A new malvertising campaign has been observed distributing an updated version of a macOS stealer malware called Atomic Stealer (or AMOS), indicating that it’s being actively maintained by its author.
An off-the-shelf Golang malware available for $1,000 per month, Atomic Stealer first came to light in April 2023. Shortly after that, new variants with an expanded set of information-gathering features were detected in the wild, targeting gamers and cryptocurrency users.
Malvertising via Google Ads has been observed as the primary distribution vector in which users searching for popular software, legitimate or cracked, on search engines are shown bogus ads that direct to websites hosting rogue installers.
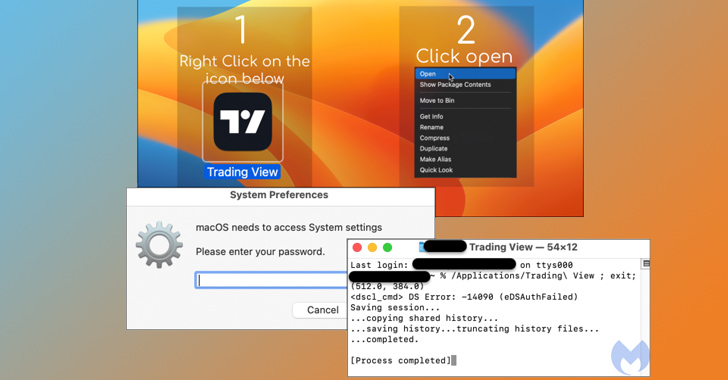
The latest campaign involves the use of a fraudulent website for TradingView, prominently featuring three buttons to download the software for Windows, macOS, and Linux operating systems.
“Both the Windows and Linux buttons point to an MSIX installer hosted on Discord that drops NetSupport RAT,” Jérôme Segura, director of threat intelligence at Malwarebytes, said.
The macOS payload (“TradingView.dmg”) is a new version of Atomic Stealer released at the end of June, which is bundled in an ad-hoc signed app that, once executed, prompts users to enter their password on a fake prompt and harvest files as well as data stored in iCloud Keychain and web browsers.
“Atomic stealer also targets both Chrome and Firefox browsers and has an extensive hardcoded list of crypto-related browser extensions to attack,” SentinelOne previously noted in May 2023. Select variants have also targeted Coinomi wallets.
The ultimate goal of the attacker is to bypass Gatekeeper protections in macOS and exfiltrate the stolen information to a server under their control.
The development comes as macOS is increasingly becoming a viable target of malware attacks, with a number of macOS-specific info stealers appearing for sale in crimeware forums in recent months to take advantage of the wide availability of Apple systems in organizations.
Way Too Vulnerable: Uncovering the State of the Identity Attack Surface
Achieved MFA? PAM? Service account protection? Find out how well-equipped your organization truly is against identity threats
“While Mac malware really does exist, it tends to be less detected than its Windows counterpart,” Segura said. “The developer or seller for AMOS actually made it a selling point that their toolkit is capable of evading detection.”
Atomic Stealer is not the only malware propagated via malvertising and search engine optimization (SEO) poisoning campaigns, as evidence has emerged of DarkGate (aka MehCrypter) latching onto the same delivery mechanism.
New versions of DarkGate have since been employed in attacks mounted by threat actors employing tactics similar to that of Scattered Spider, Aon’s Stroz Friedberg Incident Response Services said last month.






