An updated version of an Android banking trojan called Xenomorph has set its sights on more than 35 financial institutions in the U.S.
The campaign, according to Dutch security firm ThreatFabric, leverages phishing web pages that are designed to entice victims into installing malicious Android apps that target a broader list of apps than its predecessors. Some of the other targeted prominent countries targeted comprise Spain, Canada, Italy, and Belgium.
“This new list adds dozens of new overlays for institutions from the United States, Portugal, and multiple crypto wallets, following a trend that has been consistent amongst all banking malware families in the last year,” the company said in an analysis published Monday.
Xenomorph is a variant of another banker malware called Alien which first emerged in 2022. Later that year, the financial malware was propagated via a new dropper dubbed BugDrop, which bypassed security features in Android 13.
A subsequent iteration spotted earlier this March came fitted with features to conduct fraud using what’s known as the Automatic Transfer System (ATS).
The feature allows its operators, named Hadoken Security, to completely seize control over the device by abusing Android’s accessibility privileges and illicitly transfer funds from the compromised device to an actor-controlled account.
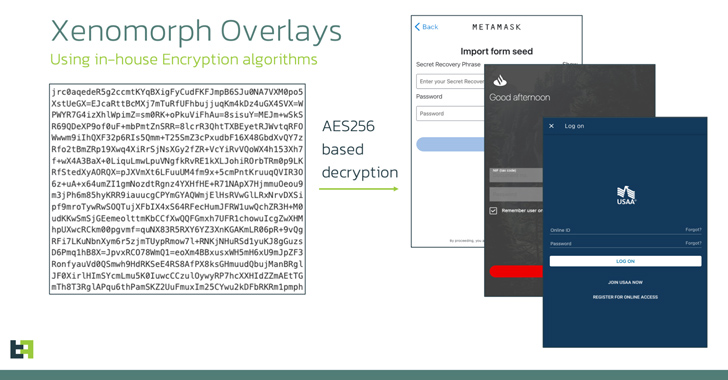
The malware also leverages overlay attacks to steal sensitive information such as credentials and credit card numbers by displaying fake login screens on top of the targeted bank apps. The overlays are retrieved from a remote server in the form of a list of URLs.
In other words, the ATS framework makes it possible to automatically extract credentials, access account balance information, initiate transactions, obtain MFA tokens from authenticator apps, and perform fund transfers, all without the need for any human intervention.
“Actors have put a lot of effort into modules that support Samsung and Xiaomi devices,” the researchers said. “This makes sense, considering that these two combined make up roughly 50% of the whole Android market share.”
Some of the new capabilities added to the latest versions of Xenomorph include an “antisleep” feature that prevents the phone’s screen from turning off by creating an active push notification, an option to simulate a simple touch at a specific screen coordinate, and impersonate another app using a “mimic” feature.
Fight AI with AI — Battling Cyber Threats with Next-Gen AI Tools
Ready to tackle new AI-driven cybersecurity challenges? Join our insightful webinar with Zscaler to address the growing threat of generative AI in cybersecurity.
As a way to bypass detection for long periods of time, the malware hides its icon from the home screen launcher upon installation. The abuse of the accessibility services further allows it to grant itself all the permissions it needs to run unimpeded on a compromised device.
Previous versions of the banking trojan have masqueraded as legitimate apps and utilities on the Google Play Store. But the latest attack wave observed in mid-August 2023 switches up the modus operandi by distributing the apps through counterfeit sites offering Chrome browser updates.
In a sign that the threat actors are targeting multiple operating systems, the investigation found that the payload hosting infrastructure is also being used to serve Windows stealer malware such as Lumma C2 and RisePro, as well as a malware loader referred to as Private Loader.
“Xenomorph maintains its status as an extremely dangerous Android banking malware, featuring a very versatile and powerful ATS engine, with multiple modules already created, with the idea of supporting multiple manufacturer’s devices,” ThreatFabric said.




