Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning and enforcing security policies for all network endpoints. With it, users can access various resources across networks. As things tend to do, times, they are a’changin’ – and a few years back, Microsoft introduced Azure Active Directory, the cloud-based version of AD to extend the AD paradigm, providing organizations with an Identity-as-a-Service (IDaaS) solution across both the cloud and on-prem apps. (Note that as of July 11th 2023, this service was renamed to Microsoft Entra ID, but for the sake of simplicity, we’ll refer to it as Azure AD in this post)
Both Active Directory and Azure AD are critical to the functioning of on-prem, cloud-based, and hybrid ecosystems, playing a key role in uptime and business continuity. And with 90% of organizations using the service for employee authentication, access control and ID management, it has become the keys to the proverbial castle.
Active Directory, Actively Problematic
But as central as it is, Active Directory security posture is often woefully lacking.
Let’s take a quick peek at how Active Directory assigns users, which will shed some light on why this tool has some shall we say, issues, associated with it.
At the core, what Active Directory does is establish groups that have roles and authorizations associated with them. Users are assigned a username and password, which is then linked to their Active Directory Account Object. Using Lightweight Directory Access Protocol, passwords are verified as correct or incorrect and the usergroup is also verified. In general, users are assigned to the Domain User group and will be granted access to the objects that domain users have authorization to access. Then there are Admins – these are users assigned to the Domain Admins group. This group is highly privileged and is thus authorized to perform any actions in the network.
With such potentially potent capabilities, it’s super critical to ensure that Active Directory is managed and configured optimally. Issues like missed patches, poor access management and misconfigurations can allow attackers to access even the most sensitive systems, which can have dire consequences.
In 2022, our in-house research found that 73% of the top attack techniques used in the compromising of critical assets involved mismanaged or stolen credentials – and more than half of the attacks in organizations include some element of Active Directory compromise. And once they have a foothold in Active Directory, attackers can perform loads of different malicious actions like:
- Hiding activity in the network
- Executing malicious code
- Elevating privileges
- Getting into the cloud environment to compromise critical assets
Point is, if you don’t know what’s happening in your Active Directory, and if you’re lacking the proper processes and security controls, you’re likely leaving the door wide open to attackers.
Download our latest research report, and discover
- How many steps it takes for attackers to typically compromise your critical assets
- Top exposures and hygiene issues that form attack paths
- Key findings related to attacks across hybrid, on-prem or multi-cloud networks.
Active Directory Attack Paths
From an attacker’s POV, Active Directory serves as a great opportunity for conducting lateral movement, as gaining that initial access allows them to move from a low-privileged user to a more valuable target – or even to fully take over – by exploiting misconfigurations or overly excessive permissions.
So now let’s take a look into the anatomy of 3 actual Active Directory attack paths and see how attackers made their way through this environment.
Here is an attack path we came across in one of our customer’s environment:
The organization was deeply committed to hardening their security posture but Active Directory was a blind spot. In this case, all authenticated users – essentially any users at all – in the domain had been accidentally granted the right to reset passwords. So if an attacker took over one Active Directory user via phishing or other social engineering techniques, they could then reset any passwords for other users and take over any account in the domain.Once they saw this, they finally understood their Active Directory security approach needed to level-up so they locked down and hardened their security practices.
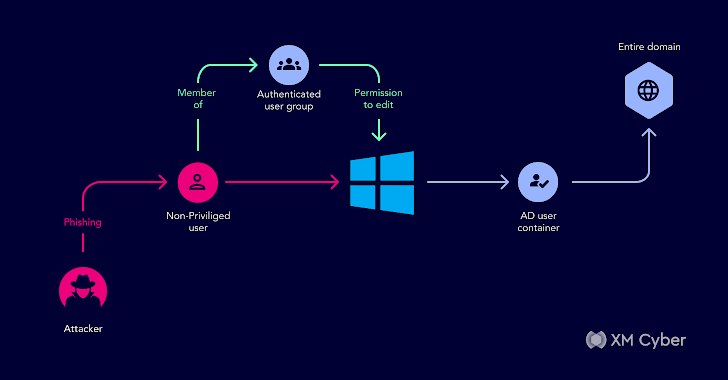
Here’s another one from one of our customer’s Active Directory;
We uncovered an attack path using the authenticated users group with permissions to change the GPO policy’s gPCFileSysPath to a path with malicious policies.
One of the affected objects was the AD User Container, with a child object that was a user which was part of the Domain Admin group. Any user in the domain could get Domain Admin permissions — all they needed was one non-privileged user to fall prey to a phishing email to compromise the entire domain. This could have led to a complete compromise of their domain.
Ready for one more? Here it is:
This one starts with an attacker infiltrating an enterprise environment via phishing mail that when opened, executed code using a vulnerability on an unpatched machine. The next step exploited the compromised Active Directory user’s local and domain credentials through credential dumping techniques. The attacker then had the permissions to add themselves to a group so they could add the compromised Active Directory user to an Active Directory helpdesk group.
The helpdesk group had the Active Directory permissions to reset other users passwords and at this stage, the attacker could reset a password to another user, preferably an old, out of use admin. Now that they were an admin, they could perform lots of harmful activities in the network, such as running malicious code by adding a script logon to other users in Active Directory.
These are just some relatively simple ways attackers make their way across Active Directory environments. By understanding these actual real-world attack paths, organizations can start to see what their Active Directory and AD Azure environments look like from the attacker’s point of view.
Watch on-demand How To Overcome Active Directory Exploits And Prevent Attacks to learn:
- How Active Directory (AD) exposures combined with other attack techniques form attack paths
- What kind of actions the attacker can perform once they compromise an AD user
- What to do for better Active Directory Security
Conclusion
Looking at attack paths can help shore up these potentially tricky environments. By getting a comprehensive view of the attack paths that exist in Active Directory across on-prem and cloud environments, organizations can learn how attackers move laterally with a context-based understanding of their environment – giving them visibility into how issues can combine to facilitate attacks and impersonate users, escalate privileges, and gain access to cloud environments.
With this understanding, organizations can prioritize what really needs fixing and harden environments to prevent Active Directory weaknesses from being leveraged by threat actors.





