CI/CD breaches frequently stem from either an initial compromise of secrets or developers becoming targets of specific attacks. However, rather than blaming developers for these breaches, it is crucial to recognize that the issue lies in the inherent lack of security in these pipelines. This highlights a larger problem: CI/CD pipelines are far from being secure by default.
The Problem: CI/CD Pipelines Are Far from Secure by Default
Although the idea of implementing secure-by-design workflows is becoming more popular, CI/CD platforms still have a significant way to go. Platforms like GitHub Actions, GitLab CI/CD, and CircleCI, which were initially designed with flexibility in mind, often prioritize ease of use over robust security measures. As a result, there is a lack of default safeguards to prevent potential issues from arising.
A glaring example of this is how easy it is for a developer to expose sensitive information like secrets. Developers commonly inject secrets at runtime and rely for that on the capability to store secrets in the CI provider itself. While this practice isn’t a problem by itself, it raises at least two security concerns: first, the CI provider hosting the secrets becomes a vault of sensitive information and an attractive target for attackers. As recently as early 2023, CircleCI suffered a breach of its systems which forced users to rotate “any and all” their secrets following a breach of the company’s systems.
Second, secrets can often leak and go unnoticed through CI/CD pipelines themselves. For example, if a secret is concatenated with another string (say, a URL) and then logged, the CI redacting mechanism will not work. Same goes with encoded secrets. The consequence is that CI logs often expose plaintext secrets. Similarly, it is not uncommon at all to find secrets hard-coded in software artifacts, being the result of a misconfigured continuous integration workflow.
CI/CD providers have already taken steps to enhance security, like GitHub Dependabot security checks. But most of the time, permissive defaults and complex permission models are still the rule. To protect CI/CD pipelines and prevent code compromise, developers should take additional measures to harden their pipelines against attacks. One crucial aspect is ensuring the protection of developers’ credentials. Another one is to take a proactive approach to security with alert triggers.
Safeguarding CI/CD and the Software Supply Chain
To effectively secure CI/CD pipelines, it’s crucial to view them as high-priority, potentially externally connected environments. The key is a mix of best practices:
- Restrict Access and Minimize Privileges: Grant access based on necessity, not convenience. Extensive access to all DevOps team members increases the risk of a compromised account providing attackers with extensive system access. Limit access to critical controls, configurations, or sensitive data.
- Enforce Multi-Factor Authentication (MFA): Crucially, always use multi-factor authentication (MFA) for logging into the CI/CD platform. MFA adds an essential layer of security, making it significantly harder for unauthorized users to gain access even if they have compromised credentials.
- Utilize OpenID Connect (OIDC): Employ OIDC for securely connecting workloads to external systems, such as for deployment. This protocol provides a robust framework for authentication and cross-domain identity verification, which is critical in a distributed and interconnected environment.
- Use Pre-Reviewed Software Dependencies: It’s important to provide developers with safe, pre-reviewed software dependencies. This practice safeguards the supply chain’s integrity and spares developers from having to verify each package’s code. This ensures supply chain integrity, relieving developers from the burden of individually verifying each package’s code.
- Secure Runtime Secrets: Safely storing secrets like API keys and credentials in the CI/CD platform requires strong security measures, such as enforced MFA and role-based access controls (RBAC). However, these are not foolproof. Secrets are leaky by nature, and additional layers of security, like rigorous credential hygiene and vigilant monitoring of internal and external threats, are necessary for comprehensive protection.
- Implement Advanced Defense Systems: Incorporate alert systems into your security framework. While honeypots are effective but challenging to scale, honeytokens offer a scalable, easy-to-implement alternative. These tokens, requiring minimal setup, can significantly enhance security for companies of all sizes across various platforms like SCM systems, CI/CD pipelines, and software artifact registries.
- Leverage Enterprise-Scale Solutions: Solutions like the GitGuardian Platform offer a single pane of glass to monitor incidents such as leaked secrets, Infrastructure as Code misconfigurations and honeytoken triggers, allowing organizations to detect, remediate and prevent CI/CD incidents on a large scale. This significantly mitigates the impact of potential data breaches.
By combining these strategies, organizations can comprehensively safeguard their CI/CD pipelines and software supply chain, adapting to evolving threats and maintaining robust security protocols. Get started securing your pipelines today with the GitGuardian Platform.









